Applies To: ThreatSync+ NDR
The ThreatSync+ NDR Managed Security Service Provider (MSSP) Summary Report provides an overview of key performance metrics across your managed accounts. This report provides a high-level summary of the current health of each managed account and enables you to monitor threat detection, network visibility, and policy violations.
The report period shown at the beginning of the report represents the data that is used to generate the report. Common report periods are one week and one month.
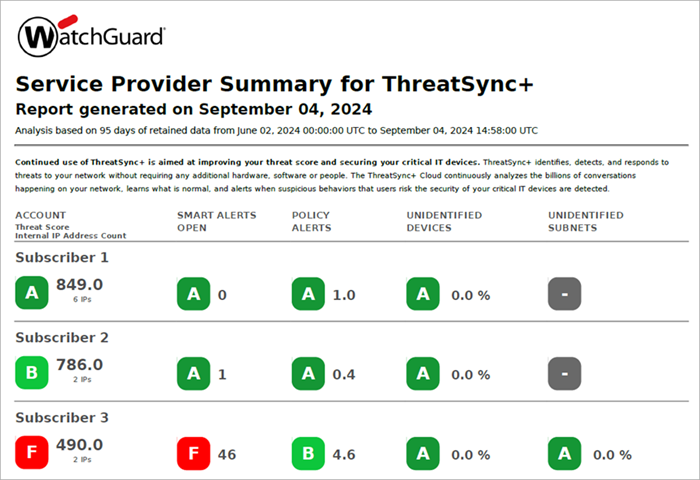
The first page of the report shows a list of selected managed accounts and these metrics for each account:
- Threat Score
- Internal IP Address Count
- Open Smart Alerts
- Policy Alerts — Weighted/Unweighted
- Unidentified Devices
- Unidentified Subnets
How to Use This Report
The Service Provider Summary Report provides you with an overview of your managed accounts that enables you to pinpoint threats and vulnerabilities. For more details, review the ThreatSync+ NDR Executive Summary Report for your managed accounts.
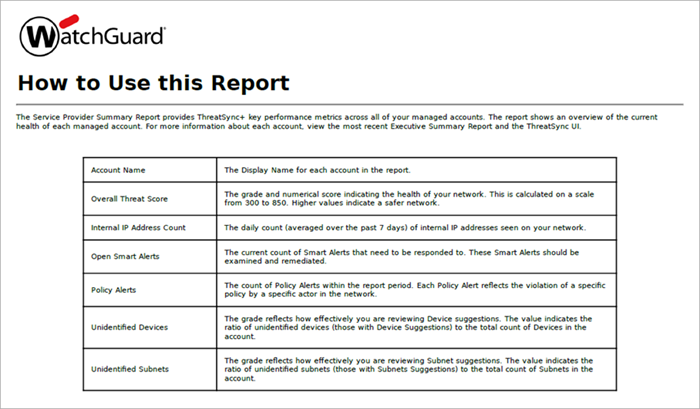
The Service Provider Summary Report shows these performance metrics for each managed account:
Overall Threat Score
Your Overall Threat Score shows an overall measure of network health, measured by the threats and vulnerabilities that ThreatSync+ NDR detects. ThreatSync+ NDR calculates threat scores on a scale of 300 to 850. The score is an average of metrics that apply to your network. You can also view your score as a grade from A to F.
Your threat score reflects how well protected your network is. Higher scores indicate that ThreatSync+ NDR has detected few threats and vulnerabilities and that your network visibility is strong.
To configure how ThreatSync+ NDR calculates the threat score shown in the report, and to specify which metrics the report includes, follow the steps in Configure the Executive Summary Report Settings.
Internal IP Address Count
The daily count of internal IP addresses associated with the network of the managed account. This number is averaged over the last seven day period.
Open Smart Alerts
The Open Smart Alerts metric grades you on how many Smart Alerts you currently have to review and act on. Smart Alerts indicate potential threats to your network. To raise your score, make sure you review, remediate, and close Smart Alerts.
Policy Alerts — Weighted/Unweighted
The Policy Violation metric tracks how many violations ThreatSync+ NDR detects in your network for the report period. The polices that you enable help to identify traffic that represents unauthorized activity. Enable policies that help you to identify errors and misconfiguration in your other security tools, such as firewalls, EDR, and asset management systems. This helps you to quickly identify when these tools do not block unauthorized traffic.
The weighted policy alert threat score is a weighted score that places higher emphasis on policy alerts with higher risk. Policy alerts with higher severity and higher importance contribute to a higher overall threat score.
Unidentified Assets
The Unidentified Assets metric indicates the percentage of assets that ThreatSync+ NDR detects that you have not identified. An important part of network visibility is the role a device performs in your network. When you identify your known assets, ThreatSync+ NDR can focus more on critical and unknown assets, and not notify you about devices that are not important. Keep the percentage of unidentified assets low so that when rogue assets appear, you can easily discover them. To keep the percentage low, review the device suggestions on the Discover page in the ThreatSync+ NDR UI and accept those that are important in your network.
Unidentified Subnets or IP Ranges
The Unidentified Subnets or IP Ranges metric indicates the percentage of subnets or IP address ranges that ThreatSync+ NDR detects but you have not yet identified. Knowledge of the active subnets in your network is a critical foundation to help ThreatSync+ NDR understand the devices in your network. A rogue subnet can indicate an unauthorized router in your network or an unauthorized configuration change. Keep the percentage of this metric low so that when unexpected changes occur, you can respond to them quickly. To keep the metric low, review the subnet suggestions on the Discover page in the ThreatSync+ NDR UI and accept those that are important in your network.