This topic describes how to use the FireCluster Setup Wizard in WatchGuard System Manager to set up a FireCluster with the auto-discovery method.
FireCluster Requirements
- Make sure you have everything necessary to configure your FireCluster and that you have planned your configuration settings. For information, go to Before You Configure a FireCluster.
- The Fireboxes must be the same model type and run the same version of Fireware to configure the devices in a FireCluster.
If you have a brand new Firebox with factory-default settings, the version of Fireware that is installed on the Firebox is indicated on a sticker on the device.
- Make sure you understand the limitations of a FireCluster, as described in Features Not Supported for a FireCluster.
- Make sure you understand how to connect the FireCluster members to each other and to the network, as described in Connect the FireCluster Hardware.
Do not connect your second Firebox to the cluster until you have configured the first Firebox that will be the cluster master. - Make sure you understand how to configure FireCluster models that include modular interfaces. For information, go to About FireCluster with Modular Interfaces.
- Make sure you understand how to set up an active/passive FireCluster with FireboxV devices. For information, go to Configure a FireCluster on VMware ESXi.
Configure FireCluster
To configure FireCluster:
- In WatchGuard System Manager, connect to the Firebox that has the configuration you want to use for the cluster. After you enable FireCluster and save the configuration, the Firebox restarts and this device becomes the cluster master.
- Click
 .
.
Or, select Tools > Policy Manager.
Policy Manager opens the configuration file for the selected device. - Select FireCluster > Setup.
The FireCluster Setup Wizard starts.

- Click Next.
- Select the type of cluster you want to enable:
Active/Passive Cluster
Enables the cluster for high availability, but not load sharing. If you select this option, the cluster has an active Firebox that handles all the connections and a passive Firebox that handles connections only if a failover of the first device occurs.
Active/Active Cluster
Enables the cluster for high availability and load sharing. If you select this option, the cluster balances incoming connection requests across both devices in the cluster.
For more information about cluster types, go to FireCluster Properties.

- Select the Cluster ID.
In most cases you can use the default value. The cluster ID uniquely identifies this cluster if you set up more than one cluster on the same layer 2 broadcast domain. If you only have one cluster, and your network does not have VRRP devices, you can use the default value.
For an active/passive cluster, the Cluster ID determines the VRRP virtual MAC (VMAC) addresses used by the interfaces of the clustered devices. If you configure more than one active/passive FireCluster on the same subnet, it is important to know how to set the Cluster ID to avoid a possible virtual MAC address conflict.
For more information about the Cluster ID, go to FireCluster Properties and Active/Passive Cluster ID and the Virtual MAC Address.
- If you selected Active/Active cluster, select the Load-balance method.
The load-balance method is the method used to balance connections among active cluster members. There are two options:
Least Connection
If you select this option, each new connection is assigned to the active cluster member with the lowest number of open connections. This is the default setting.
Round-Robin
If you select this option, new connections are distributed among the active cluster members in round-robin order. The first connection goes to one cluster member. The next connection goes to the other cluster member, and so on.
For more information about the load balance method, go to FireCluster Properties.
- Select the Primary and Backup cluster interfaces. The cluster interfaces are dedicated to communication between cluster members and are not used for other network traffic. You must configure the Primary interface. For redundancy, we recommend you also configure the Backup interface.
Primary
The device interface that you dedicate to primary communication between the cluster members. Select the interface number that you used to connect the FireCluster devices to each other.
Backup
The device interface that you dedicate to communication between the cluster members if the primary interface fails. Select the second interface number that you used to connect the FireCluster devices to each other, if any.
For more information about cluster interfaces, go to FireCluster Interfaces.
- Select the Interface for Management IP address. You use this interface to connect directly to FireCluster members for maintenance operations and to send log messages to a local server, such as a Dimension server. This is not a dedicated interface. It also is used for other network traffic. You cannot select an external interface that uses PPPoE as the Interface for Management IP address. We recommend that you select the interface that the management computer usually connects to. For more information about the interface for Management IP address, go to FireCluster Interfaces.
- When prompted by the configuration wizard, add these FireCluster member properties for each device:
Feature Key
For each device, import or download the feature key to enable all features for the device. If you previously imported the feature key in Policy Manager, the wizard automatically uses that feature key for the first device in the cluster.
For more information about the feature key, go to Add Cluster Member Feature Key.
Member Name
The name that identifies each device in the FireCluster configuration.
For more information about the member name, go to Add the FireCluster Member ID and Name.
Serial Number
The serial number of the Firebox. The serial number is used as the Member ID in the FireCluster Configuration dialog box. The wizard sets this automatically when you import or download the feature key for the Firebox.
For more information about the serial number, go to Add the FireCluster Member ID and Name.
Primary Cluster Interface IP Address
The IP address the cluster members use to communicate with each other over the primary cluster interface. The primary FireCluster IP address for each cluster member must be an IPv4 address on the same subnet.
The cluster member with the greater weighted average index (the combined system health index and interface health index) wins the election to become the cluster master. If the consolidated index for both cluster members is the same, the cluster member with higher primary cluster interface IP address wins the election to become the cluster master.
Backup cluster interface IP address
(Optional) The IP address the cluster members use to communicate with each other over the backup cluster interface. The backup FireCluster IP address for each cluster member must be an IPv4 address on the same subnet.
The primary and backup cluster interfaces must be on different, unused subnets. Make sure that you use subnets that do not overlap with local or VPN subnets. To avoid IP address conflicts with routable IP addresses, we recommend that you use Automatic Private IP Addressing (APIPA) subnets, also known as link-local addresses (169.254.0.1/16 – 169.254.255.254/16).
Management IP address
A unique IP address that you can use to connect to an individual Firebox while it is configured as part of a cluster. You must specify a different management IP address for each cluster member. If the interface you chose as the Interface for management IP address has IPv6 enabled, you can optionally configure an IPv6 management IP address.
The IPv4 management IP address can be any unused IP address. We recommend that you use an IP address on the same subnet as the interface you select as the Interface for management IP address. This is to make sure that the address is routable. The management IP address must be on the same subnet as the Dimension Server or syslog server that your FireCluster sends log messages to.
The IPv6 management IP address must be an unused IP address. We recommend that you use an IPv6 address with the same prefix as an IPv6 address assigned to the interface you selected as the Interface for management IP address. This is to make sure that the IPv6 address is routable.
For more information, go to About FireCluster Management IP Addresses.
- Review the configuration summary on the final screen of the FireCluster Setup Wizard. The configuration summary includes the options you selected and which interfaces are monitored for link status.

