GhosHacker, which is seemingly a misspelling of GhostHacker based on the ransom note dropped with the same name—GhostHacker.exe—is a crypto-ransomware built from the NoCry ransomware builder. This allegation comes from the debug string of another similar variant named Anonymous, which shares all of the same characteristics as this ransomware and others such as BlackSkull and AzzaSec. These variants are almost the same, indicating they are all based on NoCry. It appears they all are possibly from the same threat actor(s) based on compilation timelines, ending with AzzaSec, and our theory is that these were test builds of AzzaSec (BlackSkull > GhosHacker > Anonymous > AzzaSec). To see the slightly different characteristics of each, visit the Ransomware Tracker entries for each, linked in this description.
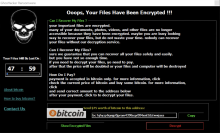
When executed, GhosHacker changes the wallpaper background and creates a process invoking a modal that provides instructions to victims. The files are encrypted with AES, and the applicable files have .red appended to them. The threat actors ask for only $75 in Bitcoin for file decryption but threaten to delete files or increase the extortion price if payment isn't received within a few days. There isn't much more information or references for this ransomware aside from a technical overview from PCrisk.