
Related Topics
Bridge Mode
Bridge mode is a feature that allows you to install your Firebox between an existing network and its gateway to filter or manage network traffic. When you enable this feature, your Firebox processes and forwards all network traffic to other gateway devices. When the traffic arrives at a gateway from the Firebox, it appears to have been sent from the original device.
System and Management IP Addresses
Fireware v11.12.1 and lower
You must specify a static IP address that is used to manage your Firebox. The Firebox also uses this IP address to receive security services signature updates and to route traffic to internal DNS, NTP, or WebBlocker servers. Because of this, make sure you assign an IP address that has a route to the Internet.
Fireware v11.12.2 and higher
You can specify a static IP address or DHCP.
If you specify DHCP, your Firebox gets a system IP address from the DHCP server configured on your gateway device. The computers on your network can also get DHCP addresses from the gateway device. The Firebox uses the IP address assigned by DHCP to receive security services signature updates and to route traffic to internal DNS, NTP, or WebBlocker servers.
If you specify DHCP, you must also specify a management IP address in a private IP address range. If the DHCP server fails to assign a system IP address to your Firebox, or if you do not know the system IP address, you can connect to the Firebox with the management IP address.
Spanning Tree
In Fireware v11.12.2 and higher, you can enable Spanning Tree Protocol in Bridge mode. Spanning Tree Protocol is designed to prevent loops on networks with redundant links between switches. Administrators who manage networks that must be highly available can configure redundant links and enable Spanning Tree Protocol to help ensure uptime.
For more information about Spanning Tree Protocol, see About Spanning Tree Protocol.
To enable Spanning Tree Protocol, see the Enable Spanning Tree Protocol section.
Disabled Functions
When you use Bridge mode, your Firebox cannot complete some functions that require the device to operate as a gateway. These functions include:
- Multi-WAN
- VLANs (Virtual Local Area Networks)
- Network bridges
- Link aggregation
- Static routes
- FireCluster
- Secondary networks
- DHCP server or DHCP relay
- Modem failover
- 1-to-1, dynamic, or static NAT
- Dynamic routing (OSPF, BGP, or RIP)
- Any type of VPN for which the Firebox is an endpoint or gateway
- Some proxy functions, including HTTP Web Cache Server
- Authentication automatic redirect
- Management of an AP device by the Gateway Wireless Controller
- Mobile Security
- Network Discovery
If you have previously configured these features or services, they are disabled when you switch to bridge mode. To use these features or services again, you must use a different network mode. If you return to drop-in or mixed routing mode, you might have to configure some features again.
Other Information
When you enable Bridge Mode, the Firebox automatically adds a Related Hosts entry for the default gateway configured on interface 0. If the default gateway IP address resides on a different interface, you must change the Related Hosts entry to the correct interface.
To learn more, see Configure Related Hosts.
When you enable bridge mode, any interfaces with a previously configured network bridge or VLAN are disabled. To use those interfaces, you must first change to either drop-in or mixed routing mode, and configure the interface as External, Optional, or Trusted, then return to bridge mode. Wireless features on a wireless Firebox operate correctly in bridge mode.
The LCD display of an XTM device in bridge mode shows the IP address of the bridged interfaces as 0.0.0.0. This is expected behavior.
To use a network bridge on a FireboxV or XTMv virtual machine on ESXi, you must enable promiscuous mode on the attached virtual switch (vSwitch) in VMware. You cannot use a network bridge on a FireboxV or an XTMv virtual machine on Hyper-V, because Hyper-V virtual switches do not support promiscuous mode.
Enable Bridge Mode (Static IP)
- Select Network > Interfaces.
The Network Interfaces page appears. - From the Configure Interfaces In drop-down list, select Bridge Mode.
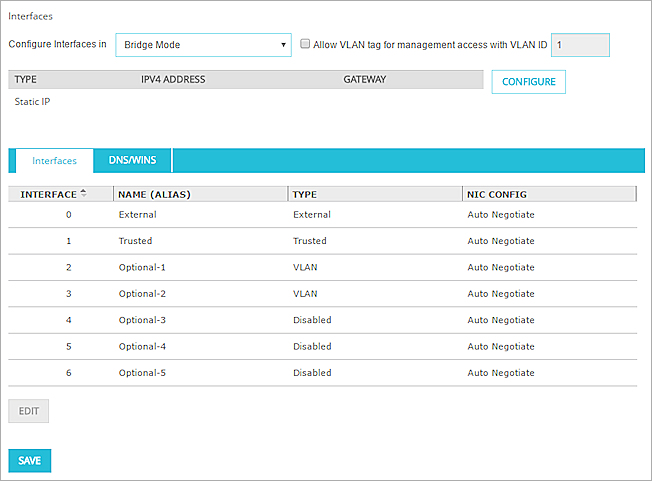
- If you are prompted to disable interfaces, click Yes to disable the interfaces, or No to return to your previous configuration.
- (Fireware v11.12.2 and higher) Click Configure
- Select Static IP.
- In the IP Address text box, type the IP address of your Firebox in slash notation.
For more information on slash notation, see About Slash Notation. - In the Gateway text box, type the Gateway IP address that receives all network traffic from the device.

- Click Save.
- Select Network > Configuration.
The Network Configuration window appears. - From the Configure Interfaces In drop-down list, select Bridge Mode.

