Applies To: FireCloud Internet Access
FireCloud is a beta product that is only available to participants in the WatchGuard FireCloud Beta program. To try FireCloud Internet Access, join the WatchGuard Beta test community.
This quick start topic reviews the general steps to configure and test FireCloud. This guide introduces FireCloud, reviews the basic components of FireCloud, and helps you get set up.
FireCloud is a fully-managed, cloud-based firewall-as a-service that protects your remote users against Internet-based security threats. You configure FireCloud in WatchGuard Cloud, and users connect to the service with the WatchGuard connection manager. While the users are connected to FireCloud, they are protected and can safely use their computer and browse the Internet.
Here is a high level overview of the steps in this quick start guide:
- Enable the FireCloud beta toggle.
- Activate a FireCloud license or start a trial.
- Configure FireCloud authentication settings.
- Review the default settings.
- Download and install the connection manager.
- Connect to FireCloud with the connection manager.
- (Optional - Service Providers Only) Create and deploy FireCloud templates.
Before you begin, we recommend that you familiarize yourself with these key terms related to FireCloud:
WatchGuard Cloud
WatchGuard Cloud is the platform where you configure, manage, and monitor FireCloud. There are two types of WatchGuard Cloud accounts — Subscriber and Service Provider. Each account type has a different view of WatchGuard Cloud. To learn more, go to About WatchGuard Cloud Account Types.
For Service Providers, the procedures in this quick start guide require additional steps.
Inventory and Allocation
Users purchased by a Service Provider account are stored in your inventory in WatchGuard Cloud. As a Service Provider, you can allocate users to your own account or any account you manage. User allocation is how Service Providers provision an account with licensed users for a security service such as FireCloud.
WatchGuard Connection Manager
The connection manager is an application that you install on end-user computers. Users use the connection manager to connect to FireCloud.
WatchGuard Agent
The WatchGuard Agent handles communication between managed computers on the same network and the WatchGuard server. The agent is installed on each endpoint or computer, and is used to deploy WatchGuard software, such as the WatchGuard connection manager and Endpoint Security software. It has low CPU, memory, and bandwidth usage and uses less than 2 MB of data each day.
When you download the installer from the FireCloud UI, you are downloading the WatchGuard Agent.
Identity Provider
An identity provider is the external database with your users and groups. This is how FireCloud knows what users and groups are authorized, and how the users are authenticated when they connect to FireCloud. You can use any identity provider that supports SAML, such as Okta, Microsoft Entra ID (Azure Active Directory), or AuthPoint.
Directories and Domain Services
Directories and Domain Services is a WatchGuard Cloud feature that enables you to sync external users, groups, and devices to WatchGuard Cloud. You can also add WatchGuard Cloud-hosted users and groups to the WatchGuard Cloud Directory. You can then use the users, groups, and devices in Directories and Domain Services with products such as FireCloud.
For FireCloud, you can use your existing authentication servers from Directories and Domain services, such as the WatchGuard Cloud Directory, to authenticate your FireCloud users and groups instead of using an identity provider.
Enable the FireCloud Beta Toggle
To get started, you must enable the FireCloud beta toggle for your account.
To enable the FireCloud beta toggle:
- Go to cloud.watchguard.com and log in.
- If you have a Service Provider account, select an account from Account Manager.
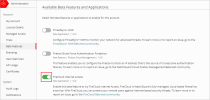
- Select Administration > Beta Features.
The Beta Features page opens. - Enable the FireCloud Internet Access beta toggle.
Activate a FireCloud License or Start a Trial
Before you begin, you must purchase and activate a FireCloud license or start a FireCloud trial.
If you have not already purchased a FireCloud license, we recommend that you start a free FireCloud trial in WatchGuard Cloud. For detailed steps to start a trial, go to Manage Trials – Service Providers or Manage Trials – Subscribers. All trial licenses are valid for 30 days, and can be renewed for another 30 days to a maximum of 60 days.
