This topic describes common problems and solutions for Mobile VPN with IKEv2:
Log Messages
In Fireware Web UI or Fireware System Manager, you can see log messages for Mobile VPN with IKEv2 on the Traffic Monitor page. You can also change the log level to help you troubleshoot.
To change the diagnostic log level for Mobile VPN with IKEv2:
- Set the diagnostic log level for IKE VPN.
To troubleshoot Mobile VPN with IKEv2 connections, you do not have to select the Enable logging for traffic sent from this device check box. This setting applies to traffic sent by the Firebox itself, which is also known as Firebox-generated traffic or self-generated traffic. - Open Traffic Monitor.
- Click the Search icon
 and type the Firebox IP address that IKEv2 VPN users connect to.
and type the Firebox IP address that IKEv2 VPN users connect to. - After you troubleshoot the problem, reset the diagnostic log level to the previous setting. The default setting is Error.
For information about log messages in WatchGuard Cloud, go to Log Messages.
We do not recommend that you select the highest logging level (Debug) unless a technical support representative directs you to do so while you troubleshoot a problem. When you use the highest diagnostic log level, the log file can fill up very quickly and performance of the Firebox can be reduced.
Installation Issues
If you cannot run the automatic configuration script that you downloaded from the Firebox:
- Make sure that you have Administrator permissions on the computer.
- If you cannot obtain Administrator permissions, you can deploy the IKEv2 VPN client with Microsoft Active Directory Group Policy (GPO).
For more information, go to How can I create and deploy custom IKEv2 and L2TP VPN profiles for Windows computers? in the WatchGuard Knowledge Base.
In Fireware v12.5.3 or lower, the automatic configuration script might fail if Windows Group Policy Objects specify digital signature restrictions for PowerShell scripts. To resolve this issue, upgrade to Fireware v12.5.4 or higher and download an updated installation script from your Firebox. The updated script uses the Bypass execution policy instead of the RemoteSigned policy.
Or, in Fireware v12.5.3 or lower, manually change the execution policy to Bypass:
- Open the WatchGuard installation script in a text editor.
- At the end of the script, change -ExecutionPolicy RemoteSigned to -Execution Policy Bypass.
The "Script cannot be loaded" error no longer appears when you run the script.
Connection Issues
When a user starts a Mobile VPN with IKEv2 connection:
- The VPN client starts a connection on port UDP 500. If that port is not open on the client gateway, the session does not proceed.
- If port UDP 500 is open, but NAT is detected, the connection proceeds on port UDP 4500. If the client gateway does not allow UDP 4500, IPSec and IKEv2 cannot proceed.
If the client gateway does not allow UDP port 500 or 4500, Windows users receive a message like this:
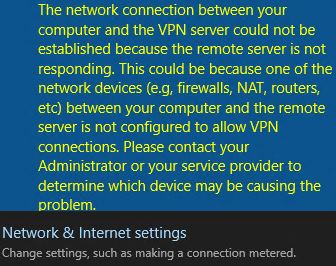
To troubleshoot this issue, verify that IPSec traffic can pass through the client gateway:
- On the client gateway, open the diagnostic or logging console.
- Verify that the gateway allows ESP and outbound traffic from the host on ports UDP 500 and UDP 4500.
If the client gateway does not have a diagnostic or logging console:
- Run a packet analyzer such as Wireshark on the user's computer to determine whether traffic from the required ports leaves the LAN or wireless network card.
- On the Firebox, run the tcpdump utility. For example, run:
-i eth0 -c2 –n host 198.51.100.100 and port 4500
In this example, you configure tcpdump to capture two inbound packets (-c2) without name resolution (-n) from the public IP address of the user (198.51.100.100) on port 4500 on the external interface of your firewall (eth0).
This error indicates the user does not have the Certificate Authority (CA) certificate installed in the local machine's Trusted CA store.
To import the certificate file, follow the instructions here:
- Configure Windows Devices for Mobile VPN with IKEv2
- Configure iOS and macOS Devices for Mobile VPN with IKEv2
- Configure Android Devices for Mobile VPN with IKEv2
In Windows, you can also install the certificate through the Microsoft Management Console (MMC):
- Open the MMC.
- Select File > Add/Remove Snap-in.
- From the Available snap-ins menu, select Certificates and click Add.
