HTTPS-Proxy: Content Inspection
When content inspection is enabled on the HTTPS-proxy, the Firebox can decrypt HTTPS traffic, examine the content, then encrypt the traffic again with a new certificate. The HTTPS-proxy decrypts content for requests that match configured domain name rules configured with the Inspect action and for WebBlocker categories you select to inspect.
The available content inspection settings depend on whether the HTTPS proxy action is for outbound or inbound HTTPS requests.
HTTPS client proxy action
An HTTPS client proxy action specifies settings for inspection of outbound HTTPS requests. When you select the Inspect action in an HTTPS client proxy action, you select the HTTP client proxy action the HTTPS proxy uses to examine the decrypted content.
HTTPS server proxy action
An HTTPS server proxy action specifies settings for inspection and routing of inbound HTTPS requests to an internal web server. When you select the Inspect action for a domain name rule in an HTTPS server proxy action, you select the HTTP server proxy action or HTTP content action the HTTPS proxy uses to examine the decrypted content.
In Fireware v12.2 and higher, you can also choose to use the default Proxy Server certificate or a different Proxy Server certificate for each domain name rule. This enables you to host several different public-facing web servers and domains behind one Firebox and allow different domains to use different certificates for inbound HTTPS traffic. For more information, go to Use Certificates with Outbound HTTPS Proxy Content Inspection. For a demonstration of the use of certificates for outbound HTTPS content inspection, go to the Outbound Content Inspection video tutorial.
An HTTP content action enables the Firebox to route inbound HTTP requests to different internal web servers based on the content of the HTTP host header and the path in the HTTP request. For an example of how to configure content inspection with an HTTP content action, go to Example: HTTPS Proxy Action with an HTTP Content Action.
Enable Content Inspection in the HTTPS Proxy Action
You can use domain name rules, WebBlocker settings, or a combination of both to enable content inspection in the HTTPS-proxy.
Domain Name Rules
To enable content inspection with domain name rules, in Fireware Web UI, create a rule with the action set to Inspect:
- Edit the HTTPS proxy action used by your HTTPS-proxy policy.

- Below the Domain Names list, click Add.
- Create your Domain Names rule. When you create the rule, select the Inspect action to enable content inspection.
For detailed instructions on how to create domain name rules, go to HTTPS-Proxy: Domain Name Rules.
- Click OK.
The domain name rule is added to the Domain Names list. The Content Inspection Status shows that content inspection is on for Domain Name Rules.

To enable content inspection with domain name rules, in Policy Manager, create a rule with the action set to Inspect:
- Edit the HTTPS proxy action used by your HTTPS-proxy policy.
- In the Domain Names section, click Add.

- Create your Domain Names rule. When you create the rule, select the Inspect action to enable content inspection.
For detailed instructions on how to create domain name rules, go to HTTPS-Proxy: Domain Name Rules.
- Click OK.
The domain name rule is added to the Domain Names list. The Content Inspection Status shows that content inspection is on for Domain Name Rules.

WebBlocker
In the WebBlocker settings in the proxy action you can select allowed categories to inspect, and you can enable inspection of uncategorized sites.
To use WebBlocker in an HTTPS proxy action to enable content inspection, from Fireware Web UI:
- Add or edit the HTTPS proxy action.
- Select WebBlocker.
- From the WebBlocker drop-down list, select a WebBlocker action.
- In the Inspect column, select the check boxes for categories on which to perform content inspection. You can only inspect categories with the Allow or Warn action. You cannot inspect categories that are denied by the WebBlocker action.