- Click Finish.
The FireCluster Configuration dialog box appears.
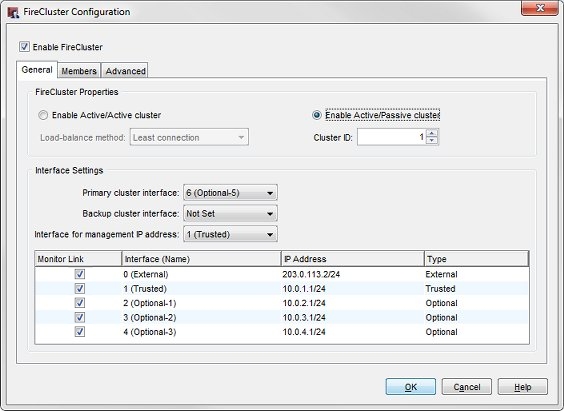
- In the Interface Settings section, review the list of monitored interfaces.
The list of monitored interfaces does not include the interfaces you configured as the Primary and Backup cluster interfaces. FireCluster monitors the link status for all enabled interfaces by default. If the cluster master detects loss of link on a monitored interface, the cluster master starts the failover process for that device.
For an active/passive cluster, you can select which of the active interfaces to monitor. If you do not want to monitor the link status of an enabled interface as a criteria for failover, clear the check box for that interface in the Monitor Link column.
We recommend that you configure the FireCluster to monitor the link status of all enabled interfaces.
An active/active FireCluster always monitors the link status of all enabled network interfaces. For an active/active FireCluster, you must disable any interfaces that are not connected to your network before you save the FireCluster configuration to the Firebox. To disable an interface:
- In Policy Manager, select Network > Configuration.
- Double-click the interface that you want to disable, and set the Interface Type to Disabled.
To automatically discover the second Firebox device and add it to the cluster, do not save the configuration file until you start the second Firebox in a factory-default state.
- Before you save the configuration of the cluster master Firebox to enable FireCluster:
- Start the second Firebox with factory-default settings. Use the reset instructions for your Firebox model. For more information, go to Reset a Firebox.
- Connect the cluster interface of the cluster master Firebox to the cluster interface of the second Firebox member of the FireCluster.
- Save the configuration to the cluster master Firebox.
When you save the configuration with FireCluster enabled to the Firebox:
- The Firebox restarts and becomes the cluster master.
- The cluster master Firebox uses the cluster interface to automatically discover the second cluster member Firebox.
- When the cluster master Firebox discovers a connected device with factory-default settings, it verifies that the serial number matches the serial number in the FireCluster configuration, and then sends the cluster configuration to the second device.
- The second device then joins the cluster and synchronizes all cluster status with the cluster master.
View FireCluster Status and Troubleshoot
After the cluster is active, you can monitor the status of the cluster members on the Firebox System Manager Front Panel tab or from Fireware Web UI. For more information, go to Monitor and Control FireCluster Members.
If the second device is not automatically discovered, you can manually trigger device discovery as described in Discover a Cluster Member.
For more information on how to troubleshoot cluster formation issues, go to Troubleshoot FireCluster.
FireCluster Formation Alternate Method
To more easily troubleshoot cluster members that do not join the cluster with the auto-discovery method because of network issues or a Fireware version mismatch, you use the alternate cluster formation method to save the Firebox configuration to both devices.
The alternate method enables you to view error and log messages about reasons why the cluster was not formed. For more information, go to Alternate FireCluster Configuration.
Connect the FireCluster to the Network
Now that the cluster is successfully formed, you can connect the Fireboxes to your network, as described in Connect the FireCluster Hardware
