
Related Topics
TDR Sandbox Analysis by APT Blocker
TDR leverages the APT Blocker service to analyze new suspicious files identified by a Host Sensor. The WatchGuard APT Blocker service uses full-system emulation analysis by Lastline to identify the characteristics and behavior of APT malware in files that enter your network. TDR Host Sensors can upload a suspicious file for analysis even if the host is not connected to a network protected by a Firebox. The Sandbox Analysis result is an APT Threat Level assigned to a file. The TDR ThreatSync analytics engine uses the APT Threat Level to determine whether to increase the Threat Score assigned to an indicator.
The sandbox is located at a Lastline cloud-based data center. The sandbox for your TDR account is in the same region where your TDR account data is stored. For example, if your TDR account region is Europe, the sandbox is also in Europe.
Enable APT Blocker
The APT Blocker feature allows Host Sensors to upload files for analysis. You can choose whether to enable or disable this feature. To configure this feature, it must be enabled in your TDR account.
To enable APT Blocker:
- Select Settings > General.
- Adjacent to the APT Blocker feature, select the Feature On check box.
- Click Save.
For more information, see TDR General Settings.
Sandbox File Action
In TDR, the Sandbox File action allows Host Sensors to upload suspicious files for analysis. You can configure an APT Blocker policy to allow this action, or you can select it as a manual action after a Host Sensor requests the Sandbox File action for a file.
If you install Host Sensors behind a Firebox that has an HTTPS proxy policy with content inspection and certification validation enabled, it might be necessary to configure an HTTPS packet filter policy to allow Host Sensors to upload files for analysis. For more information, see Configure a Firewall Policy for TDR Traffic.
A Host Sensor uploads a file to TDR for analysis under these conditions:
- Process or registry heuristics indicate to the Host Sensor that a file is suspicious
- The MD5 value of the file does not match a previously analyzed file
- An active TDR APT Blocker policy or manual TDR action specifies the Sandbox File action
The Sandbox File action can take up to 20 minutes. While the Sandbox File action is in progress, these events occur:
- The Host Sensor uploads the file to the TDR cloud
- TDR sends the file to a secure regional sandbox for analysis
- Lastline executes the file and analyzes the file for threats
- Lastline sends the APT Threat Level result to TDR
- TDR updates the Threat Score associated with the indicator
TDR adjusts the Threat Scores for indicators only if a Host Sensor requests Sandbox Analysis. TDR does not adjust the Threat Score of indicators if a Host Sensor did not request Sandbox Analysis, even if another Host Sensor requested Sandbox Analysis on the same file.
The Host Sensor does not request the Sandbox File action for Host Ransomware Prevention (HRP) events. If HRP is enabled in Prevent mode, when the Host Sensor detects ransomware, it automatically takes action to quarantine the file and end the process. For more information, see About TDR Host Ransomware Prevention.
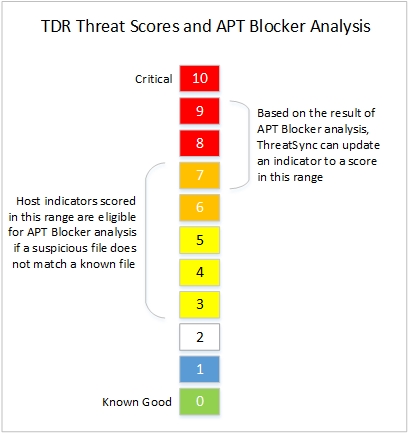
APT Blocker Threat Levels and Indicator Threat Scores
When the suspicious file is first detected, TDR assigns an indicator score based on the heuristics, and requests the Sandbox File action. APT Blocker categorizes APT activity based on the severity of the threat. APT Blocker Threat Levels in TDR are the same as the APT Threat Levels for APT Blocker on a Firebox.
