
Related Topics
Recommended TDR Policies
To enable Host Sensors to automatically take action against high severity threats, you must configure TDR policies. Recommended policies are enabled in your TDR account by default. You can modify these policies or add new ones, based on the host groups and the requirements of your network.
For TDR accounts activated prior to 7 August 2017, the default TDR policies are configured, but are not enabled by default.
Default TDR Policies
Each TDR account has three default remediation policies. If you have enabled the APT Blocker feature, a default APT Blocker Policy is also enabled by default.
The three default remediation policies allow Host Sensors to take remediation actions for indicators with different threat scores at Cybercon thresholds of 4, 3, and 2. With the default policies enabled, you can change the Cybercon level (from 3 to 2 for example) to immediately allow Host Sensors to take action on threats with a lower threat score.
The default APT Blocker policy allows Host Sensors to send suspicious files that do not match a known threat to the sandbox for APT Blocker analysis.
- Cybercon Threshold: 4 (applies to Cybercon 4, 3, 2, and 1)
- Allow: the Sandbox File action
- Target: "All Hosts"
- Cybercon Threshold: 2 (applies to Cybercon 2 and 1)
- Threat Score Threshold: 7 (applies to Threat Scores 7 and higher)
- Allow: all remediation actions (Quarantine File, Kill Process, Delete Registry Value)
- Target: "All Hosts"
- Cybercon Threshold: 3 (applies to Cybercon 3, 2, 1)
- Threat Score Threshold: 8 (applies to Threat Scores 8 and higher)
- Allow: all remediation actions (Quarantine File, Kill Process, Delete Registry Value)
- Target: "All Hosts"
- Cybercon Threshold: 4 (applies to Cybercon 4, 3, 2, 1)
- Threat Score Threshold: 9 (applies to Threat Scores 9 and higher)
- Allow: all remediation actions (Quarantine File, Kill Process, Delete Registry Value)
- Target: "All Hosts"
When APT Blocker is enabled, the four default TDR policies look like this:
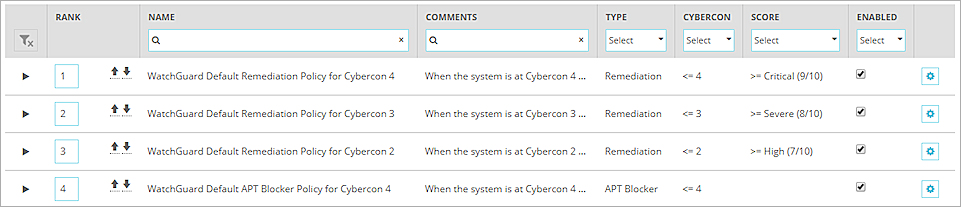
With these default policies, all Host Sensors take these actions:
When the Cybercon level is 4:
- Host Sensors automatically take remediation actions for indicators with a Threat Score of 9 or higher.
- Host Sensors automatically upload suspicious files for analysis in a secure sandbox environment.
When the Cybercon level is 3:
- Host Sensors automatically take remediation actions for indicators with a Threat Score of 8 or higher.
- Host Sensors automatically upload suspicious files for analysis in a secure sandbox environment.
When the Cybercon level is 2 or 1:
- Host Sensors automatically take remediation actions for indicators with a Threat Score of 7 or higher.
- Host Sensors automatically upload suspicious files for analysis in a secure sandbox environment.
Set the Cybercon Level
When you use the default TDR policies you can set the Cybercon level so that the Host Sensors can take automated action to remediate threats based on the active policies at each Cybercon threshold.
- For most deployments, we recommend you set the Cybercon level to 3.
- For a more conservative stance, with less automated remediation, set the Cybercon level to 4.
- For a more aggressive stance, with more automated remediation, set the Cybercon level to 2.
For more information about Cybercon levels, see About TDR Cybercon Levels.
Use Groups as Policy Targets
The default TDR policies are a good place to start for a new TDR account. But it is likely that you might want to configure different policies for different hosts on your network. To create different policies for different groups of hosts, you can specify groups as targets in your policies. You can synchronize groups from your active directory server or you can define TDR groups based on host names or IP addresses. Tip!To add hosts to a group, on the Hosts page select the hosts select the Change Host Group action.
For more information about how to configure Groups, see Manage TDR Groups.
The default group All Hosts includes all hosts that have a Host Sensor installed. We recommend that you create separate groups for clients and servers so that you can create policies specific to these groups.
For example you could add these groups:
- All Clients — Includes all client computers with a Host Sensor installed; does not include servers
- All Servers — Includes all servers with a Host Sensor installed
With these groups, you can configure remediation policies to take automated action for clients at a different threat level than for servers. At the highest threat levels (lowest Cybercon threshold) you can use the All Hosts group so policies to apply to all hosts.
| Example Policy Name | Cybercon Threshold |
Threat Score Threshold |
Policy Target (Group) |
Automated Actions |
|---|---|---|---|---|
| (no policy) | Cybercon 5 | None | ||
| C4 Threat 8 - Clients Only | Cybercon 4 | 8 | All Clients |
- Kill Process |
| C4 - Sandbox All | Cybercon 4 | N/A | All Hosts | - Sandbox File |
| C3 Threat 8 - Servers and Clients | Cybercon 3 | 8 | All Servers All Clients |
- Kill Process |
| C2 Threat 4 - All Hosts | Cybercon 2 | 4 | All Hosts |
- Kill Process |
| C1 - Threat 2 - All Hosts | Cybercon 1 | 2 | All Hosts |
- Kill Process |
Policy Tips
As you configure additional policies, keep these tips in mind:
Use the Cybercon Threshold to activate policies quickly
- With the default policies active, set the Cybercon level to 3.
- Configure no policies for Cybercon 5.
- Add policies for the higher severity (lower number) Cybercon levels.
- You set the Cybercon Threshold for your policies.
- You decide when to change the Cybercon level based on the current activity and risks on your network to activate policies for each Cybercon Threshold.
Use groups for policy targets:
- Configure groups for hosts that have similar requirements; for example, create a group for servers
- Create policies that target that each group
- You can also customize Host Sensor settings per group
For more information, see Manage Hosts In a Group