BOVPN Virtual Interface for Dynamic Routing to Microsoft Azure
You can configure static or dynamic routing. This topic covers dynamic routing. For information about static routing, go to BOVPN Virtual Interface for Static Routing to Microsoft Azure.
In this example, we show a VPN configuration with:
- Dynamic BGP routing. Azure supports the BGP dynamic routing protocol. OSPF is not supported.
- One Firebox external physical interface
- One Firebox BOVPN virtual interface with one gateway endpoint. A BOVPN virtual interface configured with multiple gateway endpoints is not supported for connections to Azure.
- One Azure gateway
To configure dynamic routing with BGP between a Firebox and Microsoft Azure, you must understand Microsoft PowerShell, a command line tool and scripting environment.
Configure Azure
To configure your Azure virtual network:
- Connect to the Azure Management Portal at https://portal.azure.com.
- Review the Microsoft documentation: Get started with Azure and Azure VPN Gateway Documentation.
In our example, we use these Microsoft Azure virtual network settings:
- Remote gateway — 203.0.113.2 (the IP address of the external interface on the Firebox). Azure does not support VPN connections to Fireboxes behind NAT devices. The Firebox must have a public external IP address.
- Local gateway — 198.51.100.2 (the IP address of the external interface on the Azure gateway)
- BGP ASN — 10001 (the BGP ASN of the Firebox)
You must use Microsoft PowerShell to configure BGP settings on your Microsoft Azure virtual network. For more information about PowerShell, see the documentation provided by Microsoft. - Virtual IP address — 100.100.100.1 (the virtual IP address of the Firebox)
- VPN type — Policy-based
- Shared key — The key automatically generated by Azure. Azure supports only the pre-shared key authentication method for site-to-site VPNs.
For the most recent list of protocols and algorithms supported by Microsoft for VPNs, go to About VPN devices and IPSec/IKE parameters for Site-to-Site VPN Gateway connections on the Microsoft website.
MTU Settings
For Azure VPN connections, Microsoft requires a maximum TCP MSS of 1350 or MTU of 1400. The Azure VPN gateway drops packets with a total packet size larger than 1400.
If the Azure VPN gateway drops packets from your Firebox, we recommend these Firebox settings:
- Fireware v12.5 or higher — In the BOVPN virtual interface configuration, specify an MTU of 1400. For more information about the MTU setting, go to Configure a Maximum Transmission Unit (MTU) Value.
- Fireware v12.4.1 or lower — In the physical interface configuration, specify an MTU of 1400.
As an alternative, you can set the global TCP MSS value to 1350. However, we do not recommend this option because this setting affects other Firebox interfaces and applies only to TCP traffic. For example, this setting does not apply to RDP traffic in most cases because RDP usually uses UDP. If you use RDP to access servers hosted in Azure, Azure will drop packets larger than 1400 bytes even if you specify the recommended TCP MSS value. For more information about the TCP MSS setting, go to Define Firebox Global Settings.
Configure the Firebox
For this example, the Firebox has one external interface and one trusted network.
Azure does not support VPN connections to Fireboxes behind NAT devices. The Firebox must have a public external IP address.
| Interface | Type | Name | IP Address |
|---|---|---|---|
| 0 | External | External | 203.0.113.2/24 |
| 1 | Trusted | Trusted | 10.0.1.1/24 |
To configure the Firebox, you must configure:
- Select VPN > BOVPN Virtual Interfaces.
The BOVPN Virtual Interfaces page opens. - Click Add.
- In the Interface Name text box, type a name to identify this gateway.
- From the Remote Endpoint Type drop-down list, select Cloud VPN or Third-Party Gateway.
- In the Use Pre-Shared Key text box, paste the auto-generated shared key you copied from the Azure Management Portal.
For site-to-site VPNs, Azure supports only the pre-shared key authentication method. - In the Gateway Endpoint section, click Add.
The Gateway Endpoint Settings dialog box opens. - Select the Local Gateway tab.
- From the Physical drop-down list, select an external interface.
- From the Interface IP Address drop-down list, select Primary Interface IPv4 Address.
- In the By IP Address text box, type the external IP address of your Firebox. In our example, we use 203.0.113.2.
- Select the Remote Gateway tab.
- In the Static IP Address text box, type the IP address of the Azure gateway. In our example, we use 198.51.100.2.
- In the By IP Address text box, type the gateway ID of the Azure gateway. In our example, we use 198.51.100.2.

- Click OK.
- Select the VPN Routes tab.
- In the Local IP Address text box, type the local IP address of the Azure resource to which you want to connect. In our example, we use 100.100.100.1.
- In the Peer IP address or netmask text box, type the Azure virtual interface IP address, not the netmask. The Azure virtual interface IP address is defined by Azure. In our example, we use 172.20.2.254.

