
Related Topics
Configure TDR Policies
TDR policies define the actions that a Host Sensor can take automatically when it detects a threat. Your TDR account includes default policies with recommended settings. You can edit the default policies and configure additional TDR policies that apply to different hosts and host groups at different Cybercon levels.
For information about the default policies and policy recommendations, see Recommended TDR Policies.
TDR policies are ranked to show their relative priority. TDR evaluates the policies in rank order. More than one TDR policy can apply to the same host at the same time. All active policies for the target are evaluated in rank order to determine which actions a Host Sensor is allowed to perform. If two or more active policies could allow or prevent an action for the same target host, the highest rank (lowest number) policy has priority.
As part of your network security procedures, you define the Cybercon levels to have specific meaning to your organization. After you define the meaning of Cybercon levels, you can configure TDR policies for each level. For more information, see About TDR Cybercon Levels.
TDR Policy Types
In TDR, you can configure two types of policies:
Remediation Policy
A Remediation policy defines actions that Host Sensors can take automatically in response to threats detected on a host.
APT Blocker Policy
An APT Blocker policy defines when Host Sensors can automatically upload suspicious files for analysis in a secure sandbox environment. For more information, see TDR Sandbox Analysis by APT Blocker.
Before you can add an APT Blocker policy you must enable the APT Blocker feature on the General Settings page. For more information, see TDR General Settings.
Policy Rules, Actions, and Targets
For each TDR policy, you configure Rules, Actions, and Targets.
Rules
Rules define when Host Sensors execute the TDR policy. For a Remediation policy you configure two thresholds that control when Host Sensors execute the actions in the policy:
- Cybercon Threshold — The maximum Cybercon level required to execute the policy.
- Threat Score Threshold — The maximum incident Threat Score detected on a host that is required to execute the policy. If the CYBERCON threshold rule is met, the policy applies to new indicators on target hosts when the indicator score is equal to or greater than the threshold enabled in the policy.
For an APT Blocker policy, you configure only a Cybercon Threshold.
Actions
Actions define what the Host Sensor does when the policy executes. For each policy, you define whether the policy allows or denies actions.
- Perform — The policy allows the Host Sensor to perform the specified actions for new indicators that match the policy rules
- Not Perform — The policy does not allow the Host Sensor to perform the specified actions if they are allowed by a lower ranked policy that applies to the same target host. A policy with the Not Perform action does not prevent an operator from manually executing an action.
For a Remediation policy, select one or more of these actions:
- Kill Process — Applies to Process or Host Ransomware Prevention indicators. After the Host Sensor identifies the communication port, the Host Sensor ends the process that supports communication to the network port.
- Quarantine File — XOR encrypts the content of a file identified in an indicator so the file is not executable.
- Delete Registry Value — Deletes the registry value that references a malicious file.
The Kill Process action by itself does not remediate a threat. To automatically remediate threats, we recommend that you allow all actions. For more information, see TDR Remediation Actions and Threat Scores.
For an APT Blocker policy, there is only one action:
Sandbox File — Sends suspicious files to the sandbox for APT Blocker analysis
Targets
Targets define which hosts the action applies to. In each policy, you can add individual hosts or groups of hosts as targets. A policy without a target does not affect any hosts. If you want a policy to apply to all hosts that have a Host Sensor installed, you can use the built-in group All Hosts.
For information about groups, see Manage TDR Groups.
See and Manage Policies
To manage policies:
- Log in to the TDR web UI as a user with Operator credentials.
- Select Configuration > Policy.
The Policy page appears.
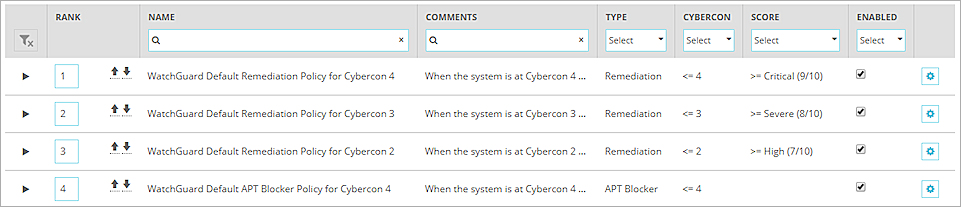
- To search for specific policies, from the filter drop-down lists and in the search text boxes, specify the policy details.
