Applies To: FireCloud Internet Access
FireCloud is a beta product that is only available to participants in the WatchGuard FireCloud Beta program. To try FireCloud Internet Access, join the WatchGuard Beta test community.
To configure FireCloud, you must set up an identity provider. An identity provider is an external system that you use to manage and authenticate your FireCloud users and groups. This is how FireCloud knows which users and groups are authorized, and how the users are authenticated when they connect to FireCloud.
Before You Begin
- To set up AuthPoint as your FireCloud identity provider and require MFA for FireCloud, you must configure AuthPoint as a SAML identity provider.
- You cannot use AuthPoint multi-factor authentication if you configure the WatchGuard Cloud Directory as your identity provider. The WatchGuard Cloud Directory only supports non-MFA users for FireCloud.
Configure an Identity Provider in FireCloud
Before you can configure FireCloud policies, you must set up an identity provider to authenticate your FireCloud users and groups. You can use any identity provider that supports SAML, such as AuthPoint, Microsoft Entra ID (Azure Active Directory), or Okta.
To configure an identity provider in FireCloud:
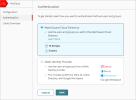
- Log in to WatchGuard Cloud and select Configure > FireCloud.
- Select the type of identity provider to use and enter the required information:WatchGuard Cloud Directory

Use the users and groups you add to the WatchGuard Cloud Directory. The WatchGuard Cloud Directory is an authentication domain where you can add users and groups that are hosted in WatchGuard Cloud. To learn more about the WatchGuard Cloud Directory, and how to add WatchGuard Cloud-hosted users and groups, go to About the WatchGuard Cloud Directory.
This option works best for accounts that do not have an external identity provider, accounts that have a small number of users, and accounts that want to test FireCloud.
If you select this option and have not set up the WatchGuard Cloud Directory, the WatchGuard Cloud Directory is created for you.
When you use the WatchGuard Cloud Directory as your FireCloud identity provider, FireCloud supports only non-MFA users. To use FireCloud with MFA users that you dd to the WatchGuard Cloud Directory, you must set up AuthPoint as a SAML identity provider for FireCloud.
AuthPoint and Third-Party SAML
Use any identity provider that supports SAML, such as AuthPoint or Microsoft Entra ID, to authenticate your users and groups. To configure a SAML identity provider, you must provide this additional information:
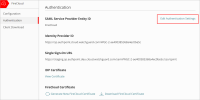
- SAML Service Provider Entity ID — Enter a name to identify FireCloud as your service provider. An entity ID is a unique name for an identity provider or a service provider. After you configure this value for FireCloud, you use this entity ID to configure your identity provider.
- Identity Provider ID — Enter the entity provider ID from your identity provider. Identity providers usually show this value in the UI, but in some cases you might have to download a metadata file and get the value from there. For example, the AuthPoint entity ID would be https://sp.authpoint.cloud.watchguard.com/ACC-1234567 where ACC-1234576 is your WatchGuard Cloud account number.
- Single Sign-On URL — Enter the single sign-on URL for your identity provider. This is usually a URL that contains the identity provider name. For example, the AuthPoint single-sign on URL would be https://sp.authpoint.usa.cloud.watchguard.com/saml/ACC-1234567/sso/spinit, where ACC-1234576 is your WatchGuard Cloud account number.
- IDP Certificate — Paste or upload the x.509 certificate from your identity provider. You can download the certificate from some identity providers, while other identity providers include the certificate as a value in the metadata file.
For AuthPoint, you can find the Identity Provider ID and the Single Sign-On URL in the AuthPoint metadata file. To download the AuthPoint metadata file and the IDP certificate, in WatchGuard Cloud, go to Configure > AuthPoint > Resources > Certificate.
- Click Save.
Provide FireCloud Information to Your Identity Provider (SAML Only)
If you configure a SAML identity provider, FireCloud generates a certificate that you can provide to your identity provider. This certificate gives your identity provider the information required to identify FireCloud and makes sure that your identity provider responds only to valid authentication requests sent by FireCloud. You can download this certificate from the FireCloud Authentication page.
We recommend that you import the FireCloud certificate to your identity provider and enable signature verification.
Your identity provider might have a different name for signature verification. For example, Okta calls this setting SAML Signed Request and Entra ID calls it Verification Certificates.
If you select to use AuthPoint as your identity provider, you must also create a SAML resource in AuthPoint for FireCloud, then add the SAML resource to your existing AuthPoint authentication policies or add new AuthPoint authentications policies for the SAML resource.
- On the FireCloud Authentication page, click Download FireCloud Certificate. You use this certificate when you configure a SAML resource in AuthPoint. You also use the SAML Service Provider Entity ID value.
- Select Configure > AuthPoint > Resources.
- Click Add Resource.
- From the Type drop-down list, select SAML.
- Enter a name for your resource, such as FireCloud.
- From the Application Type drop-down list, select Others.
- In the Service Provider Entity ID text box, enter the SAML Service Provider Entity ID that you set in Configure an Identity Provider in FireCloud.
- In the Assertion Consumer Service text box, enter the ACS value for your FireCloud account based on your WatchGuard Cloud account region.
- North America / Americas — https://authsvc.firecloud.usa.cloud.watchguard.com/v1/acs
- EMEA — https://authsvc.firecloud.deu.cloud.watchguard.com/v1/acs
- APAC — https://authsvc.firecloud.jpn.cloud.watchguard.com/v1/acs
- From the User ID Sent on Redirection to Service Provider drop-down list, select User Name.
- For the certificate, upload your FireCloud certificate.
- From the AuthPoint Certificate drop-down list, select the AuthPoint certificate to associate with your resource. You must select the same certificate that you downloaded the metadata and x.509 certificate from.
- Click Add Attribute.
- In the Attribute Name text box, type groups. This value is case-sensitive.
- From the Get Value From drop-down list, select User Groups.
- Click Save.
AuthPoint saves your custom attribute. - Click Save.
AuthPoint creates your SAML resource. - On the Policies page in AuthPoint, add a new AuthPoint authentication policy for this resource, or add it to your existing authentication policies. For more information, go to About AuthPoint Authentication Policies.
- To allow users to connect to FireCloud with only their password, your AuthPoint authentication policy must require only the password authentication option.
- To require users to authenticate with MFA when they connect to FireCloud, your AuthPoint authentication policy must require the push, QR code, or OTP authentication options in addition to the password authentication option.
Control Access to FireCloud
If you connected FireCloud to an identity provider that has more users than will use FireCloud, you can control access to FireCloud so that only some users can connect to the service and consume a user license. To do this, you disable the default FireCloud access rule and configure access rules for only the user groups that you want to have access to FireCloud. Users that do not have an access rule cannot connect to the FireCloud service and consume a license.
You can also provide the FireCloud connection manager to only the end-users that you want to use the service.
Edit FireCloud Authentication Settings or Change Identity Provider
If you change your FireCloud identity provider, FireCloud deletes all your access rules because they no longer have any groups associated with them. FireCloud prompts you for confirmation before this happens.
The default access rule is not affected.
To edit the settings for your identity provider, or to change to a new identity provider, from WatchGuard Cloud:
- Select Configure > FireCloud.
- From the navigation menu, select Authentication.
- Click Edit Authentication Settings.
- Make your changes, then click Save.