The High, Medium, and Low Threat Levels indicate the severity of malware. This rating is determined based on a score assigned to the file when the file is analyzed by Lastline. For the High, Medium, and Low Threat Levels, TDR increases the indicator Threat Score.
The Clean Threat Level indicates the file was determined to be free of malware. For the Clean Threat Level, TDR does not change the indicator Threat Score.
| APT Blocker Threat Level | TDR Threat Score |
|---|---|
| High | 9 (Critical) |
| Medium | 8 (Severe) |
| Low | 7 (High) |
| Clean | No change |
You can configure a combination of APT Blocker policies and Remediation policies to enable TDR Host Sensors to automatically analyze and respond to emerging threats. For information about recommended policies, see Recommended TDR Policies.
See APT Blocker Sandbox Analysis Status
To see the status of an APT Blocker Sandbox File action for indicators:
- Select Threatsync > Indicators.
- Click
 to clear the filters.
to clear the filters. - In the Action Requested column heading, select the Sandbox File action. Click Apply.
The Indicators list is filtered to show only indicators where the Host Sensor requested the Sandbox File action.

- The Outcome column shows the status of the Sandbox File action for each Host Sensor.
- To see additional information for an indicator, in the Indicator column, click Additional Information.
The Sandbox Analysis status appears in the APT Blocker section of the additional details for an indicator.
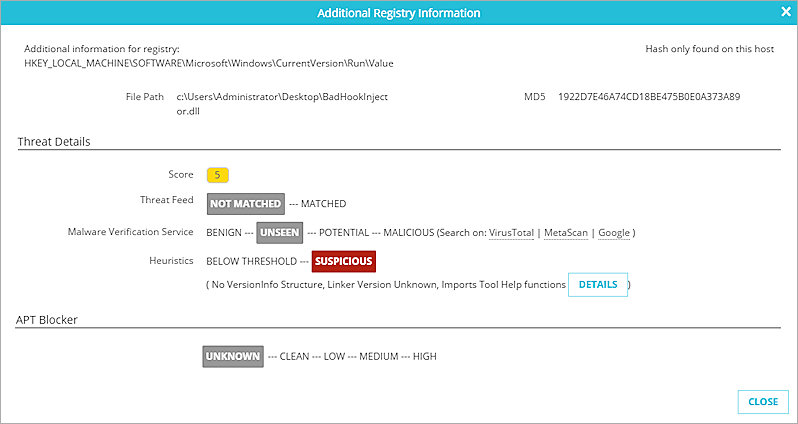
- If Sandbox Analysis is not complete, the APT Blocker status is Unknown. This status appears if the Sandbox File action is in progress or if there is no policy to allow the action.
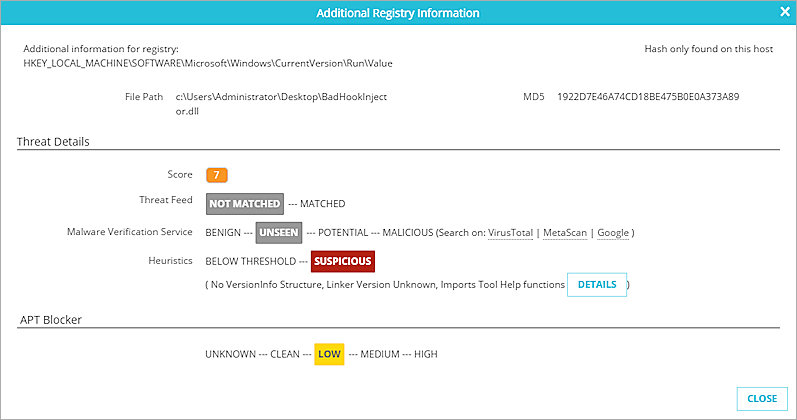
- After Sandbox Analysis is complete, the APT Blocker status indicates the Threat Level. If appropriate, the indicator score is also adjusted based on file analysis.
For more information about how to manage indicators in TDR, see Manage TDR Indicators.