HTTPS-Proxy: WebBlocker
For an HTTPS client proxy action you can use WebBlocker to allow or deny web site content based on WebBlocker categories. In the proxy action WebBlocker settings, select the WebBlocker action that defines the content categories you want to deny. In the WebBlocker settings in the proxy action you can select allowed categories to inspect, and you can enable inspection of uncategorized sites.
WebBlocker and Domain Name Rules
Domain name rules take precedence over WebBlocker actions configured in the HTTPS proxy action. The domain name rules configured in the Content Inspection settings control which proxy action settings are used and whether WebBlocker is used to filter content.
- For HTTPS requests that match a domain name rule with the Inspect action, the proxy uses the WebBlocker profile in the HTTP proxy action to filter the content.
- For HTTPS requests that do not match a domain name rule, if the action for domain names that do not match a rule is set to Allow, the proxy uses the WebBlocker profile and inspection settings in the HTTPS proxy action.
- For HTTPS requests that match a domain name rule with the Allow action, WebBlocker is not used to filter or inspect the content.
For more information about domain name rules, see HTTPS-Proxy: Domain Name Rules.
HTTPS Proxy and Deny Messages
If you enable WebBlocker in an HTTPS proxy action, but do not enable content inspection, the proxy action uses the website certificate to identify the website category and decide whether to allow or deny access. Without content inspection, the HTTPS proxy action cannot selectively deny website content, and users do not see a deny message when content is denied by WebBlocker. There is also no option for the user to type a WebBlocker local override passphrase.
To enable the HTTPS proxy action to decrypt the client connection and selectively deny site content, enable content inspection in the HTTPS proxy. With content inspection enabled, the Firebox displays a deny message to the user when content is denied by WebBlocker or any other proxy scanning actions.
In Fireware 12.4 and higher, websites in categories with the Warn action are allowed by the HTTPS proxy action when you enable WebBlocker but do not enable content inspection. Users do not see a warn message unless content inspection is enabled.
For more information about content inspection, see HTTPS-Proxy: Content Inspection.
Configure WebBlocker in an HTTPS Proxy Action
- Add or edit the HTTPS proxy action.
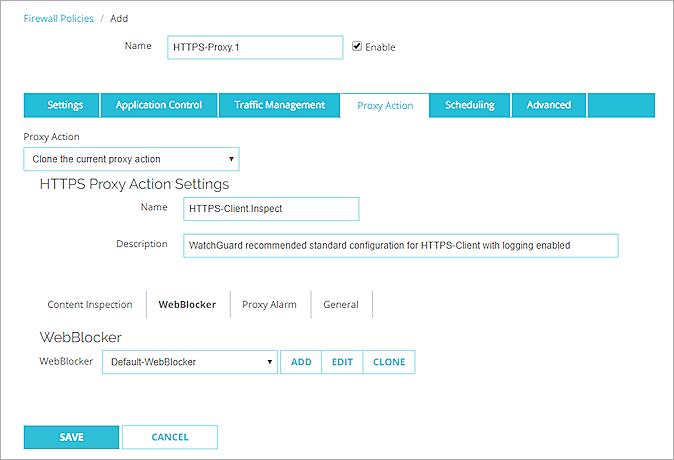
- Select WebBlocker.
- From the WebBlocker drop-down list, select a WebBlocker action.
To edit the selected WebBlocker action, click Edit.
Or, to create a new WebBlocker action, select an existing action and click Clone.
- In the Inspect column, select the check boxes for categories on which to perform content inspection. You can only inspect categories with the Allow or Warn action. You cannot inspect categories that are denied by the WebBlocker action.

- To inspect content for URLs that do not match a WebBlocker category, select the Inspect when a URL is uncategorized check box. Tip!
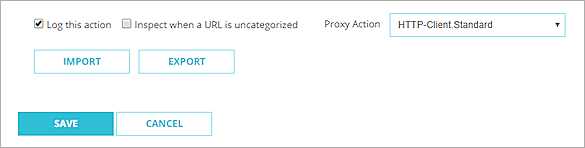
- From the Proxy Action drop-down list at the bottom of the page, select the HTTP proxy action to use for inspection.
- Click Save.
- Edit the HTTPS proxy action.
- In the Categories tree, select WebBlocker.
The WebBlocker page appears. - From the WebBlocker drop-down list, select a WebBlocker action.
Or, to create a new WebBlocker action, click .
.

- In the Inspect column, select the check boxes for categories on which to perform content inspection. You can only inspect categories with the Allow or Warn action. You cannot inspect categories that are denied by the WebBlocker action.
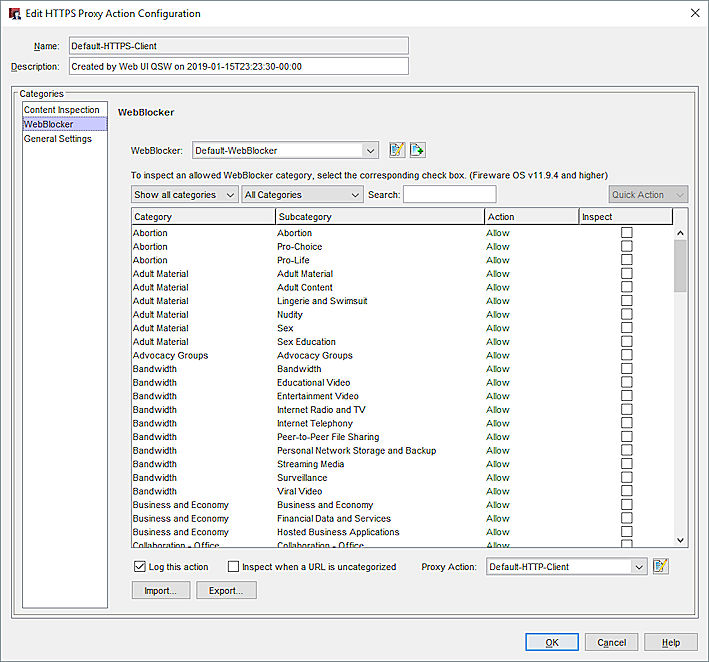
- To inspect content for URLs that do not match a WebBlocker category, select the Inspect when a URL is uncategorized check box.
- From the Proxy Action drop-down list, specify the proxy action to use for inspection.
- Click OK.
Import and Export WebBlocker Inspection Settings
If you manage several Fireboxes or use WebBlocker with more than one proxy definition, you can import and export the content inspection settings between them. This saves time because you must define the inspection categories only once. The settings are exported as an xml file.
To export WebBlocker inspection settings from an HTTPS client proxy action:
- Edit the HTTPS client proxy action.
- In the proxy action, select the WebBlocker action.
- Click Export.
The categories to inspect are exported to an xml file.- In Fireware Web UI, the file name is wb_cats_dpi.xml.
- In Policy Manager, the default file name is wb_exports.xml.
After you export the WebBlocker inspection settings, you can import the file to another HTTPS proxy action on the same Firebox or a different Firebox. When you import the categories to inspect from a file, this replaces any categories you have previously selected in the proxy action configuration.
To import WebBlocker inspection settings to an HTTPS client proxy action:
- Edit the HTTPS client proxy action.
- Select the WebBlocker action.
- Click Import.
- Select the file to import.
Inspection is enabled for the WebBlocker categories in the file.
If the xml file includes WebBlocker categories for inspection that are not allowed in the WebBlocker configuration in the proxy action, those categories are not selected for inspection after the import.
For more information about WebBlocker, see About WebBlocker.