
Related Topics
Drop-In Mode
In a drop-in configuration, your Firebox is configured with the same IP address on all interfaces. The drop-in configuration mode distributes the network’s logical address range across all available network interfaces. You can put your Firebox between the router and the LAN and not have to change the configuration of any local computers. This configuration is known as drop-in mode because your Firebox can be dropped in to a previously configured network.

In drop-in mode:
- The same primary IP address is assigned to all interfaces on your Firebox (external, trusted, optional, and custom).
- You can assign secondary networks on any interface.
- Dynamic routing (OSPF, BGP, or RIP) is not supported.
- Built-in wireless networking on Firebox or XTM wireless devices is not supported (Fireware XTM v11.9 and higher).
- You can keep the same IP addresses and default gateways for hosts on your trusted and optional networks, and add a secondary network address to the primary external interface so your Firebox can correctly send traffic to the hosts on these networks.
- The public servers behind your Firebox can continue to use public IP addresses. Network address translation (NAT) is not used to route traffic from outside your network to your public servers.
- The Firebox cannot route VLAN tagged traffic.
- The Firebox does not support link aggregation.
The properties of a drop-in configuration are:
- You must assign and use a static IP address on the external interface.
- You use one logical network for all interfaces.
- You cannot configure more than one external interface when your Firebox is configured in drop-in mode. Multi-WAN functionality is automatically disabled.
It is sometimes necessary to clear the ARP cache of each computer protected by the Firebox, but this is not common.
If you move an IP address from a computer located behind one interface to a computer located behind a different interface, it can take several minutes before network traffic is sent to the new location. Your Firebox must update its internal routing table before this traffic can pass. Traffic types that are affected include logging, SNMP, and Firebox management connections.
- Select Network > Interfaces.
The Network Interfaces dialog box appears. - From the Configure Interfaces in drop-down list, select Drop-In Mode.
- In the IP Address text box, type the IP address you want to use as the primary address for all interfaces on your Firebox.
- In the Gateway text box, type the IP address of the gateway. This IP address is automatically added to the Related Hosts list.
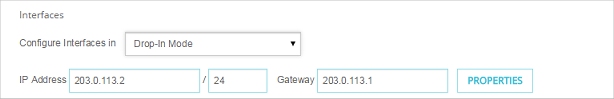
- Click Save.
In the Interfaces page for a device in drop-in mode, you can also select an individual interface to edit the interface settings, such as the interface type, secondary IP addresses, MAC Access Control and other settings.
- Click
 .
.
Or, select Network > Configuration.
The Network Configuration dialog box appears. - From the Configure Interfaces in drop-down list, select Drop-In Mode.
- In the IP Address text box, type the IP address you want to use as the primary address for all interfaces on your Firebox.
- In the Gateway text box, type the IP address of the gateway. This IP address is automatically added to the Related Hosts list.
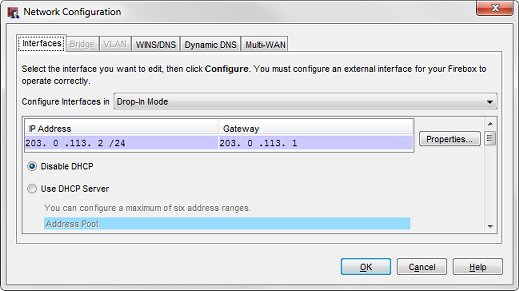
- Click OK.
- Save the Configuration File.
In the Network Configuration dialog box, you can also scroll down to configure settings for each interface, such as the interface type, secondary IP addresses, MAC Access Control and other settings.
See Also
Configure DHCP in Drop-In Mode