According to the Albabat Team, this is the stable version of Albabat. To view earlier versions of Albabat (Albabat Beta), please visit the Beta version's entry page. A link to that can be found next to the Lineage variable.
The first appearance of the first official version of Albabat appeared in a self-published video on Dailymotion from the group. In fact, we don't have a sample of this ransomware (yet), and much of the data within was taken from that video. However, we must assume most of the information is the same as the beta version. Including the hybrid encryption type, using a combination of AES to encrypt files and RSA to encrypt the AES symmetric key, and that it's written in Rust. Assuming it's the same operators, we still believe they are based in Portugal based on their ransom note having translation defaulted to Portuguese and their demonstration video showing Portugal as a location. However, we can't confirm this for certain.
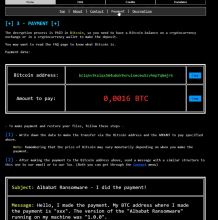
There are a few noticeable differences from the beta version to the stable version that we could tell. The first is that the extortion amount was higher than in the beta versions. In the beta version, we observed 0.00145 and 0.0015 as the extortion amounts. The video of the stable version showed 0.0016 BTC (about $82). Second, they added Tox as a communication method for negotiations. This was previously on email. The most obvious change is the extension appended to encrypted files. Previously, this was 'abbt,' but now it's a generated unique 8 alphanumeric character ID. This ID is used for file decryption and negotiations. The name of the ransom note also reflects this unique ID. Aside from that and a few minor changes to the ransom note HTML file, there were no other noticeable observations.