Applies To: ThreatSync+ NDR
The ThreatSync+ NDR Executive Summary report provides a high-level overview of the threats and vulnerabilities that ThreatSync+ NDR detects. The report includes an overall network threat score and shows you changes in the trend of that score over time. Lower scores indicate that you might not be fully protecting your network. Improvement in your threat score over time demonstrates that you are using the capabilities of ThreatSync+ NDR to monitor and detect threats.
The first section of the report provides a threat assessment overview:
Report Period
The report period shown at the beginning of the report represents the data that is used to generate the report. Common report periods are one week and one month.
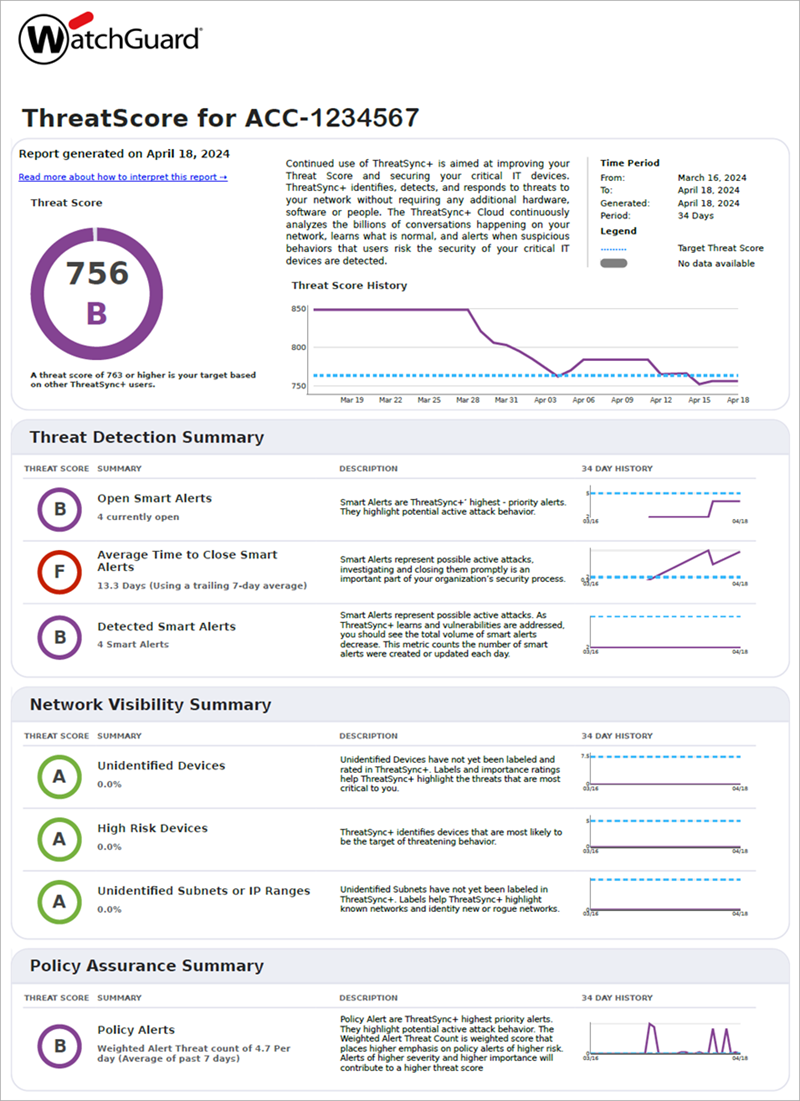
Threat Score
ThreatSync+ calculates threat scores on a scale of 300 to 850. The score is an average of metrics that apply to your network. You can also view your score as a grade from A to F.
Your threat score reflects how well protected your network is. Higher scores indicate that ThreatSync+ has detected few threats and vulnerabilities and that your network visibility is strong.
Target Threat Score
The target threat score provides a goal that you should aim to meet or exceed. The target is based on our experience with many customer networks and represents a B grade (Very Good).
How to Use This Report
Continued use of ThreatSync+ NDR is aimed at improving your threat score and securing your critical IT devices. This report provides you with an overview of your network that enables you to pinpoint threats and vulnerabilities.
Threat Scores
Your Threat Score provides you with an overall measure of network health measured by the threats and vulnerabilities that ThreatSync+ NDR detects. The score enables you to track your progress over time and compare your network to that of other ThreatSync+ NDR users. The score is calculated on a scale of 300 to 850. Your health grade reflects your performance compared to others. Most get a B grade, but we should all aim for an A grade.
