A Security Template is a set of configuration information that is used when you create VPN tunnels. When you use Security Templates, you do not have to create new security settings each time you create a tunnel. These templates include Phase 1 and Phase 2 settings that use the SHA1-AES256-DH5 and SHA2-AES256-DH5 encryption algorithms.
For more information about Phase 1 and Phase 2 settings, go to Configure IPSec VPN Phase 1 Settings and Configure Phase 2 Settings.
Predefined managed Security Templates are supplied for all of the available encryption types. You can use these settings to create secure tunnels that work correctly for most networks. However, if your network has special requirements, you can modify these existing templates or make new templates:
- SHA1-AES256-DH5 (Predefined)
- SHA2-AES256-DH5 (Predefined)
If your WSM Management Server is v11.11 or lower, the Predefined Security Templates are not available. Instead, these default templates are available:
- Medium
- Medium with Authentication
- Strong with Authentication
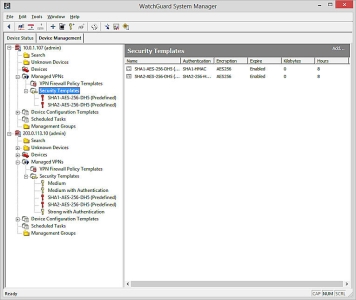
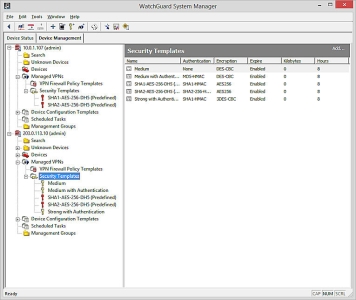
If you upgrade your Management Server to v11.11.1 or higher, the default templates are still available, and the Predefined Security Templates are added to the Security Templates list. For a newly installed Management Server v11.11.1 and higher, only the Predefined Security Templates are available. The Security Templates that are available on your Management Server appear in the Security Templates tree and on the Security Templates page. The Predefined templates are designated by a red key icon and the older, default templates are designated by a gold key icon.
Example of the Security Templates page for new installation of a Management Server v11.11.1 or higher
Example of the Security Templates page for a Management Server upgraded to v11.11.1 or higher
To add a Security Template:
- On the Device Management tab, click
 .
.
Or, select Edit > Insert Security Template.
Or, from the Management Server tree, select Managed VPNs > Security Templates and click Add.
The Security Template dialog box appears.
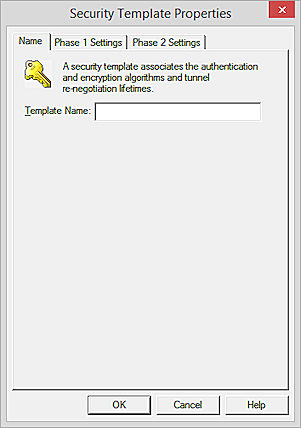
- In the Template Name text box, type a name for the template.
This is the name that appears in the Security Templates list and in the Add VPN Wizard. - Select the Phase 1 Settings tab.
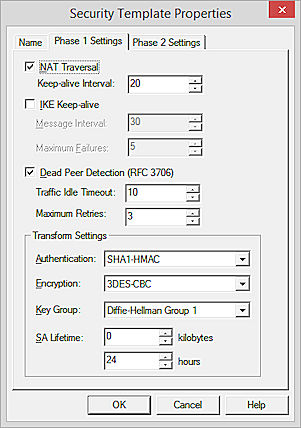
- To create a BOVPN tunnel between the Firebox and another device that is behind a NAT device, select the NAT Traversal check box.
NAT Traversal, or UDP Encapsulation, allows traffic to get to the correct destinations when a device does not have a public IP address.
To change the default NAT Traversal keep-alive interval, in the Keep-alive Interval text box, type or select the number of seconds before the next NAT keep-alive message is sent. - If both devices do not support Dead Peer Detection, and if both devices are Fireboxes, select the IKE Keep-alive check box to enable the Firebox to send messages to its IKE peer and keep the VPN tunnel open.
- To set the Message Interval, type or select the number of seconds.
- To set the maximum number of times the Firebox tries to send an IKE keep-alive message before it tries to negotiate Phase 1 again, in the Max Failures text box, type or select the number of attempts.
- If the other VPN endpoint supports it, select the Dead Peer Detection check box.
- To set the amount of time the Firebox waits before it sends a query to the remote peer, when a packet is waiting to be sent to the peer and no traffic has been received from the peer, in the Traffic Idle Timeout text box, type the amount of time.
- To specify the number of times the Firebox tries to contact the remote peer before it renegotiates the Phase 1 connection, in the Max Retries text box, type or select the number of retries.
Do not enable both IKE Keep-alive and Dead Peer Detection.
- From the Authentication drop-down list, select the authentication method.
- From the Encryption drop-down list, select the encryption method.
- From the Key Group drop-down list, select a Diffie-Hellman group.
Diffie-Hellman groups determine the strength of the master key used in the key exchange process. Higher group numbers are more secure, but more time is required to make the keys.
For more information, go to About Diffie-Hellman Groups. - To change the SA (security association) life, in the SA Life text boxes type or select a number to define the amount of time or traffic that must pass before the SA expires. For for no limit, type or select 0 (zero).
- Select the Phase 2 Settings tab.
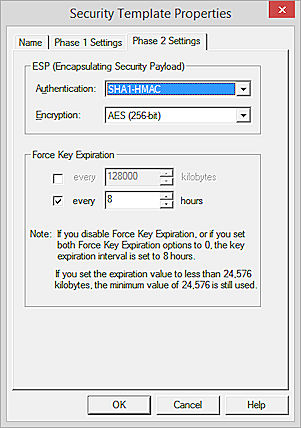
- From the Authentication drop-down list, select the authentication method for Phase 2.
- From the Encryption drop-down list, select the encryption method.
- To make the gateway endpoints generate and exchange new keys after a quantity of time or amount of traffic passes, select the Force Key Expiration check box. Select the duration and a number of kilobytes after which the key expires.
If Force Key Expiration is disabled, or if it is enabled and both the time and number of kilobytes are set to zero, the Firebox uses a default key expiration time of 8 hours.
The maximum expiration time is one year. - Click OK.