Applies To: ThreatSync+ NDR, ThreatSync+ SaaS
Policy alerts notify you of activity on your network that is unauthorized or unexpected. When you configure ThreatSync+ policies to reflect the access policies of your organization, each policy alert you receive indicates a policy violation that might be a threat to your organization.
ThreatSync+ NDR Default Policies
When you first set up ThreatSync+ NDR, a subset of policies are activated by default. These are identified by the tag Level 1 and they automatically generate policy alerts. About 30 of the more than 75 available policies are included in Level 1. These default policy alerts reflect the threats and vulnerabilities that are most common and easiest to remediate. For more information, go to ThreatSync+ NDR Level 1 Policies.
ThreatSync+ SaaS Default Policies
When you first set up a ThreatSync+ SaaS integration with Microsoft 365, seven policies are activated by default. These are identified by the tag Level 1 and they automatically generate policy alerts. For more information, go to Level 1 Policies for ThreatSync+ SaaS — Microsoft 365.
For policy alerts that are based on machine learning, ThreatSync+ builds a baseline of activity and generates a policy alert only when traffic varies from this baseline. If you receive too many policy alerts, or want to change the threat sensitivity, you can tune your policies. For more information, go to Policy Tuning.
Monitor Policy Alerts
Policy alerts show on the ThreatSync+ Policy Alerts page. The ThreatSync+ Policy Alerts page provides a centralized list of policy alerts for operators to review and respond to. To respond to policy alerts, you can manually block devices or block unauthorized access, and tune your policies to ignore future, expected activity.
You can also set up email notifications for the creation of policy alerts. For more information, go to Configure ThreatSync+ Alerts and Notification Rules.
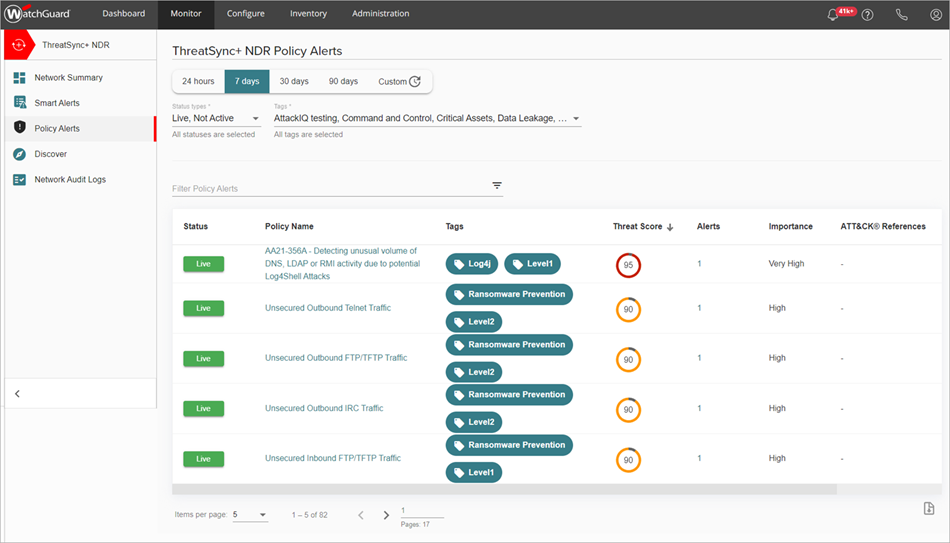
The ThreatSync+ Policy Alerts page shows these details:
- Status — Status of the policy. The status can be Live or Not Active. If you click Live, the status changes to Not Active and the policy is deactivated. If you click Not Active, the status changes to Live and the policy is activated.
- Policy Name — Name of the policy. Click the policy name to view the Policy Alert Details page.
- Tags — Tags you define and apply to organize your devices, subnets, and organizations.
- Threat Score — Threat score of the policy alert. The policy alert list is sorted by highest threat score by default.
- Alerts — The number of policy alerts for a specific policy. Click the alert number to view the Policy Alert Details page.
- Importance — A rating you assign to indicate how valuable this device is to your organization. The importance level should reflect the impact to your organization if this device is damaged or lost. This value is used to calculate the risk level of an asset in conjunction with the advanced threat detection of ThreatSync+.