Add a Policy
You can add a combination of Remediation and APT Blocker policies to automatically take action against threats on your network. For information about recommended policies, see Recommended TDR Policies.
- From the Policy page, click Add Policy.
The Select Policy Type setting appears. - Select Remediation Policy.
The settings for a Remediation policy appear.
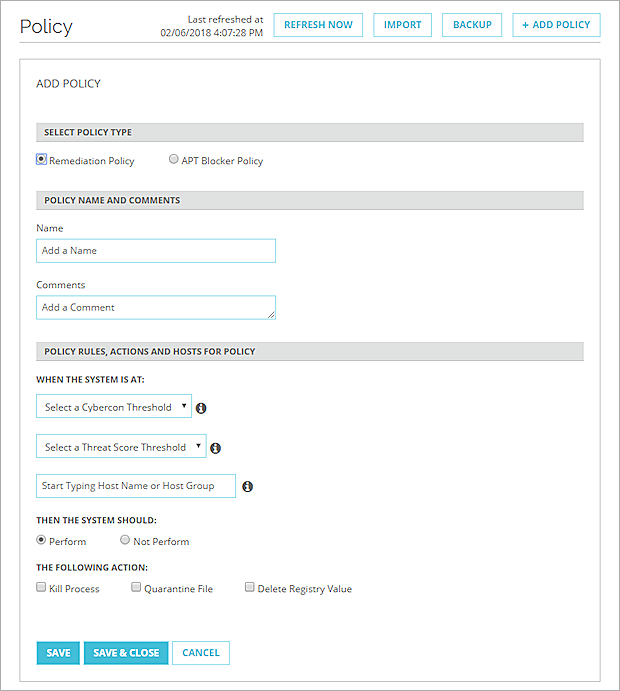
- In the Name text box, type a name for this policy.
- (Optional) In the Comments text box, type other information about the policy.
- From the Select a Cybercon Threshold drop-down list, select the Cybercon level at which you want this policy to execute.
The policy executes only when the Cybercon level is equal to or lower than the value you select here. - From the Select a Threat Score Threshold drop-down list, select the indicator threat score at which you want this policy to execute.
The policy executes for an indicator with a Threat Score equal to or higher than the value you select here. - Select targets for this policy.
- In the Host Name or Host Group text box, type at least three characters from the name of the host or host group to add. Tip!To specify all hosts, type "All Hosts". This is a built-in default group that includes all hosts that have a Host Sensor installed.
Host names and group names that include the characters appear. - Select the host or group name to add.
- To add other targets for this policy, repeat the previous two steps.
- In the Host Name or Host Group text box, type at least three characters from the name of the host or host group to add. Tip!To specify all hosts, type "All Hosts". This is a built-in default group that includes all hosts that have a Host Sensor installed.
- Select an option to specify whether to allow Host Sensors to execute the actions you specify:
- Perform — Allow Host Sensors to perform the specified actions.
- Not Perform — Do not allow Host Sensors to perform the specified actions.
- Select the check box for each action you want this policy to control for the target hosts.
For more information about these actions, see Actions. - Click Save & Close.
- From the Policy page, click Add Policy.
The Select Policy Type setting appears. - Select APT Blocker Policy.
The settings for an APT Blocker policy appear.
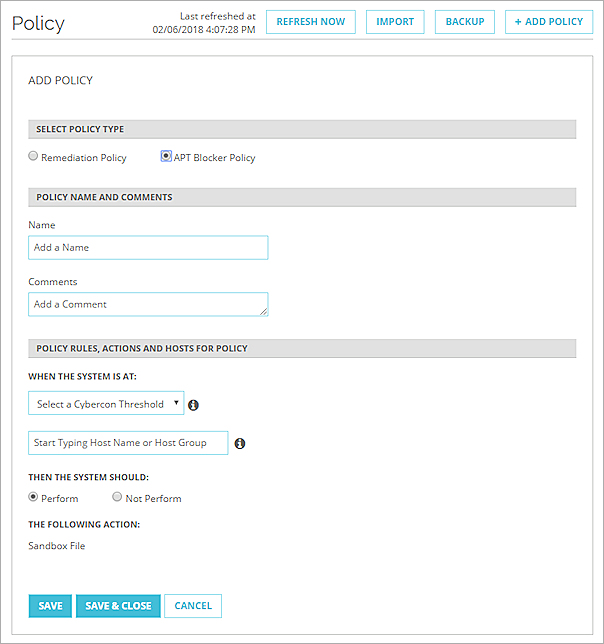
- In the Name text box, type a name for this policy.