We recommend that you extend your trial now to get the full 60 days. You can only extend the trial once within 30 days of the trial start date, and only before the trial expires.
If you have a WatchGuard Cloud Service Provider account and want to use FireCloud for your own account, after you activate a FireCloud license you must allocate the users to your Subscriber account. For detailed steps, go to Allocate FireCloud Users.
Configure Authentication Settings
Before you can configure FireCloud, you must set up an identity provider. An identity provider is an external system that you use to manage and authenticate your FireCloud users and groups. This is how FireCloud knows what users and groups are authorized, and how the users are authenticated when they connect to FireCloud.
Configure an Identity Provider
To configure an identity provider for FireCloud:
- Log in to WatchGuard Cloud and select Configure > FireCloud.
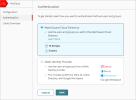
- Select the type of identity provider to use and enter the required information:WatchGuard Cloud Directory

Use the users and groups you add to the WatchGuard Cloud Directory. The WatchGuard Cloud Directory is an authentication domain where you can add users and groups that are hosted in WatchGuard Cloud. To learn more about the WatchGuard Cloud Directory, and how to add WatchGuard Cloud-hosted users and groups, go to About the WatchGuard Cloud Directory.
This option is best for accounts that do not have an external identity provider, accounts that have only a few users, and accounts that want to test FireCloud.
If you select this option and have not set up the WatchGuard Cloud Directory, the WatchGuard Cloud Directory is configured for you.
When you use the WatchGuard Cloud Directory as your FireCloud identity provider, FireCloud supports only non-MFA users. To use FireCloud with MFA users that you have added to the WatchGuard Cloud Directory, you must set up AuthPoint as a SAML identity provider for FireCloud.
AuthPoint and Third-Party SAML
Use any identity provider that supports SAML, such as AuthPoint or Microsoft Entra ID, to authenticate your users and groups. To configure a SAML identity provider, you must provide additional information:
- SAML Service Provider Entity ID — Enter a name to identify FireCloud as your service provider. An entity ID is a unique name for an identity provider or a service provider. After you configure this value for FireCloud, you use this entity ID to configure your identity provider.
- Identity Provider ID — Enter the entity provider ID from your identity provider. Identity providers usually show this value in the UI, but in some cases you might have to download a metadata file and get the value from there. For example, the AuthPoint entity ID would be https://sp.authpoint.cloud.watchguard.com/ACC-1234567 where ACC-1234576 is your WatchGuard Cloud account number.
- Single Sign-On URL — Enter the single sign-on URL for your identity provider. This is usually a URL that contains the identity provider name. For example, the AuthPoint single-sign on URL would be https://sp.authpoint.usa.cloud.watchguard.com/saml/ACC-1234567/sso/spinit, where ACC-1234576 is your WatchGuard Cloud account number. You can find the AuthPoint single sign-on URL in the SAML metadata file.
- IDP Certificate — Paste or upload the x.509 certificate from your identity provider. You can download the certificate from some identity providers, while other identity providers include the certificate as a value in the metadata file.
For AuthPoint, you can find the Identity Provider ID and the Single Sign-On URL in the AuthPoint metadata file. To download the AuthPoint metadata certificate and the IDP certificate, in WatchGuard Cloud, go to Configure > AuthPoint > Resources > Certificate.
- Click Save.
You only have to configure an identity provider the first time you set up FireCloud. To edit the settings for your identity provider, or change to a new identity provider, go to the Configure > FireCloud > Authentication.
Provide FireCloud Information to Your Identity Provider (SAML Only)
If you configure a SAML identity provider, FireCloud generates a certificate that you can provide to your identity provider. This certificate gives your identity provider the information to identify FireCloud and makes sure that your identity provider responds only to valid authentication requests sent by FireCloud. You can download this certificate from the FireCloud Authentication page.
We recommend that you import the FireCloud certificate to your identity provider and enable signature verification.