Metric Targets
The targets you should aim to meet or beat for these metrics might vary based on the size of network and the type of organization. ThreatSync+ NDR assigns these targets based on what we know about your organization and sites similar to yours.
The Trend Chart for each metric shows the target value in a separate series on the chart. View your report to see what target ThreatSync+ NDR recommends you aim for. If you meet the target, you will earn a B grade. If you exceed the target, you can earn an A grade.
The ThreatSync+ NDR Executive Summary report includes these sections:
- Threat Detection Summary
- Network Visibility Summary
- Policy Assurance Summary
- ThreatSync+ NDR Executive Summary Report
- Network Visibility Detail
- Policy Assurance Detail
To configure how ThreatSync+ NDR calculates the threat score shown in the report, and to specify which metrics the report includes, follow the steps in Configure the Executive Summary Report Settings.
You can schedule WatchGuard Cloud to run ThreatSync+ NDR reports automatically and email the reports to specified recipients. You can also download scheduled reports from WatchGuard Cloud. For more information, go to Schedule ThreatSync+ Reports.
Threat Detection Summary
The Threat Detection Summary section provides an at-a-glance overview of threats to your network.

Threat Detection metrics encourage you to review and respond to ThreatSync+ NDR Smart Alerts. The metrics track how many Smart Alerts are open, how promptly you address them, and how much time ThreatSync+ NDR saves by monitoring potential threats so you do not have to.
Network Visibility Summary
The Network Visibility section of the report provides information about your network and assets:

Network Visibility metrics help you to keep up with the identification of the important subnets and devices in your network. When you tell ThreatSync+ NDR which assets and subnets are most important to you, ThreatSync+ NDR can provide more effective threat information. When you label the assets and specify their roles, ThreatSync+ NDR can automatically detect policy violations for those types of systems. ThreatSync+ NDR also uses subnet labels to more effectively identify rogue devices and unknown threats.
Policy Assurance Summary
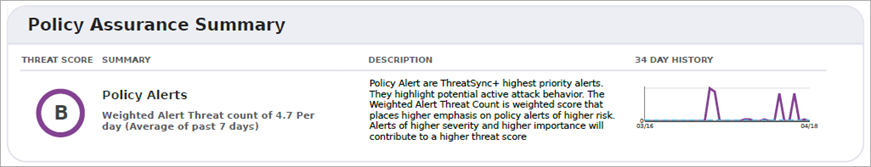
The Policy Violation metric tracks how many violations ThreatSync+ NDR detects in your network. The polices that you enable help to identify traffic that represents unauthorized activity. Enable policies that help you to identify errors and misconfiguration in your other security tools, such as firewalls, EDR, and asset management systems. This helps you to quickly identify when these tools do not block unauthorized traffic.
The weighted policy alert threat score is a weighted score that places higher emphasis on policy alerts with higher risk. Policy alerts with higher severity and higher importance contribute to a higher overall threat score.
Threat Detection Detail
The Threat Detection Detail section provides details of Threat Detection metrics.
This section includes this information:
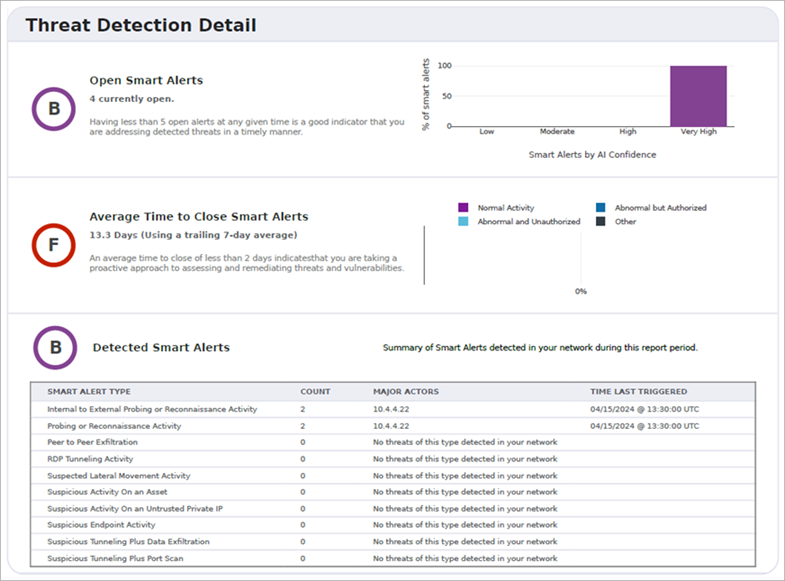
Open Smart Alerts Metric
The Open Smart Alerts Metric grades you on how many Smart Alerts you currently need to review and act on. Smart Alerts indicate potential threats to your network. To raise your score, make sure you review, remediate, and close Smart Alerts. The trend chart shows you how the number of open alerts has changed over the previous 14 days.
