Applies To: ThreatSync+ NDR
ThreatSync+ NDR defense goal reports are actionable reports that help you monitor threats and prove compliance for audit or cyber insurance purposes.
Available ThreatSync+ NDR reports depend on your license type. The Executive Summary and Ransomware Prevention reports are included by default with ThreatSync+ NDR. To add more reports, and the ability to generate custom reports, we recommend you add a WatchGuard Compliance Reporting license. For more information, go to About WatchGuard Compliance Reporting.
The Compliance Reporting license includes these ThreatSync+ NDR defense goal reports:
Cyber Essentials Certification
This report provides an overview of your network defense and shows whether you are in compliance with the objectives and controls outlined by the National Cyber Security Centre Cyber Essentials certification. This certification helps you to protect your organization against the most common cyber attacks.
FFIEC
This report provides an overview of your network defense and shows whether you are in compliance with the objectives and controls outlined by the Federal Financial Institutions Examination Council (FFIEC) guidelines. These guidelines help financial institutions operate safely, mitigate risk, comply with applicable regulations, follow legal requirements, and adequately manage cybersecurity risks.
ISO 27001 – Information Security, Cybersecurity and Privacy Protection
There are two versions of the ISO 27001 Defense Goal report — one for the 2013 version of the standard and one for the 2022 version.
These reports provide an overview of your network defense and show whether you are in compliance with the objectives and controls outlined by ISO 27001. This standard provides companies with guidance to establish, implement, maintain, and improve information security management systems.
Motion Picture Association Content Security Program
This report provides an overview of your network defense and shows whether you are in compliance with the objectives and controls outlined by the Motion Picture Association (MPA) Content Security Program. This program is a set of voluntary content security best practices to protect intellectual property against theft, piracy, and tampering.
NIST 800-53 – Security and Privacy Controls for Information Systems and Organizations
This report provides an overview of your network defense and shows whether you are in compliance with the objectives and controls outlined by the National Institute of Standards and Technology (NIST) guideline 800-53. NIST 800-53 provides a catalog of guidelines that support the development of secure and resilient federal information systems. These guidelines include operational, technical, and management safeguards to maintain the integrity, confidentiality, and security of federal information systems.
NIST 800-171 – Protecting Controlled Unclassified Information in Non-federal Systems and Organizations
This report provides an overview of your network defense and shows whether you are in compliance with the objectives and controls outlined by the National Institute of Standards and Technology (NIST) guideline SP 800-171. NIST SP 800-171 sets standards for safeguarding sensitive information on federal contractor IT systems and networks.
NIST CSF – Cybersecurity Framework
This report provides an overview of your network defense and shows whether you are in compliance with the objectives and controls outlined by the National Institute of Standards and Technology (NIST) cybersecurity framework (CSF). The CSF provides guidance to industry, government agencies, and other organizations to manage cybersecurity risks. It includes a taxonomy of high-level cybersecurity outcomes that organizations can use to better understand, assess, prioritize, and communicate their cybersecurity efforts.
Every defense goal report has a similar format, but each report has different objectives and controls, based on the specific requirements for compliance for each guideline, standard, or certification. To configure objectives and network defense controls for your defense goal reports, go to Manage Network Defense Goals.
Defense goal reports provide you with a network defense overview and show whether you are in compliance with the objectives and controls for a specified time period. You can generate this report for up to a six month time period.