For detailed instructions on how to configure WebBlocker in an HTTPS proxy action, go to HTTPS-Proxy: WebBlocker.
- From the Proxy Action drop-down list, specify the proxy action to use for inspection.
- In the Inspect column, select the check boxes for categories on which to perform content inspection. To inspect content for URLs that do not match a WebBlocker category, select the Inspect when a URL is uncategorized check box.
- Click OK.
To use WebBlocker in an HTTPS proxy action to enable content inspection, from Policy Manager:
- Edit the HTTPS proxy action.
In the Categories tree, select WebBlocker.
The WebBlocker page appears. - From the WebBlocker drop-down list, select a WebBlocker action.
- In the Inspect column, select the check boxes for categories on which to perform content inspection.
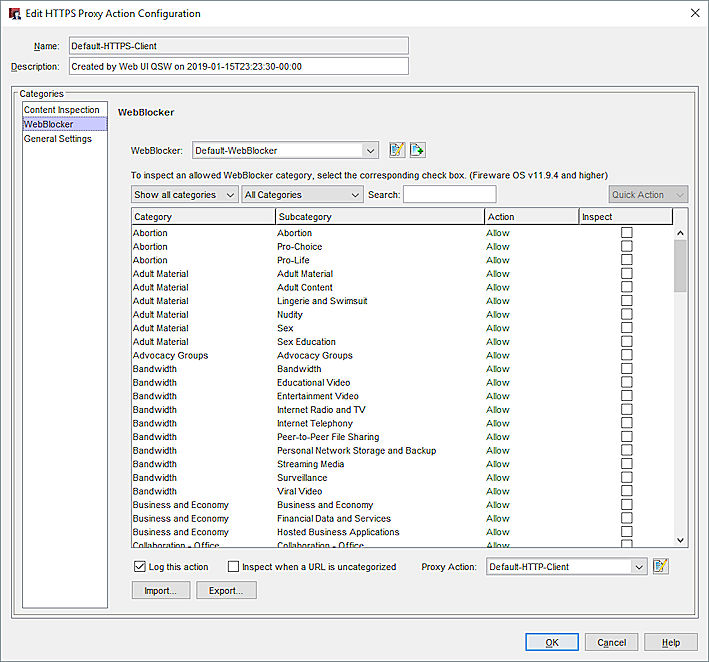
For detailed instructions on how to configure WebBlocker in an HTTPS proxy action, go to HTTPS-Proxy: WebBlocker.
- From the Proxy Action drop-down list, specify the proxy action to use for inspection.
- Click OK.
Modify the TLS Profile in the HTTPS Proxy Action
- Disable OSCP to improve latency when you browse the web
- Enable TLS compliance to prevent non-TLS/HTTPS traffic through the proxy
- Enable a minimum protocol version
We recommend you use the default TLS Profile settings.
In Fireware v12.1.1 and higher, you configure the HTTPS content inspection settings in a TLS profile that is used by the HTTPS proxy action. By default, the HTTPS proxy action uses a predefined TLS profile. You can edit the TLS profile settings in the proxy action, or from the TLS Profiles page.
- Edit the HTTPS proxy action used by your HTTPS-proxy policy.
The Content Inspection tab is selected by default.
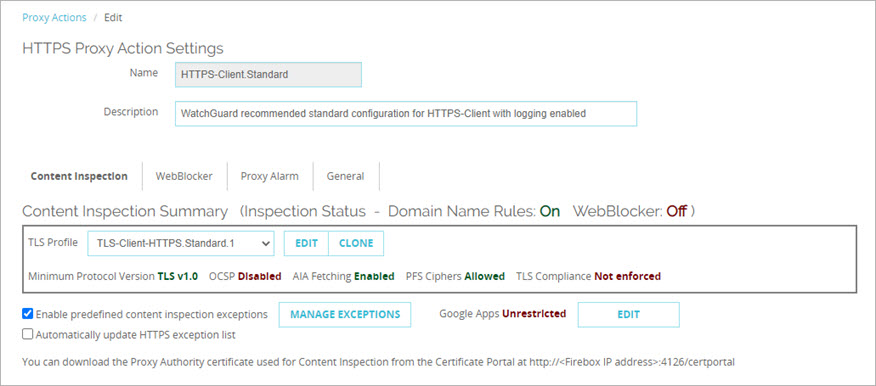
- From the TLS Profile drop-down list, select the TLS profile to use.
The settings for the selected profile show in the Content Inspection Summary.
- Minimum Protocol Version — Shows the minimum protocol version allowed
- OCSP — Shows whether OCSP is set to Disabled, Lenient, or Strict
- PFS Ciphers — Shows whether Perfect Forward Secrecy Ciphers is set to Allowed, Required, or None
- TLS Compliance — Shows whether TLS Compliance is enforced
- To edit the TLS profile, click Edit. Predefined TLS profiles are not editable. To edit a predefined TLS profile, you must first click Clone to make an editable copy.
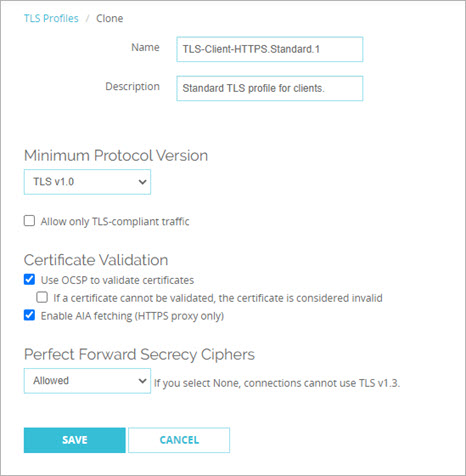
- Configure the TLS Profile settings as required for your network. For more information, see Configure TLS Profiles.
- To enable content inspection, select the Inspect action in the domain name rules or WebBlocker settings. For more information, see HTTPS-Proxy: Domain Name Rules, and HTTPS-Proxy: WebBlocker.
- Edit the HTTPS proxy action used by your HTTPS-proxy policy.
- In the Categories list, select Content Inspection.
The Content Inspection settings appear.

