On October 6, 2020, Leo Kelion, a Technology desk editor from BBC, published an article highlighting Pen Test Partners (PTP) research that revealed a critical vulnerability in an Internet-enabled male chastity belt device. How it works is that the device - Qiui's Cellmate Chastity Cage - wirelessly connects to a smartphone using Bluetooth via the Qiui mobile app. Users can use the app to discover other users, similar to a forum or social media platform, and more apposite, allow users to send commands to the device remotely. For users to send commands to another user's device, it must be processed by an intermediary server. PTP security researchers discovered a way to fool this server into disclosing almost everything about any other user's device and sending commands such as lock and unlock actions.
PTP's first exchange with Qiui happened in April 2020, and Qiui subsequently updated the app and fixed the server's API. However, users who didn't update their apps were left vulnerable. Qiui's CEO claimed the issue would create more problems than it fixes, so they accepted the risk. This answer came to the dissatisfaction of PTP researchers, and after multiple attempts to reach decision-makers at Qiui, they posted the vulnerability information to the public, which is where the BBC article comes in.
Apparently, a threat actor noticed this article, researched the vulnerability, and hastily coded a ransomware in Python that exploited it on a mass scale. The source code, downloaded from vx-underground's GitHub repo, shows a script that queries that API, attempts to add all users as friends, and designates the attacker as the "keymaster" of each user's device. The keymaster is the individual who has control of each device on a user's account. In other words, the attacker can remotely control the device's lock and unlock features.
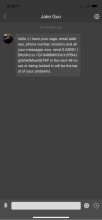
Vx-underground also has pictures of users affected by this attack and some exchanges between them. The attacker impersonated the CEO of the company - Jake Guo. After this, they ran the ransomware script, which immediately gave the attacker access to all devices with outdated mobile apps. The ransom note appeared in the messages on the user's account with a ransom note: "hahaha i have your cock now. send 0.02 BTC (Bitcoin) to [Bitcoin Address] by [Time Limit] or you'll be locked forever".
The user who reported this information claims they weren't using the device when the attack occurred, and two other users reported the same attack. This is how we have three victims listed below. It's uncertain if the attacker managed to lock anyone in their devices. However, - and we're struggling to find the proper adverb here - thankfully, Qiui published a workaround for this issue by taking a flathead screwdriver to the device. Although you can also call their hotline for a manual override. Checking the Bitcoin address provided by the attacker showed that no one paid the 0.02 BTC ransom (about $235 at the time of the attack).
Ransom note pictures derived from vx-underground.
| Industry Sector | País | Extortion Date | Amount (USD) |
|---|---|---|---|
| Individual | 0.02 BTC($235) | ||
| Individual | 0.02 BTC($235) | ||
| Individual | 0.02 BTC($235) |