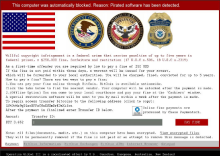
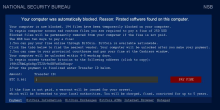
VirLock is also commonly called NSB due to the ransom note portraying the NATIONAL SECURITY BUREAU. Typically, these types of malware are defined as scareware because they trick or "scare" users into thinking that law enforcement is after them, coercing them to download malicious files or pay pseudo-ransoms. However, considering this is also ransomware in that it alters file contents in conjunction with the NSB ransom note, we've labeled it crypto-ransomware. It doesn't stop there, though. This ransomware is also polymorphic because it alters encrypted files to executables that, when run, re-infects the entire system. So, this is crypto-ransomware that is also polymorphic and is also considered scareware because of the mechanisms of the ransom note. Since the ransom note impersonates law enforcement and forces it open, effectively locking the user from the system, it's also labeled as Imitation and Locker ransomware.
Because this ransomware is polymorphic, there are thousands and thousands of samples, and each file it infects is considered a separate sample. Because of this, we've refrained from adding all the hashes we hold, but we've included the most researched samples listed in the References and Publications section. A few variations of VirLock exist, but the differences aren't significant enough to warrant additional entries. They all imitate law enforcement, ask for $250 in Bitcoin, and encrypt files with XOR. VirLock is considered one of the first, if not the very first, widespread polymorphic ransomware, and it still affects users today because of its replicating features. Thus, we anticipate the sample count to constantly increase unless there's a universal fix for its propagation.