Your identity provider might have a different name for signature verification. For example, Okta calls this setting SAML Signed Request and Entra ID calls it Verification Certificates.
If you select to use AuthPoint as your identity provider, you must also create a SAML resource in AuthPoint for FireCloud, and you must add the SAML resource to your existing authentication policies or add new authentications policies for the SAML resource.
- On the FireCloud Authentication page, click Download FireCloud Certificate. You use this certificate when you configure a SAML resource in AuthPoint. You also use the SAML Service Provider Entity ID value.
- Select Configure > AuthPoint > Resources.
- Click Add Resource.
- From the Type drop-down list, select SAML.
- Enter a name for your resource, such as FireCloud.
- From the Application Type drop-down list, select Others.
- In the Service Provider Entity ID text box, enter the SAML Service Provider Entity ID that you specified in Configure an Identity Provider in FireCloud.
- In the Assertion Consumer Service text box, enter the ACS value for your FireCloud account, based on your WatchGuard Cloud account region.
- North America / Americas — https://authsvc.firecloud.usa.cloud.watchguard.com/v1/acs
- EMEA — https://authsvc.firecloud.deu.cloud.watchguard.com/v1/acs
- APAC — https://authsvc.firecloud.jpn.cloud.watchguard.com/v1/acs
- From the User ID Sent on Redirection to Service Provider drop-down list, select User Name.
- For the certificate, upload your FireCloud certificate.
- From the AuthPoint Certificate drop-down list, select the AuthPoint certificate to associate with your resource. You must select the same certificate that you downloaded the metadata and x.509 certificate from.
- Click Add Attribute.
- In the Attribute Name text box, type groups. This value is case-sensitive.
- From the Get Value From drop-down list, select User Groups.
- Click Save.
AuthPoint saves your custom attribute. - Click Save.
AuthPoint creates your SAML resource. - On the Policies page in AuthPoint, add a new AuthPoint authentication policy for this resource, or add the resource to your existing authentication policies. For more information, go to About AuthPoint Authentication Policies.
- To allow users to connect to FireCloud with only their password, your AuthPoint authentication policy must require only the password authentication option.
- To require users to authenticate with MFA when they connect to FireCloud, your AuthPoint authentication policy must require the push, QR code, or OTP authentication options in addition to the password authentication option.
Control Access to FireCloud
If you have connected FireCloud to an identity provider that has more users than will actually use FireCloud, you can control access to FireCloud so that only some users can connect to the service and consume a user license. To do this, you can disable the default FireCloud access rule and configure access rules for only the user groups that you want to have access to FireCloud. Users that do not have an access rule cannot connect to the FireCloud service and consume a license. For more information, go to FireCloud Access Rules.
You can also provide the FireCloud connection manager to only the end-users that you want to use the service.
Review the Default Settings
By default, FireCloud has all security services enabled with default configurations, and a default access rule is in place to specify which security services apply to user traffic. This means that you can deploy and use FireCloud immediately, but we recommend that you review the default settings.
Scanning engines protect against spyware, viruses, malicious applications, spam email, and data leakage. Content scanning services are enabled by default with recommended settings. For content scanning to apply to traffic, you must also enable content scanning in FireCloud access rules.
With FireCloud, you can enable content scanning with these services:
Gateway AntiVirus
Gateway AntiVirus protects your users from viruses. You can configure the action Gateway AntiVirus takes when a virus is detected, an error occurs, scanned content exceeds the configured size limit, or scanned content is encrypted.
APT Blocker
An Advanced Persistent Threat (APT) attack is a type of network attack that uses advanced malware and zero-day exploits to get access to networks and confidential data over extended periods of time. APT Blocker identifies the characteristics and behavior of APT malware in files and email attachments that enter your network. You can configure the action APT Blocker takes for each threat level (High, Medium, Low).
You can use FireCloud to monitor and block common security threats, such as botnets, spyware, SQL injections, cross-site scripting, and buffer overflows. FireCloud network blocking security services are enabled by default, with recommended settings.