- From the TLS Profile drop-down list, select the TLS profile to use.
The settings for the selected profile show in the Content Inspection Summary.
- Minimum Protocol Version — Shows the minimum protocol version allowed
- OCSP — Shows whether OCSP is set to Disabled, Lenient, or Strict
- PFS Ciphers — Shows whether PFS Ciphers is set to Allowed, Required, or None
- TLS Compliance — Shows whether TLS Compliance is enforced
- To edit the TLS profile, click
 . To edit a predefined TLS profile, you must click
. To edit a predefined TLS profile, you must click  to make an editable copy.
to make an editable copy.
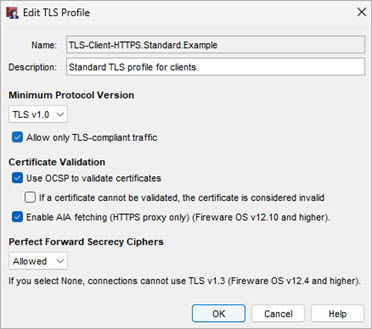
- Configure the TLS Profile settings as required for your network. For more information, see Configure TLS Profiles.
TLS compliant traffic refers to TLS protocol messages that adhere to TLS/SSL standards that are considered secure and can be interpreted by the HTTPS proxy. This is not automatically enabled when you enable content inspection. If TLS-compliant traffic is not enabled, you can allow non-compliant protocol traffic (used by some VPN software and other applications).
When TLS compliant traffic is enabled, if the tunneled traffic does not use a valid HTTPS protocol, the HTTPS proxy action prompts the Firebox to send a log message about the errors and drops the traffic.
When you enable content inspection in the HTTPS-proxy you can block user access to personal Google services. For more information, go to Restrict Google Apps to Allowed Domains.
Manage Content Inspection Exceptions
When you enable content inspection in an HTTPS proxy action, the Content Inspection Exceptions list is enabled by default. If you do not want to allow encrypted connections to the domains in the exception list you can disable the entire exception list, or disable specific exceptions.
Content Inspection Exceptions are supported in Fireware v12.1 and higher.
The Content Inspection Exceptions list includes domains for services that are known to be incompatible with content inspection. The Manage Content Inspection Exceptions list is created and maintained by WatchGuard. You can enable or disable the predefined exceptions. You cannot add or remove exceptions. For more information about default exceptions, see the Knowledge Base article Which applications are on the default exception list in an HTTPS proxy action?
- The HTTPS-proxy does not perform content inspection for a domain when the content inspection exception is enabled.
- Content inspection exceptions are shared by all HTTPS proxy actions that have predefined content inspection exceptions enabled.
Domain name rules have higher precedence than any match in the Content Inspection Exceptions list. If a domain name rule is matched, the action from that rule will always be applied. If there are other domains you do not want the proxy to inspect, you can configure domain name rules to bypass inspection. For more information about domain name rules, see HTTPS-Proxy: Domain Name Rules.
To enable or disable predefined content inspection exceptions, content inspection must be enabled in the Domain Name Rules or WebBlocker settings in the proxy action.
In Fireware v12.7 and higher, you can use the Automatically Update HTTPS Exception List check box to specify whether to update the Content Inspection Exceptions list automatically when WatchGuard makes changes. By default, the check box is selected and the list updates automatically.
The HTTPS Exception List continues to update even when your feature license expires. The Firebox checks for a new version every hour, by default.
- In the HTTPS proxy action, select Content Inspection.
The Content Inspection Summary section shows the current Content Inspection status and configuration settings.
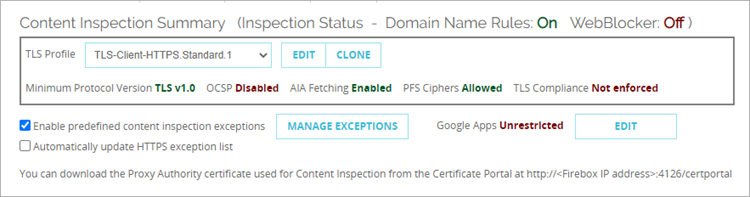
- To disable all predefined content inspections, clear the Enable Predefined Content Inspection Exceptions check box.
- To specify whether to update the Content Inspection Exceptions list automatically, select or clear the Automatically Update HTTPS Exception List check box.
- To disable specific content inspection exceptions, below the Content Inspection Summary, click Manage Exceptions.
The Manage Content Inspection Exceptions dialog box opens.
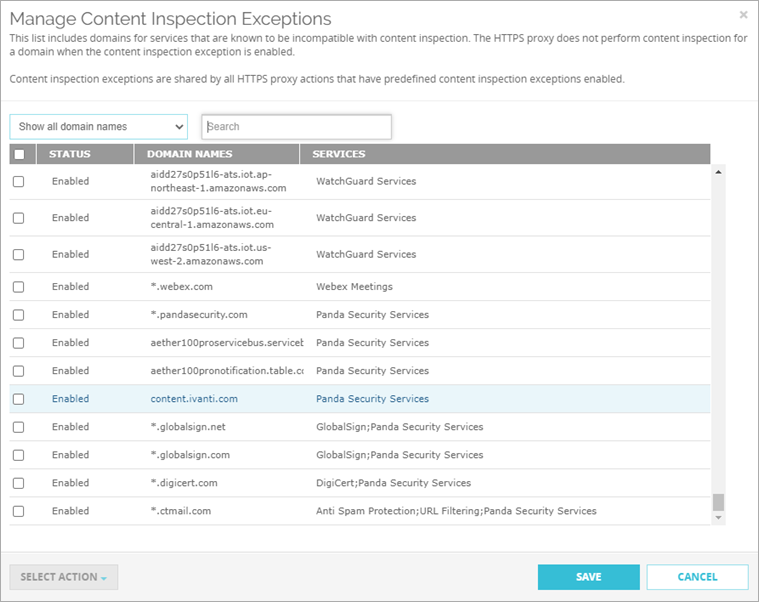
- Search for a domain or select a display option:
- Show all domain names
- Show only enabled domain names
- Show only disabled domain names
- Select one or more domains.
- From the Select Action drop-down list, select Enable or Disable.
- Click Save.
- In the HTTPS proxy action, select Content Inspection.
The Content Inspection Summary section shows the current content inspection status and configuration settings.

