Applies To: ThreatSync+ NDR
ThreatSync+ is a cloud-based, network-centric threat detection and response solution that helps organizations identify, detect, and respond to network-based cyberattacks through an advanced, layered approach. ThreatSync+ uses advanced artificial intelligence (AI) and machine learning capabilities to deliver enterprise-level cyber defense across hybrid networks.
Throughout this documentation, ThreatSync+ refers generally to all ThreatSync+ products. When a feature is specific to a product, refer to the Applies To statement at the top of the Help topic for information about which products the topic is relevant to.
ThreatSync+ NDR continuously monitors and analyzes data flows and provides:
- Detection and response for your physical and private networks.
- Network analysis of both north-south traffic (traffic that enters or exits your network) and east-west traffic (traffic within your network).
- An open solution for multivendor networks, including WatchGuard Fireboxes, third-party switches, and third-party firewalls.
- Executive Summary and Ransomware Prevention Defense Goal reports.
- An optional Compliance Reporting license adds continuous compliance reporting for cyber networks.
ThreatSync+ NDR deploys across multiple locations and quickly integrates with your existing environment. Automation eliminates the need for threat hunters and forensic analysts.
ThreatSync+ monitors:
- Authentication threats, such as password and credential attacks.
- Network and cloud risks, including firewall rule failures and unsecured ports.
- Cyberattacks, including ransomware and supply chain attacks.
- File and data threats, such as the movement of sensitive files to public clouds or open file shares.
ThreatSync+ correlates these events and delivers actionable intelligence in the form of a network threat score that helps you to prioritize remediation actions. For more information, go to Network Threat Score.
For more information about ThreatSync+ NDR, go to these sections:
Licensing
To use ThreatSync+ NDR, you must purchase and activate a ThreatSync+ NDR license. ThreatSync+ NDR is licensed for each user. ThreatSync+ NDR will monitor active network devices up to two times the number of users in the license. For example, if your license is for 250 users, then ThreatSync+ NDR monitors network traffic for up to 500 active network devices (for example, workstations, mobile phones, IP phones, servers, cameras, or other IOT devices). To see a graph of the number of internal devices monitored over time, you can review the ThreatSync+ NDR monitoring dashboard (Monitor > Network Summary > Total Devices > Devices Over Time).
For more information on licensing, go to About ThreatSync+ NDR Licenses.
For more information on ThreatSync+ NDR licensing and enforcement, go to this Knowledge Base article: FAQ on ThreatSync+ NDR Licensing. (external)
(Optional) WatchGuard Compliance Reporting License
To use Compliance Reporting in WatchGuard Cloud, you must activate a ThreatSync+ NDR license and a Compliance Reporting license. Like ThreatSync+ NDR, Compliance Reporting is licensed for each user. It provides access to the reports in WatchGuard Cloud.
To make sure that Compliance Reporting reflects device data from all ThreatSync+ NDR users, we recommend that the number of users in your WatchGuard Compliance Reporting license matches the number of users in the ThreatSync+ NDR license. For example, if you purchase a ThreatSync+ NDR license for 250 users, then purchase a WatchGuard Compliance Reporting license for 250 users. For more information, go to About WatchGuard Compliance Reporting Licenses.
Data Collection
To gain visibility into all areas of your network, you should monitor IP traffic across all the devices in your network. Cloud-managed and locally-managed Fireboxes with cloud reporting that run Fireware v12.10.3 and higher automatically send network traffic data to WatchGuard Cloud and ThreatSync+. (For locally-managed Fireboxes with cloud reporting, you must enable the Firebox to send log messages for reports in each packet filter policy.) This data feed provides the information required for ThreatSync+ NDR to identify and detect potential threats and suspicious activities, such as lateral movements, DNS tunnels, fast and slow scans, and data exfiltration.
For Fireboxes that run lower versions of Fireware or third-party firewalls or switches, on-premise collection devices called collectors are used to monitor network traffic. Collectors take data feeds such as NetFlow and sFlow from third-party switches and firewalls, and forward them through a secure connection to WatchGuard Cloud. These data feeds include information on the traffic that flows through the switch or firewall to network devices. We recommend that you configure your switches and firewalls to relay network traffic data through these collectors to be forwarded to WatchGuard Cloud. For information on how to install and configure collectors on Linux computers and servers, go to Configure Collectors for ThreatSync+ NDR (Linux Computers). For information on how to install and configure collectors on Windows computers and servers, go to Configure Collectors for ThreatSync+ NDR (Windows Computers).