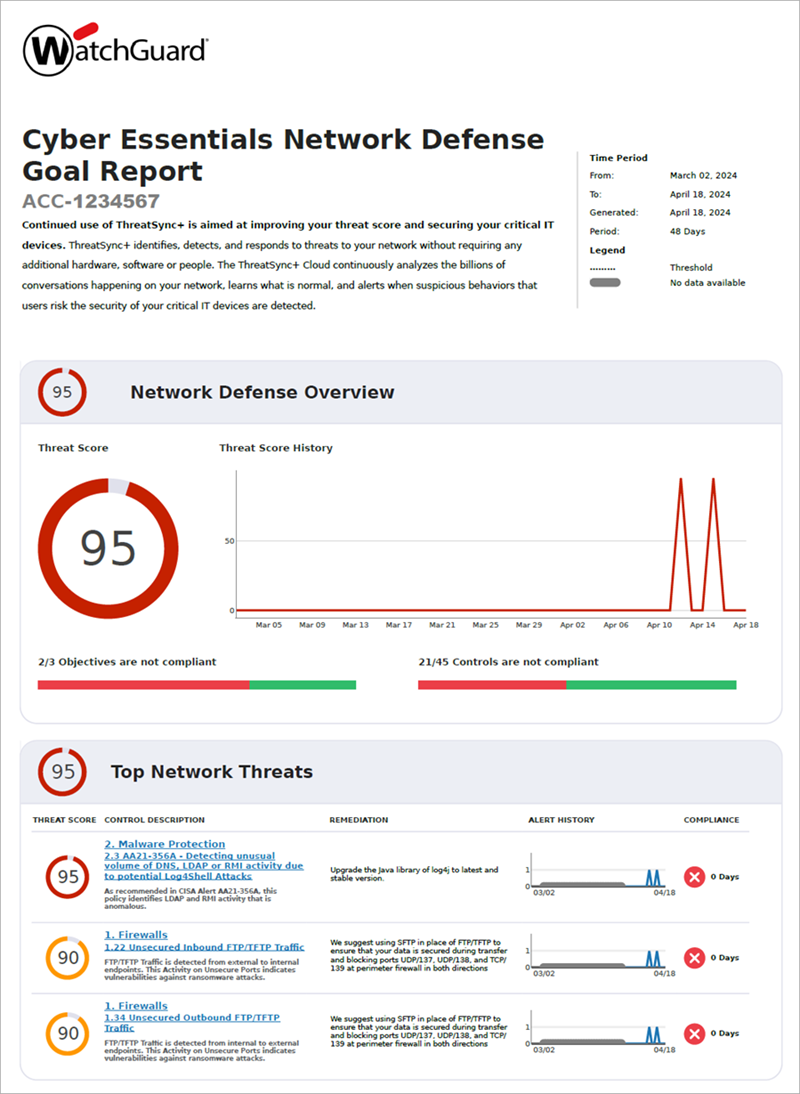
Network Defense Overview
The Network Defense Overview section provides a snapshot of your overall network defense. You can view your threat score, threat score history, and how many objectives and controls are compliant or not compliant.
Your threat score represents your potential exposure to threats in your network. This threat score is an aggregation of the threat scores for each of the controls presented in the report. The defense goal is a collection of defense objectives, each organized around a specific prevention area. Each defense objective consists of a set of controls that you should enable and monitor to help prevent cyberattacks.
Threat Score
The overall threat score shows the highest value recorded in the report period.
Threat Score History
The Threat Score History chart shows the defense goal threat score for each day in the report period.
Objectives and Controls
The Objective and Control summary charts show the proportion of objectives and controls that are compliant, violated, or which insufficient data is available to evaluate.
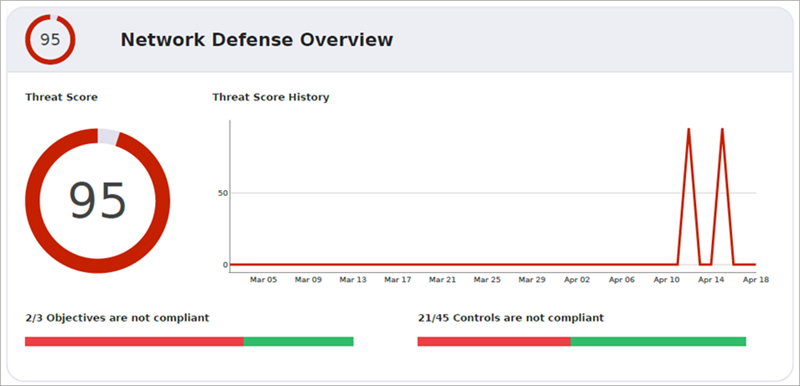
Top Network Threats
The Top Network Threats section lists the three highest-risk controls covered in this report. This section shows a chart of your top threats with details about the controls, remediation suggestions, alert history, and whether or not your network is compliant.