The Certificates snap-in wizard opens. - Select Computer Account and click Next.
- Select Local Computer and click Finish.
- From the list of certificates, right-click Trusted Root Certification Authorities.
- Select All Tasks > Import.
The Certificate Import Wizard opens. - Click Browse.
- Browse to the location where you saved the Mobile VPN with IKEv2 configuration file from your Firebox.
For information about how to download the configuration file, go to Configure Client Devices for Mobile VPN with IKEv2. - Select the rootca.crt file.
- Click Next.
- Keep the default values, which are Place all certificates in the following store and Trusted Root Certification Authorities.
- Click Finish.
Account-Related Connection Issues
During the VPN connection process, the Firebox verifies the user's identity and group membership on the local database or an existing RADIUS server.
The user must be a member of:
- The default IKEv2-Users group on the Firebox, or
- A group explicitly added during Firebox configuration.
If the VPN connection cannot establish because of a user account issue, the log message Unhandled external packet shows in Traffic Monitor on the Firebox. This log message indicates that the user is not part of a group that is allowed to connect to Mobile VPN with IKEv2.
Example log messages:
2020-06-26 06:22:48 admd Authentication of MUVPN user [John@Firebox-DB] from 203.0.113.209 was accepted msg_id="1100-0004" Event
2020-06-26 06:22:48 sessiond IKEv2 VPN user John@Firebox-DB from 203.0.113.209 logged in assigned virtual IP is 192.168.114.1 msg_id="3E00-0002" Event
2020-06-26 06:22:48 iked (203.0.113.150<->203.0.113.209)'WG IKEv2 MVPN' MUVPN IPSec tunnel is established. local:0 remote:0 in-SA:0x698360e1 out-SA:0xd5d960bc role:responder msg_id="0207-0001" Event
2020-06-26 06:22:49 Deny 192.168.114.1 255.255.255.255 bootps/udp 68 67 0-External Firebox Denied 328 128 (Unhandled External Packet-00) proc_id="firewall" rc="101" msg_id="3000-0148" src_user="John@Firebox-DB" Traffic
2020-06-26 06:22:49 Deny 192.168.114.1 255.255.255.255 netbios-ns/udp 137 137 0-External Firebox Denied 96 128 (Unhandled External Packet-00) proc_id="firewall" rc="101" msg_id="3000-0148" src_user="John@Firebox-DB" Traffic
2020-06-26 06:25:42 Deny 10.0.200.2 10.0.150.3 icmp tunnel.200 1-Trusted Denied 60 126 (Unhandled External Packet-00) proc_id="firewall" rc="101" msg_id="3000-0148" Traffic
2020-06-26 06:25:47 Deny 10.0.200.2 10.0.150.3 icmp tunnel.200 1-Trusted Denied 60 126 (Unhandled External Packet-00) proc_id="firewall" rc="101" msg_id="3000-0148" Traffic
For more information, go to About Mobile VPN with IKEv2 User Authentication.
If the user specifies the wrong password, the log message invalid credentials shows in Traffic Monitor on the Firebox.
Example log message:
2020-06-26 06:28:42 admd Authentication of MUVPN user [Bob@Firebox-DB] from 203.0.113.209 was rejected, password is incorrect msg_id="1100-0005" Event
If the user specifies a user name that does not exist on the authentication server, the log message user doesn't exist shows in Traffic Monitor on the Firebox.
Example log messages:
2020-06-26 06:32:26 admd Authentication of MUVPN user [Mike@Firebox-DB] from 203.0.113.209 was rejected, user doesn't exist msg_id="1100-0005" Event
Server is not responding (in which case all users from on that server may have problems authenticating):.
2020-06-26 14:39:26 admd Authentication server RADIUS(10.0.200.50):1812 is not responding msg_id="1100-0003" Event
2020-06-26 14:39:26 admd Authentication of MUVPN user [Mike@RADIUS] from 203.0.113.209 was rejected, Recv timeout msg_id="1100-0005" Event
For these account-related connection issues, users receive a general error message, such as:
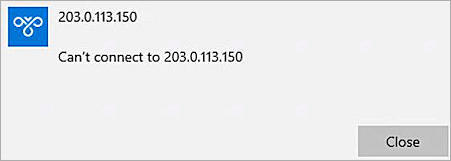
To troubleshoot issues with AuthPoint authentication, go to:
- Firebox Mobile VPN with IKEv2 Integration with AuthPoint
- Firebox Cloud Mobile VPN with IKEv2 Integration with AuthPoint for Azure Active Directory Users
- Troubleshoot AuthPoint
Issues After Connection
If users cannot connect to file shares, printers, or other network resources by domain name or IP address:
- Determine whether users can ping the IP address of an internal network resource or the internal interface of the Firebox.
