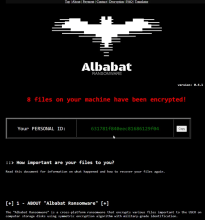
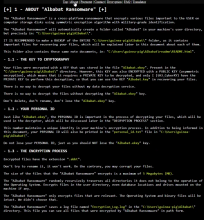
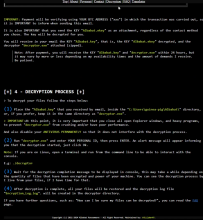
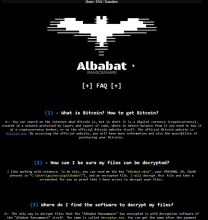
According to the Albabat Team, the beta version of their ransomware are all versions that start with 0 (zero). These variants include versions 0.1.x, 0.3.x, and 0.4.x. Their initial stable version can be found here: Albabat.
The beta versions of Albabat appeared at the beginning of November 2023 and continued to trickle out in the wild for the next few months. That is until the Albabat Team released a video on Dailymotion showcasing their release version - Albabat 1.0.0 - in February 2024. The encryptor is written in Rust, and it drops a granular readme HTML file that gives thorough instructions to the victim of the ransomware. In fact, many of the changes from the different beta versions contained significant changes to the readme file; they certainly took a lot of time. More so than other groups. You can view snippets of the readme HTML file in the ransom note images below. You will also observe an image of the victim's desktop wallpaper, which changes after running the executable. That image is titled 'banner.jpg.'
The Albabat ransomware employs an increasingly ubiquitous encryption method, combining AES to encrypt the files and RSA to encrypt the symmetric key. This means that only the operators possess the private key necessary to decrypt the AES key, making decryption impossible for anyone else. Upon execution, the wallpaper is changed to reflect a White Bat, which is what the operators claim "Albabat" translates to from Latin (which is not true). From there, files are encrypted, and a ransom note is either dropped in the same directory where the file was executed or in the user's root directory, based on which beta version is executed. Encrypted files have the extension 'abbt.' Then, the ransom note appears (or you have to go open it manually), which provides users with contact information, which is email only, and an extortion amount of roughly 0.0015 BTC. These Bitcoin values varied from around $50 to $70, which varies based on the Bitcoin price's expected value on the compilation date.
We can gather a few things based on public information and the ransom note. First, the "About" section in the ransom note states that this is maintained by an individual named "tH3_CyberXY." This individual is the claimed lead developer. Furthermore, their demonstration videos on Dailymotion are signed "Att" by the Albabat Team. There is an individual on GitLab with the same name - tH3CyberXY - who happened to star repositories for CSGO cheat applications, including PPHUD, which is the same name as two of the files: PPHUD.exe. Furthermore, in the demonstration videos, the location at the bottom right is set to "POR," which is Portugal. To further support the theory that at least one of the operators is in Portugal is the fact that there is a Translate section in the HTML ransom note, and the default language is set to Portugal. Due to this, we believe this is an OPSEC failure, and this Att individual is based in Portugal. The other operators could be located there as well.
| Industry Sector | Country | Extortion Date | Amount (USD) |
|---|---|---|---|
| Unknown | Unknown | 0.0015 BTC($59) |