- ATT&CK® References — Shows a MITRE ATT&CK type and link, if available.
- Description — A description of the policy alert.
To monitor policy alerts:
- Select Monitor > ThreatSync+ > Policy Alerts.
The ThreatSync+ Policy Alerts page opens. - To view specific policy alerts:
- To view specific policy alerts, click the policy alert. For more information, go to View Policy Alert Details.
Change the Date Range
By default, the policy alerts list shows policy alerts for the last seven days. You can change the date to view policy alerts for different dates.
To filter the policy alerts list by date:
- Click a date in the date widget for one of these time periods:
- 24 hours
- 7 days
- 30 days
- 90 days
- Custom
- If you select Custom, specify a start date and time, and an end date and time for the custom time period.
Sort and Filter the Policy Alerts List
By default, the policy alert list shows policy alerts with the highest threat score, sorted in descending order, so the most critical policy alerts are at the beginning of the list.
To customize which policy alerts you view, you can filter the policy list by status types, tags, or by keyword search.
To sort the policy alert list, click a column name to sort the policy alerts list by that column.
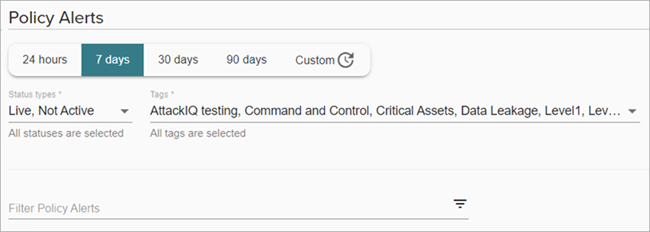
To filter the policy alert list:
- From the Status types drop-down list, select whether you want to filter the policy alerts list by Live or Not Active status, or both.
- From the Tags drop-down list, select the tags you want to include in your filtered results.
- In the Filter Policy Alerts text box, enter a keyword to filter your results.