- If you are prompted to disable interfaces, click Yes to disable the interfaces, or No to return to your previous configuration.
- (Fireware v11.12.2 and higher) Click Configure
The Bridge Mode Properties window appears. - Select Use Static IP.

- In the IP Address text box, type the IP address of your Firebox in slash notation.
For more information on slash notation, see About Slash Notation. - In the Default Gateway text box, type the Gateway IP address that receives all network traffic from the device.
- Click OK.
Enable Bridge Mode (DHCP)
Before you save the configuration changes described in this section, make sure to record the management IP address so you can connect to the Firebox later.
- Select Network > Interfaces.
The Interfaces page appears. - From the Configure Interfaces In drop-down list, select Bridge Mode.
- If you are prompted to disable interfaces, click Yes to disable the interfaces, or No to return to your previous configuration.
- (Fireware v11.12.2 and higher) Click Configure
The Bridge Mode Properties window appears. - From the Configuration Mode drop-down list, select DHCP.
- In the Management Address section, in the IP Address text box, type an IP address in a private IP address range. Tip!You can use this IP address to connect to the Firebox if DHCP fails, or if you do not know the current System IP Address.

- Click Back.
- Click Save. A dialog box appears that says you must log in to your Firebox with the new management IP address after you continue.
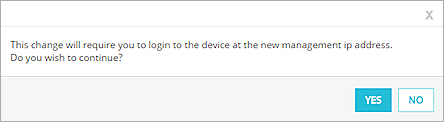
- Click Yes to continue.
- To log in to your Firebox, type the system IP address assigned by DHCP, or the management IP address that you specified.
- Select Network > Configuration.
The Network Configuration window appears. - From the Configure Interfaces In drop-down list, select Bridge Mode.
- If you are prompted to disable interfaces, click Yes to disable the interfaces, or No to return to your previous configuration.
- (Fireware v11.12.2 and higher) Click Configure.
The Bridge Mode Properties window appears. - Select Use DHCP client.
- For Host IP, leave the default option selected, which is Obtain an IP address automatically.
- In the Management Address section, in the IP Address text box, type an IP address in a private range. Tip!You can use this IP address to connect to the Firebox if DHCP fails, or if you do not know the current System IP Address.
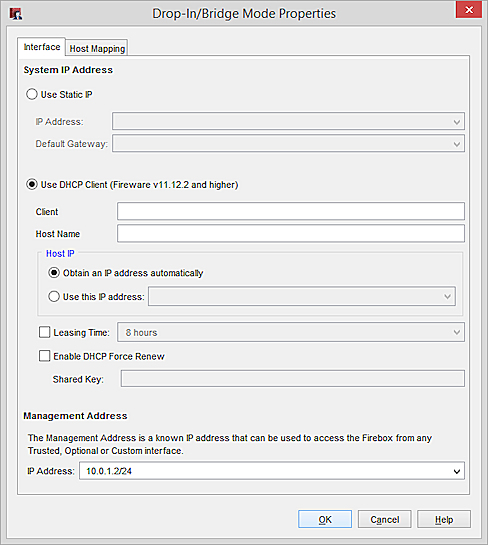
- Click OK.
- To log in to your Firebox after you save the configuration, type the system IP address assigned by DHCP, or the management IP address that you specified.
Enable Spanning Tree Protocol
In Fireware v11.12.2 and higher, you can enable Spanning Tree Protocol. To change the default Spanning Tree Protocol settings, you must use the Fireware command line interface (CLI). For more information about the default Spanning Tree Protocol settings, see Configure Spanning Tree Protocol Settings in the CLI.
To enable Spanning Tree Protocol from the Web UI:
- Select Network > Interfaces.
The Network Configuration page appears. - Select Bridge Protocols.
- Select Enable Spanning Tree Protocol.

- Click OK.
To enable Spanning Tree Protocol from Policy Manager:
- Select Network > Configuration.
The Network Configuration window appears. - Select Bridge Protocols.
- Select Enable Spanning Tree Protocol.
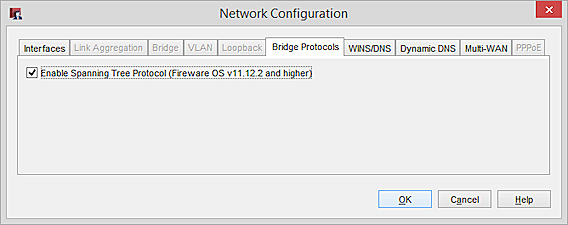
- Click OK.
Allow Management Access from a VLAN
When you configure a Firebox in Bridge mode, you cannot configure VLANs on the Firebox. But the Firebox can pass VLAN tagged traffic between 802.1Q bridges or switches. You can optionally configure the Firebox to be managed from a VLAN that has a specified VLAN tag.
To enable management from a VLAN for a device in bridge mode, from Fireware Web UI:
- Select Network > Interfaces.
The Network Interfaces page appears. - Select the Allow VLAN tag for management access check box.
- Type or select the VLAN ID you want to allow to connect to the device for management access.
To enable management from a VLAN for a device in bridge mode, from Policy Manager:
- Click
 .
.
Or, select Network > Configuration.
The Network Configuration window appears. - Select the Allow VLAN tag for management access check box.
- Type or select the VLAN ID you want to allow to connect to the device for management access.