- Select the Phase 1 Settings tab.
- From the Version drop-down list, select IKEv2. Static VPN routes between your Firebox and Azure require IKEv2.
- In the Transform Settings section, select the default transform.
- Click Edit.
- From the Authentication drop-down list, keep the default value of SHA2-256 or select another option that Microsoft Azure supports for Phase 1.
- From the Encryption drop-down list, keep the default value of AES(256-bit) or select another option that Microsoft Azure supports or Phase 1.
- In the SA Life text box, type 8.
- From the Key Group drop-down list, select a Diffie-Hellman group that Microsoft Azure supports for Phase 1.
For information about Microsoft cryptographic requirements, go to About VPN devices and IPsec/IKE parameters for Site-to-Site VPN Gateway connections and About cryptographic requirements and Azure VPN gateways in the Microsoft documentation.
The default Key Group setting is Diffie-Hellman Group 14.

- Select the Phase 2 Settings tab.
- Select Enable Perfect Forward Secrecy.
- From the Diffie-Hellman drop-down list, select a Diffie-Hellman group that Microsoft Azure supports for Phase 2.
For information about Microsoft cryptographic requirements, go to About VPN devices and IPsec/IKE parameters for Site-to-Site VPN Gateway connections and About cryptographic requirements and Azure VPN gateways in the Microsoft documentation. - In the IPSec Proposals section, make sure the proposals ESP-AES256-SHA256 or ESP-AES256-GCM appear. Azure does not support AES128-GCM or AES192-GCM. To add a proposal, click Add.
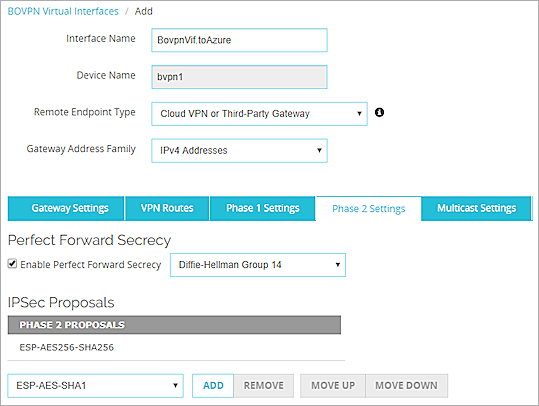
- Click OK.
- Click Save.
The Firebox automatically adds the policies BOVPN-Allow.out and BOVPN-Allow.in to your configuration.
The Azure BGP ASN and the virtual IP address (known as the bgpPeeringAddress in Azure) are defined by Azure and cannot be changed. You can use Microsoft PowerShell to see the Azure BGP ASN and bgpPeeringAddress. The Firebox BGP dynamic routing configuration has these commands:
!
! The local BGP ASN is 10001
!
router bgp 10001
!
! to Azure VPC
!
!
! The Azure (remote) BGP ASN is 65515 and its VIF IP (bgpPeeringAddress) is 172.20.2.254.
! These are the two parameters you must get from the Azure side.
!
neighbor 172.20.2.254 remote-as 65515
neighbor 172.20.2.254 activate
neighbor 172.20.2.254 ebgp-multihop
!
! To advertise the local networks
!
network 10.0.1.0/24
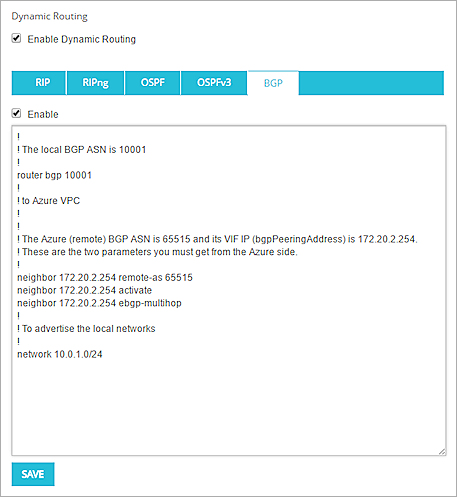
The configured BGP settings in Fireware Web UI
If you configure more than one trusted network on your Firebox, and you want Azure to learn the route to an additional trusted network, run an additional network command. For example:
network 10.0.1.0/24
network 10.0.2.0/24
Test the VPN Connection
To test the configuration, ping a local Azure resource from the local network behind your Firebox. Make sure that your Firebox and Azure virtual network are configured to allow ICMP traffic.
For more information about Azure configuration settings, go to the documentation provided by Microsoft.
BOVPN Virtual Interface for Static Routing to Microsoft Azure
Virtual Interface IP Addresses for a VPN to a Third-Party Endpoint