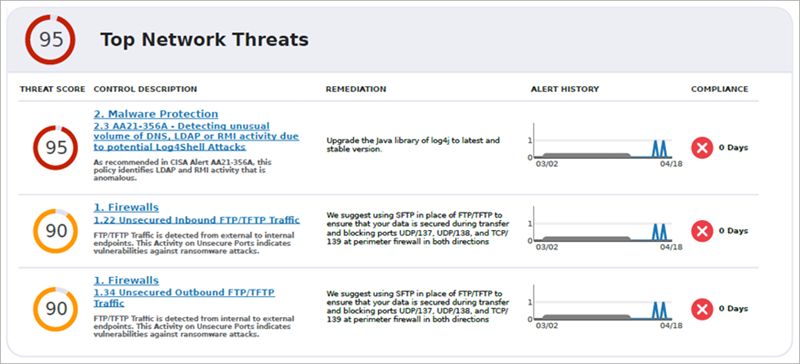
To view more information about a specific control, click the control name to go to the Objective and Control Detail sections.
Objective and Control Details
The Objective and Control Detail sections show additional detail for each of the defense objectives included in the report. Each section identifies the name of a defense objective, its compliance status, and the controls that the objective is configured to include.
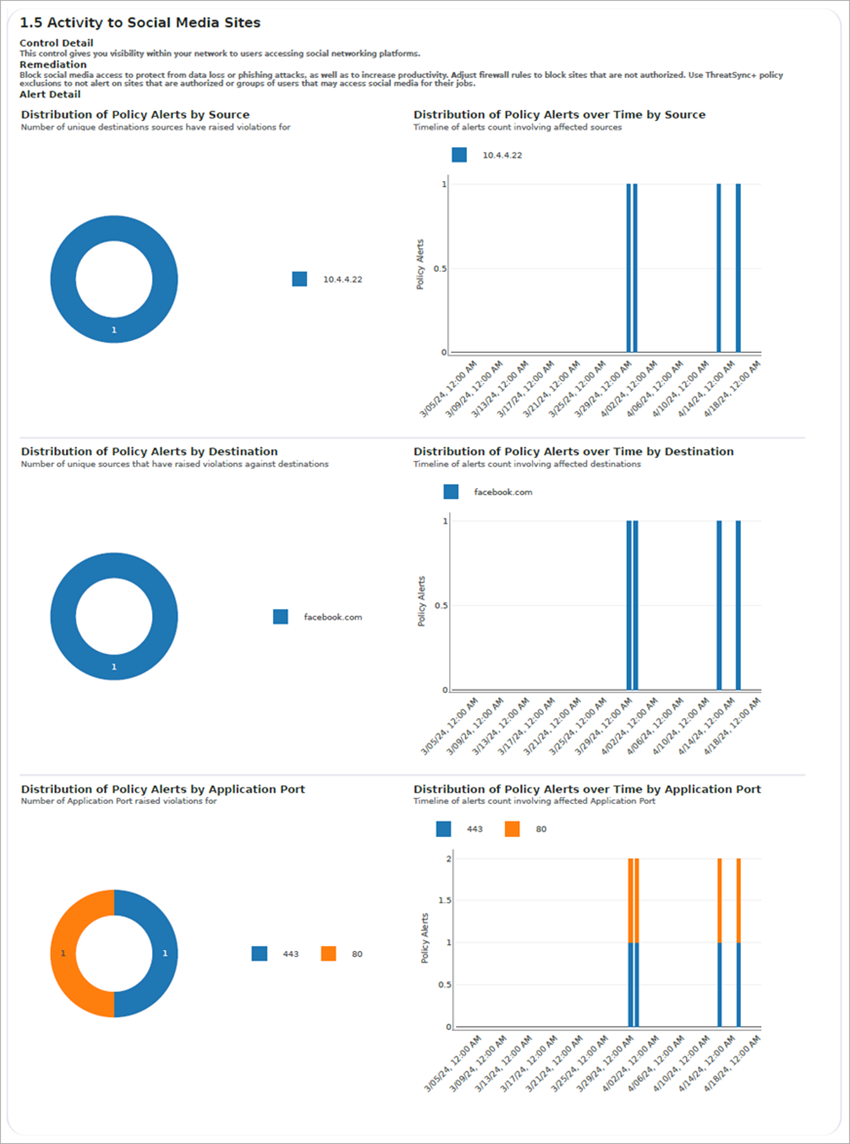
For each control, the report describes the purpose of the control, the threat score associated with violations of the control, a short remediation recommendation, and a chart with an alert history count.