Average Time to Close Smart Alerts
The Average Time to Close Smart Alerts metric tracks how long Smart Alerts remain open. To raise your score, respond to and close Smart Alerts quickly. The target for a B grade is two open Smart Alerts at any given time.
The chart shows the reasons you specified when you closed the Smart Alerts. There are four possible reasons:
- Abnormal and Unauthorized — This is a real threat that requires investigation. ThreatSync+ NDR correctly identified abnormal activity and this activity is not authorized on your network. You do not recognize the activity as part of your authorized business activity.
- Abnormal and Authorized — ThreatSync+ NDR correctly identified abnormal activity but you understand the source of the activity and know that it is authorized on the network. For example, you might have performed a network scan as part of your own tests.
- Normal Activity — This activity is expected on the network. When you close these Smart Alerts, you can configure ThreatSync+ NDR to suppress future alerts.
- Other — You do not know what the Smart Alert is. It might be a threat but you are unable to determine the root cause. When you close these Smart Alerts, you can provide more detail so that ThreatSync+ NDR can better determine whether this is a risk.
Manual Effort Saved
The Manual Effort Saved metric indicates the amount of time ThreatSync+ save through the automatic review of potential threats and vulnerabilities. This calculation uses the number of Smart Alerts and behaviors detected by ThreatSync+ and assumes that each detection saves you several minutes of manual review of flow logs to detect anomalous activity and potential threats. This metric includes only activity that you do not have to look at. We estimate that you save one hour for every unconfirmed Smart Alert that ThreatSync+ detects and save 15 minutes for every Orphaned Behavior. The maximum value is capped at 10 person days each week. To keep your score high, make sure that you actively monitor your network and that your collectors constantly feed data to ThreatSync+.
Smart Alert Summary
The Smart Alert Summary provides a quick view of the types of Smart Alerts seen during the report period. Each row summarizes the Smart Alerts that occurred for that type of threat and shows this information:
- Status — Indicates if there are many occurrences, a couple of occurrences, or no occurrences.
- Major Actors — Indicates how many of your internal assets or systems were involved in the potential threats.
- Time First Seen — Shows you when Smart Alerts of this type were first seen. The time might precede the report period if the Smart Alert time span partially covers the report period.
- Time Last Triggered — Shows you when Smart Alerts of this type were last seen.
Network Visibility Detail
The Network Visibility Detail section provides details about your network.

This section includes this information:
Your Network
Your Network provides basic statistics about the devices ThreatSync+ NDR can identify. Internal IP addresses are those that are part of your organization. ThreatSync+ NDR identifies internal IP addresses as those with private IP addresses or those you explicitly labeled as internal in the subnet settings. Trusted internal IP addresses are those that have been labeled, either automatically through ThreatSync+ NDR asset discovery, or manually through subnet settings.
External IP addresses are all IP addresses that are not internal. These are the public IP addresses that your employees or users communicate with.
This section also includes some basic statistics on the amount of data ThreatSync+ NDR identifies as it moves across your network. Total traffic is the byte count of data monitored. Flow counts reflect the total number of conversations between pairs of IP addresses and ports during the report period.
Unidentified Assets
The Unidentified Assets metric indicates the percentage of assets that ThreatSync+ NDR detects that you have not identified. An important part of network visibility is the role a device performs in your network. When you identify your known assets, ThreatSync+ NDR can focus more on critical and unknown assets, and not notify you about devices that are not important. Keep the percentage of unidentified assets low so that when rogue assets appear, you can easily discover them. To keep the percentage low, review the device suggestions on the Discover page in the ThreatSync+ UI and accept those that are important in your network.
High Risk Assets
The High Risk Assets metric identifies assets that have high risk levels and indicates what percentage of all defined current assets are high risk.
These factors contribute to an increase in risk level for an asset:
- The asset is a major or minor actor in open Smart Alerts and behaviors
- High numbers of anomalous events involve the IP addresses of the asset
- The asset is labeled as important
The accompanying chart shows you the common roles assigned to your high and low risk assets.
To keep this metric low, close Smart Alerts in a timely manner, remediate threats so that future Smart Alerts do not occur, and set your asset importance levels accurately so that unimportant assets do not create a false sense of risk.