View Policy Alert Details
To view more details about a specific policy alert, click the policy name.
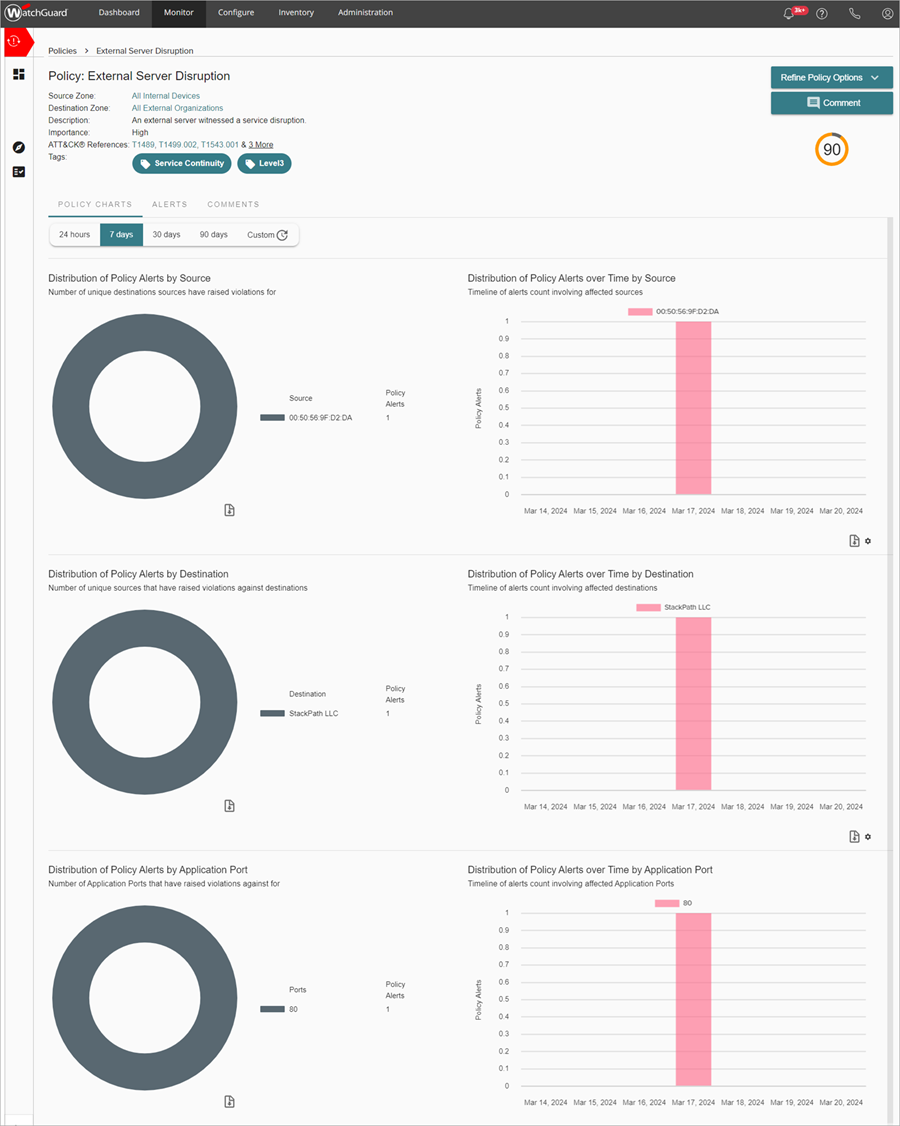
The Policy Alert Details page includes these details:
- Source and destination zone information
- Description of the policy alert
- How the policy alert works
- How to tune the policy alert
- Importance
- Threat score
- Tags associated with the policy
You can modify policy configuration details from the Refine Policy Options drop-down list:
- Refine Activity Triggers
- Refine Source Zones
- Refine Destination Zones
For more information, go to Configure ThreatSync+ Policies.
Three tabs show detailed policy alert information:
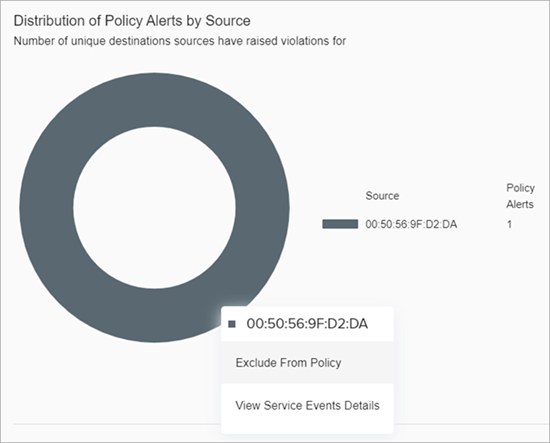
- Policy Charts — Shows charts that vary by policy alert type. Details can include the distribution of policy alerts by source, time, destination, and application port. Point to chart to view details and perform actions. For example, click Exclude From Policy to exclude a device from a policy, or click View Traffic Details to view anomalous traffic information.
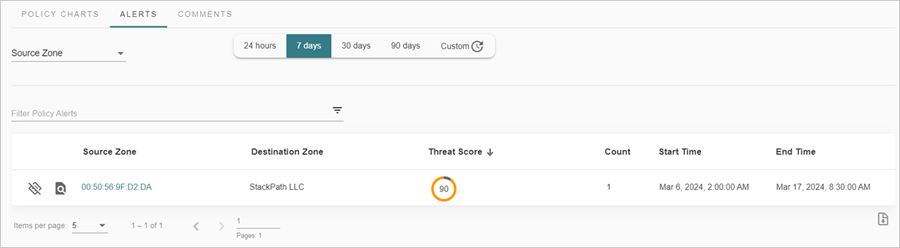
- Alerts — Shows zone and threat score details about the policy alert. You can filter the tab to show Source Zone or Destination Zone charts, or filter the list by threat score. Click the source zone name to view device details and activity.
- Comments — Shows a history of comments associated with the policy alert. Click Comment to add a comment to a policy alert.
Deactivate a Policy
To deactivate a policy directly from the Policy Alerts page, click Live next to the policy name to change the status to Not Active.
Configure ThreatSync+ Policies