- To disable all predefined content inspections, clear the Enable Predefined Content Inspection Exceptions check box.
- To specify whether to update the Content Inspection Exceptions list automatically, select or clear the Automatically Update HTTPS Exception List check box.
- To disable specific content inspection exceptions, below the Content Inspection Summary, click Manage Exceptions.
The Manage Content Inspection Exceptions dialog box opens.
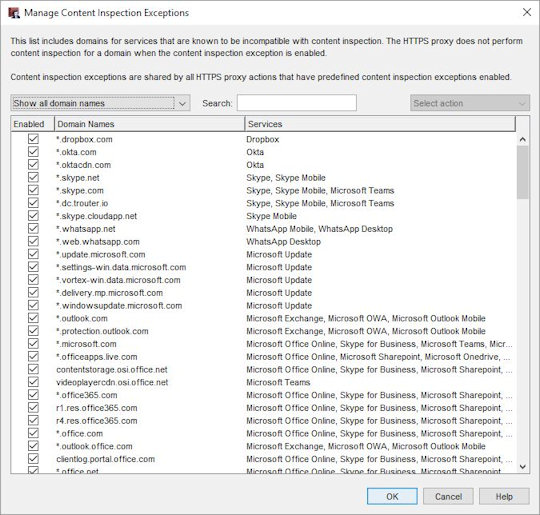
- Search for a domain or select a display option:
- Show all domain names
- Show only enabled domain names
- Show only disabled domain names
- Select one or more domains.
- From the Select Action drop-down list, select Enable or Disable.
- Click Save.
Use Certificates with Outbound HTTPS Proxy Content Inspection.