- Make sure the Firebox policy that controls access to internal resources sends a log message for that activity. You can view the log messages to determine whether the Firebox sees the traffic and allows it to pass through.
For information about logging, go to Configure Logging and Notification for a Policy.
If the policy allows the traffic and the network resource is available, but the user does not receive a response from the network resource:
- Use the tcpdump diagnostic tool to filter the request from the interface or VLAN where the destination resource is. For example:
-i vlan10 -c2 -n host 10.0.10.250 and icmp - On the user's computer:
- Use a packet analyzer tool such as Wireshark to determine whether the host received the packet.
- Determine whether Windows Firewall or third-party software prevents connects to resources outside of the user's subnet. If so, add an exception or rule to allow such traffic.
- Verify the Firebox is the default gateway or has a route for the VPN client's virtual IP network through the Firebox.
To verify the VPN client configuration includes your internal DNS server for name resolution, on the Firebox:
- In the Mobile VPN with IKEv2 configuration, the default DNS setting is Assign the network DNS/WINS settings to mobile clients. Keep this default setting so the Firebox passes its Network DNS servers to mobile IKEv2 clients.

- In the Network DNS server settings at Network > Interfaces > DNS/WINS, verify the internal DNS server is the primary server. The primary server appears first in the list.
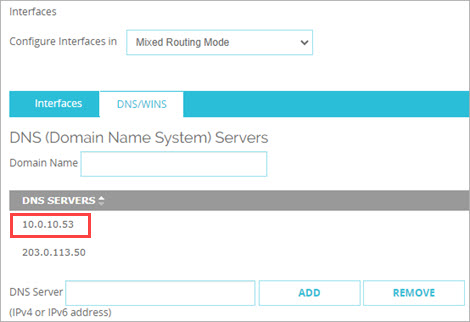
If users cannot use a single-part host name to connect to internal network resources, but they can use a Fully Qualified Domain Name (FQDN) to connect, the DNS suffix is not defined on the client. Mapped drives typically use host names, and the client needs a DNS suffix to find the DNS record for the file share.
In Fireware v12.9 or higher, the WatchGuard VPN client configuration files that you download from the Firebox can include a domain name suffix. In Fireware v12.9, for clients to inherit this suffix, you must:
- Enter a Domain Name in the network (global) DNS settings on the Firebox.
- In the Mobile VPN with IKEv2 configuration on the Firebox, select Assign the Network DNS/WINS settings to mobile clients.
- Download and install the client configuration files on user devices.
In Fireware v12.8.x or lower, Mobile IKEv2 clients do not inherit the domain name suffix specified in the Network DNS server settings on the Firebox. To specify a domain suffix for VPN clients, you have these options:
- Option 1 — Create a custom script for Active Directory GPO deployment. For more information, go to How can I create and deploy custom IKEv2 and L2TP VPN profiles for Windows computers? in the WatchGuard Knowledge Base.
- Option 2 — Manually configure a domain suffix in the VPN client settings. For more information, go to Manually configure DNS server and suffix settings for Windows VPN connections in the WatchGuard Knowledge Base.
For more information about DNS settings in the Mobile VPN with IKEv2 configuration, go to Configure DNS and WINS Servers for Mobile VPN with IKEv2.
For more information about global DNS settings on the Firebox, go to Configure Network DNS and WINS Servers.
In the mobile VPN configuration on the Firebox, if the IP address specified for user connections corresponds to an external VLAN interface, select the Apply firewall policies to intra-VLAN traffic check box in the VLAN configuration so that Firebox policies and NAT apply to mobile VPN user traffic. For more information about this setting, go to Define a New VLAN.
If users still cannot connect to network resources through an established VPN tunnel, go to Troubleshoot Network Connectivity for information about other steps you can take to identify and resolve the issue.