- (Optional) In the Comments text box, type other information about the policy.
- From the Select a Cybercon Threshold drop-down list, select the Cybercon level at which you want this policy to execute.
The policy executes only when the Cybercon level is equal to or lower than the value you select here. - Select targets for this policy
- In the Host Name or Host Group text box, type at least three characters from the name of the host or host group to add. Tip!To specify all hosts, type "All Hosts". This is a built-in default group that includes all hosts that have a Host Sensor installed.
Host names and group names that include the characters appear. - Select the host or group name to add.
- To add other targets for this policy, repeat the previous two steps.
- In the Host Name or Host Group text box, type at least three characters from the name of the host or host group to add. Tip!To specify all hosts, type "All Hosts". This is a built-in default group that includes all hosts that have a Host Sensor installed.
- Select an option to specify whether the Host Sensors can execute the Sandbox File action:
- Perform — Allow Host Sensors to perform the Sandbox File action.
- Not Perform — Do not allow Host Sensors to perform the Sandbox File action.
- Click Save & Close.
Change Policy Rank
The Policy page includes all currently defined policies in order of precedence, numbered from the highest rank (1) to the lowest rank. When you add a new policy, it is automatically added to the top of the Policy list, at the highest rank. Policies do not change rank automatically based on the target of the policy. You must manually change the rank of each policy.
For example, if you configure a policy to not perform an action for a single host, and then add a new policy to perform actions for a group that the host is a member of, the policy that you added last (the new policy for the group) has the highest rank and takes precedence. If you want the policy for the single host to take precedence, you must manually change the rank of that policy to a higher position in the list than the policy for the group that host is a member of.
To change the rank of a policy, you can:
- In the Rank column, to increase or decrease the rank of a policy, adjacent to that policy, click
 or
or  .
. - In the Rank column, change the number in the text box.
- Drag-and-drop a policy to a different position in the list .
When you change the rank of a policy, the numbers assigned to all other policies in the list are automatically updated to show their new rank.
Policy Rank and Action Precedence
More than one active TDR policy can apply to the same target host at the same time. This is different from how policy precedence works in Fireware. If multiple active TDR policies apply to the same target host, the action in the highest ranked policy applies for each action. For example if the highest ranked policy for a target specifies that Host Sensors cannot perform the Delete Registry Value action, and a lower ranked policy for the same target allows Host Sensors to perform the Kill Process, Quarantine File, and Delete Registry Value actions, the Host Sensor performs only the Kill Process and Quarantine File actions because the action that specifies that the Host Sensor should not perform the Delete Registry Value action has higher precedence.
Back Up or Import Policies
You can save a backup of all policies to an .XML file. To add the policies to any TDR account, you can import the saved .XML file. This enables a TDR Service Provider to easily copy policies configured in one managed customer account to another managed account. To avoid duplicate policies, the imported policies are merged with the current list of policies.
If the name of a policy in an imported backup file matches the name of an existing policy, the imported policy replaces the existing policy.
To save the policies to a backup file:
- Select Configuration > Policy.
The list of currently configured policies appears. - Click Backup.
The .XML backup file is saved to the downloads folder.
The name of the policy backup file includes the current date and time. For example:
WatchGuardTDR_Policies_2017-01-25_22-39-43.xml
To import policies from a saved policies .XML file:
- Click Import.
- Select and open the saved backup file.
A confirmation dialog box appears. - Click Import.
The policies from the file are added to the Policy list.
Edit, Duplicate, or Remove a Policy
To edit a policy, from the Policy page:
- To expand the details of a policy, click
 .
. - Edit the settings as described in the previous section.
- Click Save & Close.
To duplicate a policy, from the Policy page:
- Adjacent to the policy to duplicate, click
 .
. - Select Duplicate Policy.
To remove a policy, from the Policy page:
- Adjacent to the policy to remove, click
 .
. - Select Remove Policy.