Applies To: WatchGuard Advanced EPDR, WatchGuard EPDR, WatchGuard EDR,WatchGuard EDR Core, WatchGuard EPP
Configure security settings profiles to define how WatchGuard Endpoint Security protects the workstations and servers on your network against threats, malware, and network attacks.
Settings vary for WatchGuard Advanced EPDR, EPDR, EDR, EDR Core, and EPP. Throughout this documentation, WatchGuard Endpoint Security refers generally to all products. If you do not have a setting in the Endpoint Security management UI, it is not supported by your product.
When you allocate WatchGuard EDR or EDR Core to a new account, and the account does not have a workstations and servers settings profile assigned, the default profile assigned to the All group has anti-exploit and decoy files disabled.
To configure a workstations and servers security settings profile:
- In WatchGuard Cloud, select Configure > Endpoints.
- Select Settings.
- From the left pane, select Workstations and Servers.
- Select an existing security settings profile to edit, copy an existing profile, or in the upper-right corner of the page, click Add to create a new profile.
The Add Settings or Edit Settings page opens.
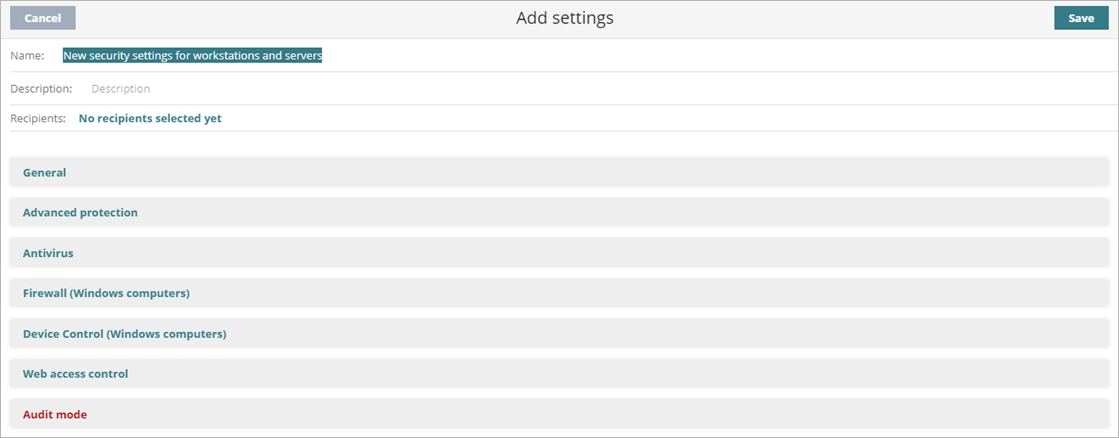
- In the Name text box, type a name for the settings profile.
- (Optional) In the Description text box, type a brief description of the settings profile.
- Select General to configure:
- Local alerts — For more information, go to Configure Local Alerts.
- Updates — For more information, go to Configure Automatic Knowledge (Signature File) Updates.
- Removal of other security products — For more information, go to Automatic Removal of Security Products.
- File and path exclusions from scans — For more information, go to Exclude Files and File Paths from Scans.
We recommend that you only add exclusions for programs that might cause performance issues. When you add an exclusion, Endpoint Security does not scan the specified files and your computers could be at risk of an attack.
- To make sure that Advanced Protection does not block an unclassified program, add it to the Authorized Software list. For more information, go to Configure Authorized Software Settings (Windows Computers).
- To configure the behavior of advanced protection and anti-exploit protection against APTs, targeted attacks, and advanced malware, select Advanced Protection. For more information, go to Advanced Protection.
- To configure parameters that control the antimalware protection against viruses and threats, including decoy files, select Antivirus. For more information, go to Configure Antivirus Scanning.
- To configure parameters that control the firewall and the intrusion detection system against network attacks, select Firewall.
For more information, go to Configure Firewall Settings (Windows Computers). - To configure parameters that control user access to the peripheral devices connected to the computer, select Device Control.
For more information, go to Configure Device Control (Windows Computers). - To restrict access to Web content categories and unknown pages, select Web Access Control. For more information, go to Configure Web Access Control.
- To enable global Audit mode, select Audit mode. For more information, go to Configure Audit Mode.
- Click Save.
- Select the profile and assign recipients, if required.
For more information, go to Assign a Settings Profile.