
Related Topics
About TDR Host Ransomware Prevention
Threat Detection and Response Host Sensors for Windows include Host Ransomware Prevention (HRP), which can identify and quarantine files and stop processes with malicious behavior that is characteristic of ransomware.
HRP Modes
You can enable Host Ransomware Prevention in one of two modes:
- Detect — Host Sensors find processes and files with characteristics of ransomware and sends reports about them to your Threat Detection and Response account for manual intervention.
- Prevent — Host Sensors detect, automatically end processes, and place files with characteristics of ransomware in quarantine before the ransomware encrypts files. Host Sensors send reports about this activity to your Threat Detection and Response account as an indicator that is already mitigated. If the Host Sensor cannot successfully complete the HRP Prevent action, this information is also sent to your TDR account for manual intervention.
A user with Administrator credentials can configure Host Ransomware Prevention mode in the global Host Sensor settings. A user with Operator credentials can configure the Host Ransomware Prevention mode in the Host Sensor settings for a group.
When you enable HRP in Detect or Prevent mode, the Host Sensor creates hidden decoy folders and files on the endpoint. If the user deletes the hidden files, the Host Sensor automatically creates them again the next time it starts.
HRP Actions and Threat Scores
When HRP is configured in Prevent mode, the Host Sensor attempts to take immediate action to kill and quarantine ransomware before it can execute and encrypt files. This action occurs immediately, even if the Host Sensor cannot connect to your TDR account or the Internet.
The next time the Host Sensor connects to your TDR account, it sends a report of the HRP event and information about any actions it took. ThreatSync creates an indicator for the HRP event and assigns a Threat Score.
In Prevent mode:
- If the Host Sensor remediation action succeeded, the HRP incident is assigned a Threat Score of 1 (Remediated)
- If the Host Sensor remediation action failed, the HRP incident is assigned a Threat Score of 10 (Critical)
In Detect mode, all HRP incidents are assigned a Threat Score of 7 (High).
HRP Indicators
Because ransomware can create multiple processes, an HRP indicator can include actions to kill multiple processes or quarantine multiple files related to the detected threat.
To filter the Indicator list to show only HRP indicators:
- Select ThreatSync > Indicators.
- Click
 to clear all filters.
to clear all filters. - At the top of the Indicator column, select Host Ransomware Prevention.
To see a detailed list of all actions and files related to an HRP indicator:
- In the Indicator column for an HRP indicator, click Additional Info.
The Additional Host Ransomware Prevention information dialog box appears.
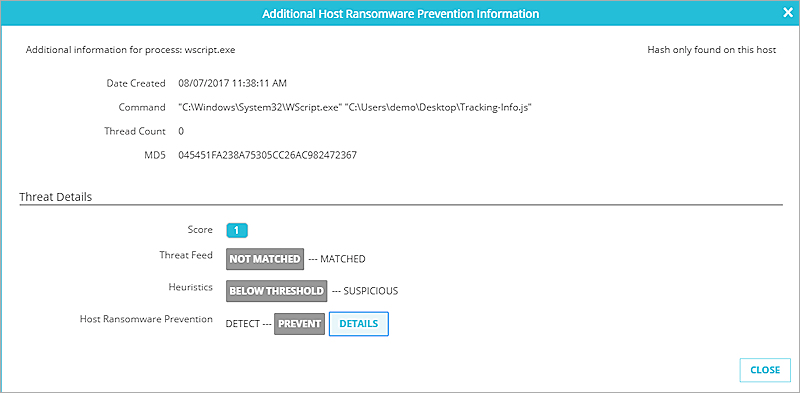
- In the Host Ransomware Prevention section of the threat details, click Details.
The Behavior summary dialog box appears, with a list of actions taken for all files related to the indicator.
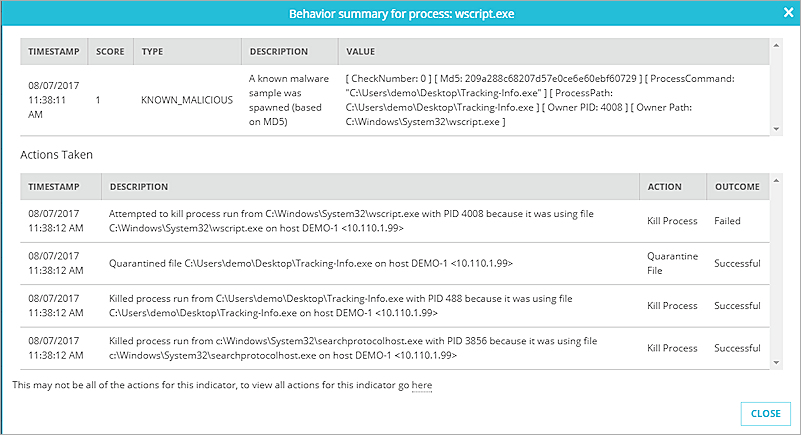
- To see a complete list of actions for the indicator, click the here link at the bottom of the list.
The Action Log for this indicator appears.
For more information about the Indicators page, see Manage TDR Indicators.
HRP Actions and Quarantined Files
The Host Sensor can quarantine one or more files as part of an HRP action. You can see the Quarantine File actions in the details for the HRP indicator, as described in the previous section.
To remove files related to an HRP indicator from quarantine, execute the Unquarantine HRP action for the indicator. For more information, see Remove a File from Quarantine
HRP Actions and the Whitelist
To prevent ransomware, the Host Sensor takes immediate action to kill the process, even before it sends the MD5 to TDR for analysis. This means that if you add the MD5 of a file to the Whitelist, the Host Sensor can still kill the process if it is detected as ransomware.
If you want the Host Sensor to ignore a file, even if it has the characteristics of ransomware, you can add an Exclusion for the directory location. The Host Sensor gets the exclusion list when it starts up, and when the exclusion list is updated. For more information, see Configure TDR Exclusions.