Botnet Detection
A botnet comprises a large number of malware-infected client computers that a remote server controls and uses to perform malicious acts. The Botnet Detection security service adds a list of known botnet site IP addresses to the FireCloud Blocked Sites List, which enables FireCloud to block these sites at the packet level.
Intrusion Prevention Service
Intrusion Prevention Service (IPS) uses signatures to provide real-time protection against network attacks, including spyware, SQL injections, cross-site scripting, and buffer overflows. Configure the action IPS takes when it detects a threat, as well as the type of scan.
To learn how to configure network blocking, go to Configure Network Blocking in FireCloud.
Geolocation is a security service that enables FireCloud to detect the geographic locations of connections to and from your devices. With FireCloud, you can enable and configure Geolocation to block access to and from specific locations.
The default Geolocation action does not block any countries.
To learn how to configure Geolocation actions, go to Add Geolocation Actions in FireCloud.
Content filtering uses the WebBlocker and Application Control security services to block specific content categories and applications. Content filtering security services are enabled by default with recommended settings.
WebBlocker
WebBlocker helps you control which websites are available to your users. WebBlocker uses a database that groups website addresses into content categories. When a user tries to connect to a website, FireCloud looks up the address in the WebBlocker database and takes the action you specify for the content category.
Application Control
Application Control enables you to monitor and control the use of applications by your users. You can use Application Control to block the use of specific applications, and you can report on application use and use attempts.
To learn how to configure content filtering, go to Content Filtering in FireCloud.
A FireCloud access rule is a policy that determines when FireCloud allows or denies connections. FireCloud matches each connection to an access rule based on the user groups that the user belongs to. You can configure which security services apply to the traffic each access rule handles.
FireCloud has a Default access rule that applies to all connections. The Default access rule has all security services enabled with the default configurations. You cannot edit or delete the Default access rule.
If you do not want to use the Default access rule, you can disable it. If the Default access rule is disabled and a user connection does not match any other access rules, the connection is denied.
To learn more about FireCloud access rules, go toFireCloud Access Rules.
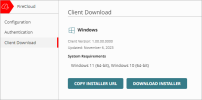
Download and Install the WatchGuard Connection Manager
For FireCloud to protect your users, they must have the WatchGuard Connection Manager installed on their device and use it to connect to FireCloud.
To download the WatchGuard Agent, used to install the WatchGuard Connection Manager:
- Log in to WatchGuard Cloud and go to Configure > FireCloud.
- Select Client Download.
The Client Download page opens.
- Click Download Installer.
The WatchGuard Agent installer download begins. - Run the downloaded installer.
- Click Install.
- When the installation is complete, click Finish.
After the WatchGuard Agent is installed, the agent automatically downloads and installs the Connection Manager. When this is finished, the Connection Manager opens and you are prompted to enter your credentials to connect to FireCloud. You use the credentials for the user account in your identity provider.
Connect to FireCloud with the Connection Manager
While you are connected to FireCloud, you are protected and can safely use your computer and browse the Internet. After you connect to FireCloud for the first time, the agent keeps your session open and you remain connected even if you restart your computer.
If you disconnect from FireCloud, you must manually log in and connect again.
To connect to FireCloud:
- Open the WatchGuard Connection Manager.
- From the system tray, click the WatchGuard Connection Manager, then select Connect.
- Enter your user name or email address, then click Next.
- Enter your password.
You see a success message when you are connected to FireCloud. - Click Log In.
Create and Deploy FireCloud Templates (Optional — Service Providers Only)
For Service Providers, FireCloud templates provide a way to manage shared configuration settings for multiple accounts. In a FireCloud template, you can configure FireCloud access rules and services just as you would for your FireCloud account. You can then subscribe your managed accounts to the template so that those accounts inherit configuration settings from the template.
To learn more about FireCloud templates, go to About FireCloud Templates and Manage FireCloud Templates.