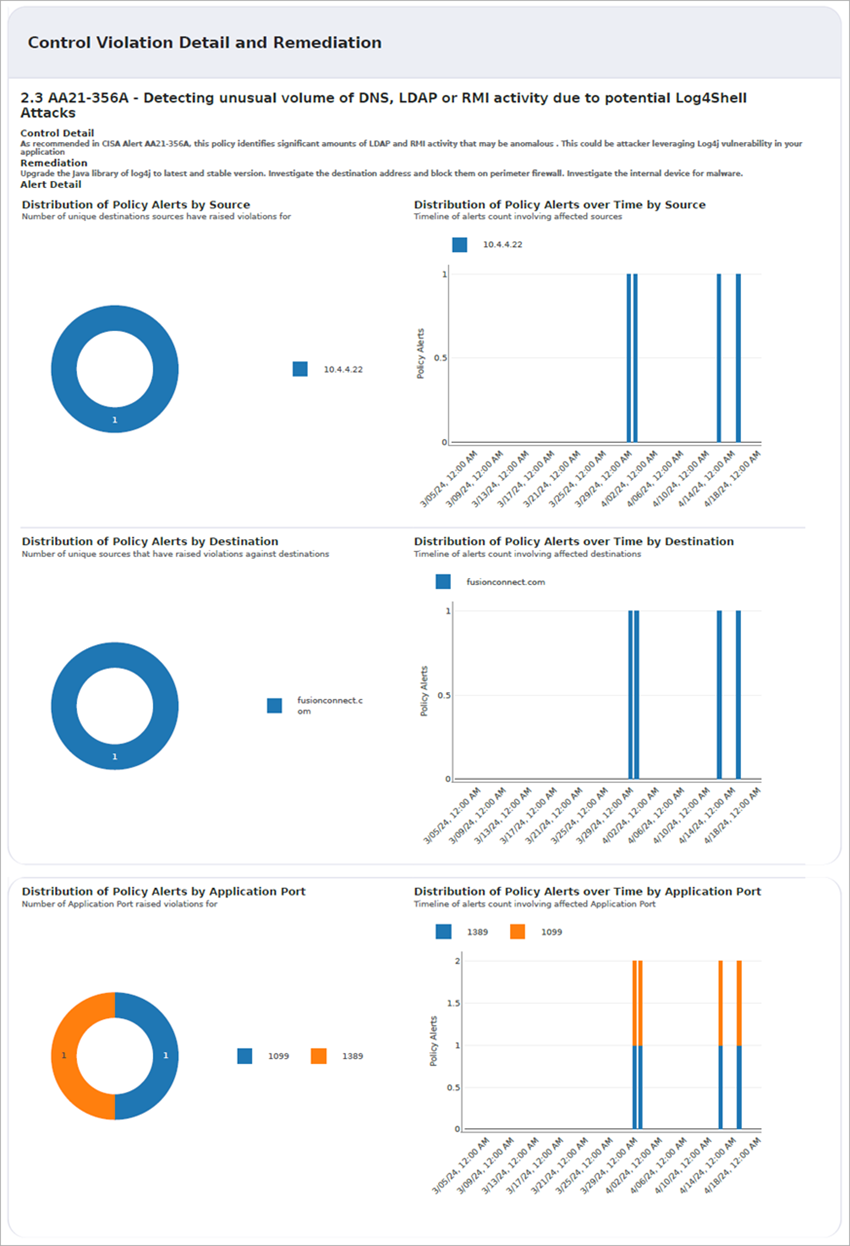
Control Violation Detail and Remediation
For controls that were violated within the report period, the report provides a detailed description of the control and remediation recommendations.
In this example in a Cyber Essentials Defense Goal report, the violation is Detecting unusual volume of DNS, LDAP or RMI activity due to potential Log4Shell Attacks.
The report provides these details:
- Control Detail — As recommended in CISA Alerts AA21-356A, this policy identified significant amounts of LDAP and RMI activity that might be anomalous. This could be an attacker leveraging a Log4j vulnerability in your application.
- Remediation — Upgrade the Java library of Log4j to the latest, stable version. Investigate the destination IP address and block it on the perimeter firewall. Investigate the internal device for malware.
Ransomware Prevention Defense Goal Report