In addition to the Firebox, you can also install agent-based collectors on third-party switches and firewalls to relay NetFlow, sFlow, VPN, and Active Directory or DHCP logs to WatchGuard Cloud through a secure IPSec tunnel.
Reports
Reports are a critical part of monitoring your organization for threats. ThreatSync+ provides reports that enable you to track the health of your network.
ThreatSync+ NDR includes these default reports:
- Executive Summary Report
- Ransomware Prevention Defense Goal Report
To add more reports, plus the ability to generate custom reports, we recommend you add a WatchGuard Compliance Reporting license. WatchGuard Compliance Reporting provides additional defense goal reports for cybersecurity regulations and standards, as well as the ability to generate custom reports for specific defense goals.
The WatchGuard Compliance Reporting license includes these reports:
Cyber Essentials Certification
This report provides an overview of your network defense and shows whether you are in compliance with the objectives and controls outlined by the National Cyber Security Centre Cyber Essentials certification. This certification helps you to protect your organization against the most common cyber attacks.
FFIEC
This report provides an overview of your network defense and shows whether you are in compliance with the objectives and controls outlined by the Federal Financial Institutions Examination Council (FFIEC) guidelines. These guidelines help financial institutions operate safely, mitigate risk, comply with applicable regulations, follow legal requirements, and adequately manage cybersecurity risks.
ISO 27001 – Information Security, Cybersecurity and Privacy Protection
There are two versions of the ISO 27001 Defense Goal report — one for the 2013 version of the standard and one for the 2022 version.
These reports provide an overview of your network defense and show whether you are in compliance with the objectives and controls outlined by ISO 27001. This standard provides companies with guidance to establish, implement, maintain, and improve information security management systems.
Motion Picture Association Content Security Program
This report provides an overview of your network defense and shows whether you are in compliance with the objectives and controls outlined by the Motion Picture Association (MPA) Content Security Program. This program is a set of voluntary content security best practices to protect intellectual property against theft, piracy, and tampering.
NIST 800-53 – Security and Privacy Controls for Information Systems and Organizations
This report provides an overview of your network defense and shows whether you are in compliance with the objectives and controls outlined by the National Institute of Standards and Technology (NIST) guideline 800-53. NIST 800-53 provides a catalog of guidelines that support the development of secure and resilient federal information systems. These guidelines include operational, technical, and management safeguards to maintain the integrity, confidentiality, and security of federal information systems.
NIST 800-171 – Protecting Controlled Unclassified Information in Non-federal Systems and Organizations
This report provides an overview of your network defense and shows whether you are in compliance with the objectives and controls outlined by the National Institute of Standards and Technology (NIST) guideline SP 800-171. NIST SP 800-171 sets standards for safeguarding sensitive information on federal contractor IT systems and networks.
NIST CSF – Cybersecurity Framework
This report provides an overview of your network defense and shows whether you are in compliance with the objectives and controls outlined by the National Institute of Standards and Technology (NIST) cybersecurity framework (CSF). The CSF provides guidance to industry, government agencies, and other organizations to manage cybersecurity risks. It includes a taxonomy of high-level cybersecurity outcomes that organizations can use to better understand, assess, prioritize, and communicate their cybersecurity efforts.
For more information, go to About WatchGuard Compliance Reporting.
Executive Summary Report
The Executive Summary Report provides a high-level overview of the threats and vulnerabilities that ThreatSync+ NDR detects. The report includes an overall network threat score and shows you changes in the trend of the threat score over time. Lower scores indicate that your network might not be fully protected.
The included metrics reflect the range of detection and response capabilities provided by ThreatSync+ NDR. The overall network threat score is calculated from metrics across three areas of protection: Threat Detection, Network Visibility, and Policy Assurance.
Follow the recommendations in the report to improve your threat score and protect your network.
For more information, go to ThreatSync+ NDR Executive Summary Report.
Ransomware Prevention Defense Goal Report
The Ransomware Prevention Defense Goal Report monitors your network for vulnerabilities that can make you more susceptible to ransomware. This report presents a summary of the controls ThreatSync+ NDR monitors to help you prevent the spread of ransomware. Each control included in the report is based on a ThreatSync+ NDR policy.
The Ransomware Prevention Defense Goal Report provides you with a network defense overview and shows whether you are in compliance with the objectives and controls for a specified time period. This report, in addition to continuous monitoring of your policy alerts and closing Smart Alerts, can prove compliance for audit or cyber insurance purposes.
