
Related Topics
Enable Firebox Wireless
You can enable up to three wireless access points on a Firebox with built-in wireless capabilities.

A WatchGuard Firebox with built-in wireless capabilities |
Enable Wireless on a Firebox Wireless Device
When you enable the wireless feature of your Firebox wireless device, you can configure the external interface to use wireless, or you can configure the Firebox as a wireless access point for users on specified networks. You can enable wireless clients to connect to the wireless device as part of the trusted network or part of the optional network. You can also use a custom network to enable a wireless guest services network for your device, or use bridge or VLAN networks in your wireless configuration.
Wireless networking on Firebox wireless devices is not supported when the Firebox is configured in Drop-In mode (Fireware OS v11.9 and higher).
Before you set up wireless network access, see Before You Begin.
Before you can enable the wireless feature on your Firebox, you must get the feature key. For more information, see About Feature Keys.
Enable Wireless
You must enable wireless on your Firebox before you can configure wireless access points.
- Select Network > Wireless.
The Wireless page appears.
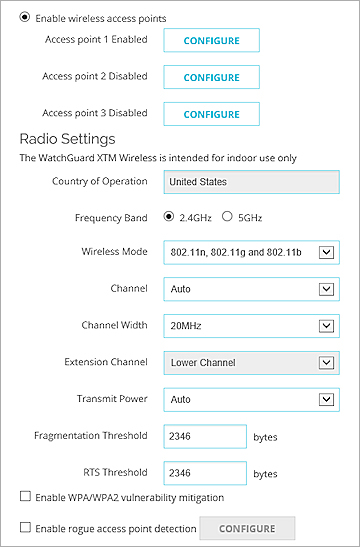
- Select the Enable Wireless check box.
- Select a wireless configuration option:
Enable wireless client as external interface
Select this option to configure the external interface of the Firebox to connect to a wireless network. This is useful in areas with limited or no existing network infrastructure.
For more information, see Configure Your External Interface as a Wireless Interface.
Enable wireless access points
Select this option to configure the Firebox as an access point for users on specified networks.
For more information, see Wireless Device Configuration Options.
- In the Radio Settings section, select your wireless radio settings.
For more information, see About Wireless Radio Settings.
- To mitigate KRACK WPA/WPA2 vulnerabilities in unpatched wireless clients, select the Enable WPA/WPA2 vulnerability mitigation check box.
This option is available in Fireware v12.0.2 and higher and blocks handshake messages that can potentially exploit clients and forces clients to reauthenticate. This re-authentication typically does not require the user to re-enter credentials, but it may add a few seconds to the connection time of the client. This option is disabled by default. This mitigation logic can trigger for other similar dropped packet symptoms, for example, natural frame errors during a handshake, or dropped packets when a client roams. This can result in some client authentication connections to fail and be reestablished. WatchGuard recommends you enable this mitigation feature until you have updated all your client software to address the client vulnerabilities, and evaluate the impact to your client environment and user experience.
- To enable the Firebox to scan for untrusted wireless access points, select the Enable rogue access point detection check box.
For more information, see Enable Rogue Access Point Detection.
- Click Save.
- Select Network > Wireless.
The Wireless Configuration dialog box appears.
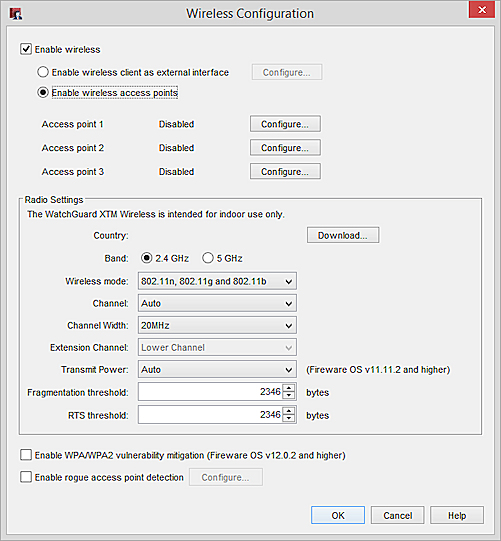
- Select the Enable wireless check box.
- Select a wireless configuration option:
Enable wireless client as external interface
Select this option to configure the external interface of the Firebox wireless device to connect to a wireless network. This is useful in areas with limited or no existing network infrastructure.
For more information, see Configure Your External Interface as a Wireless Interface.
Enable wireless access points
Select this option to configure the Firebox wireless device as an access point for users on specified networks.
For more information, see Wireless Device Configuration Options.
- In the Radio Settings section, select your wireless radio settings.
For more information, see About Wireless Radio Settings.
- To mitigate KRACK WPA/WPA2 vulnerabilities in unpatched wireless clients, select the Enable WPA/WPA2 vulnerability mitigation check box.
This option is available in Fireware v12.0.2 and higher and blocks handshake messages that can potentially exploit clients and forces clients to reauthenticate. This re-authentication typically does not require the user to re-enter credentials, but it may add a few seconds to the connection time of the client. This option is disabled by default. This mitigation logic can trigger for other similar dropped packet symptoms, for example, natural frame errors during a handshake, or dropped packets when a client roams. This can result in some client authentication connections to fail and be reestablished. WatchGuard recommends you enable this mitigation feature until you have updated all your client software to address the client vulnerabilities, and evaluate the impact to your client environment and user experience.
- To enable the device to scan for untrusted wireless access points, select the Enable rogue access point detection check box.
For more information, see Enable Rogue Access Point Detection.
- Click OK.
Enable Wireless to Your Networks
You can enable wireless settings for the trusted, optional, VLAN, bridge, or custom networks. For more information, see Enable Wireless Connections.
Enable a Wireless Guest Network
You can configure any access point as a wireless guest network. For more information, see Enable a Wireless Guest Network.