Unidentified Subnets or IP Ranges
The Unidentified Subnets or IP Ranges metric indicates the percentage of subnets or IP address ranges that ThreatSync+ NDR detects but you have not yet identified. Knowledge of the active subnets in your network is a critical foundation to help ThreatSync+ NDR understand the devices in your network. A rogue subnet can indicate an unauthorized router in your network or an unauthorized configuration change. Keep the percentage of this metric low so that when unexpected changes occur, you can respond to them quickly. To keep the metric low, review the subnet suggestions on the Discover page in the ThreatSync+ UI and accept those that are important in your network.
Policy Assurance Detail
The Policy Assurance Detail section provides details about policy alerts and common policy violations.

The Policy Violation Metric tracks a seven day trailing average of the count of violations that occur each day. ThreatSync+ NDR evaluates each policy periodically, at most once every 30 minutes. Each failure of the policy rule counts as a violation.
For example, if one internal device communicates to a prohibited country, it can violate the Activity to Blocked Countries rule once every evaluation period. If two internal devices communicate to the same prohibited country, ThreatSync+ NDR generates two violations.
The trend shows the history for a 14 day period and includes policies with and without violations. Policies that are not activated do not show in the trend.
At first, you might have a high volume of violations as you experiment with which policies are most helpful to protect your network. Violations should only trigger when activity violates an important policy. Enable those policies that alert you of malicious activity and drive you to take action. Tune the policies and zones to only alert on what is important. To improve your score on this metric, reduce your daily policy count to two or fewer for a small network.
The Top 5 most Common Violations chart identifies which policies triggered the most violations over the report period. Only the top five policies are included. The x axis is a count of violations.
The Violations by Category chart identifies which types of policies triggered the most violations over the report period. If you assign categories to reflect the types of policies you enforce, you can get a clear view of the types of issues that are most common in your network.
Because the count of active policies might grow to be quite large over time, group the policies by category to provide a quick way to understand where your network weaknesses might be.
The Assets or IPs with Most Violations chart identifies which systems in your network triggered the most violations over the report period. Only the top five systems are included. The x axis is a count of violations.
Recommendations to Improve Your Executive Summary Report Threat Score
If you perform regular, simple maintenance and respond quickly to Smart Alerts and policy alerts, you can keep your score high. A high score enables ThreatSync+ NDR to be most effective and is also a metric for compliance.
Review these recommendations to maximize your Executive Summary report threat score:
Close Smart Alerts
Respond to Smart Alerts quickly to improve your score. When you review, respond, and remediate potential threats, you keep your network safe. A large list of open Smart Alerts indicates that you have not responded to threats to your network.
When you are responsive to alerts, your Time to Close improves. If you respond quickly, assess the threat and perform remediation actions, you can close Smart Alerts promptly.
Review Unidentified Asset Suggestions
To help ThreatSync+ NDR make better decisions about the seriousness of threats, identify your important assets. You respond differently to an attack on a critical asset than a non-critical asset. When you define assets and assign importance levels to them, ThreatSync+ NDR can better prioritize alerts.
Over time, new assets join your network and existing assets change roles. The Discover page in the ThreatSync+ UI shows you when this occurs so you can create a new asset or update an existing one.
Asset suggestions recommend one these actions:
- Add a new asset that has not yet been configured.
- Add an additional role to an existing asset.
- Remove a role from an existing asset.
If you do not recognize a suggested asset, it might be unauthorized. You can tag it and take corrective action immediately.
Review Unidentified Subnet Suggestions
When you label subnets, it makes it easier to recognize different parts of your network. For example, IP addresses are difficult to keep track because they look similar. If you attach organization names and tags to your internal subnets, you can label them to make it easier to understand the potential threats that ThreatSync+ NDR shows in Smart Alerts, behaviors, and policy alerts. Like assets, subnet suggestions show on the Discover page.
Only Define Policies that Make Sense for Your Network
Policy alerts can tell you when activity in your network violates an information security policy that you have established. It is important to create policies that reflect the accepted practices of your network or you will constantly need to review policy alerts that are not important to you. For example, if your organization has a clear policy that access to a specific social media site is prohibited, enable that policy. If there is no such prohibition, disable that policy.
Your policies should reflect your firewall rules and any other security enforcement tools you use. Use ThreatSync+ NDR policies as a way to alert you when your security systems are broken. When properly configured, your ThreatSync+ NDR policies can enforce compliance with your enterprise information security policies.
Use zones to reduce the number of IP addresses, organizations, domains, and so on that a policy covers so that you only enforce rules for those systems that are required. For example, instead of the All Internal IP Addresses zone, create another zone that includes only the subnets that you want to receive alerts for.
You can also use domain lists to establish a clear set of public sites to receive alerts for or you can use exclusion lists to not generate alerts for specific sources or destinations that you allow to violate the policy.
Configure the Executive Summary Report Settings