For more information, go to Ransomware Prevention Defense Goal Report.
ThreatSync+ UI
To configure and monitor ThreatSync+, you use the ThreatSync+ UI in WatchGuard Cloud. To connect to WatchGuard Cloud, go to cloud.watchguard.com and log in with your account credentials.
Monitor ThreatSync+
ThreatSync+ NDR automatically collects data from your Fireboxes in WatchGuard Cloud and includes default policies and Smart Alerts to help you monitor potential issues in your network.
Available pages and features vary and depend on your license type. Throughout this documentation, ThreatSync+ refers generally to all products. If you do not see a page or feature in the ThreatSync+ UI, it is not supported by your product.
To monitor ThreatSync+, select Monitor > ThreatSync+.

Use these pages to monitor ThreatSync+:
- Network Summary — Provides an overview of trends in your network and includes links to detailed information about Smart Alerts, policy alerts, device risks, and network traffic. For more information, go to About the ThreatSync+ Summary Page.
- Smart Alerts — Shows open Smart Alerts that indicate an attack might be in progress on your network and provides guidance to help you remediate the threat. For more information, go to About Smart Alerts.
- Policy Alerts — Shows alerts for policy violations on your network. For more information, go to About Policy Alerts.
-
Users — Shows details about user activity and threat detection in Microsoft 365. This page is available with a ThreatSync+ SaaS license. For more information, go to About ThreatSync+ SaaS Licenses and ThreatSync+ Users.
- Discover — Shows subnets and important servers and network devices that ThreatSync+ automatically identifies. For more information, go to ThreatSync+ NDR Asset Discovery.
- Audit Logs — Shows details of any configuration activity performed for ThreatSync+ policies and zones on your network. For more information, go to ThreatSync+ Audit Logs.
Configure ThreatSync+
You can configure ThreatSync+ specifically for your organization and network.
To configure ThreatSync+, select Configure > ThreatSync+.
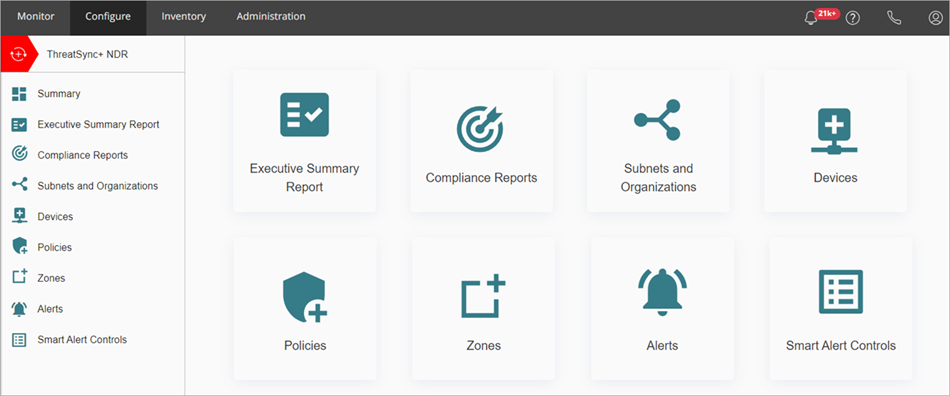
You can use these pages to configure ThreatSync+:
- Executive Summary Report — Configure settings for your Executive Summary Report. For more information, go to Configure the Executive Summary Report Settings.
- Compliance Reports — Manage your network defense goals and objectives for defense goal reports. For more information, go to Manage Network Defense Goals.
- Subnets and Organizations — Configure subnets and ranges of IP addresses to label your internal networks and important systems to help identify rogue devices. For more information, go to Configure Subnets and Organizations.
- Devices — Manage devices on your network and add or import new devices. For more information, go to Manage Devices.
- Policies — Manage default policies and add policies with custom policy definitions for your network. For more information, go to Configure ThreatSync+ Policies.
- Zones — Manage zones in your network and create custom zones. For more information, go to Manage ThreatSync+ Zones.
- Alerts — Specify which policy alerts and Smart Alerts generate email notifications. For more information, go to Configure ThreatSync+ Alerts and Notification Rules.
- Smart Alert Controls — Configure rules to filter Smart Alerts. For more information, go to Configure ThreatSync+ NDR Smart Alert Controls.
Quick Start — Set Up ThreatSync+ NDR