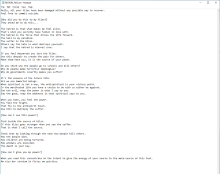
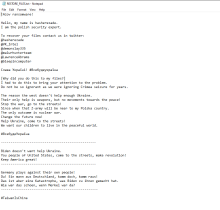
This ransomware is probably only classified as such because it drops a ransom note. There are two versions of Azov, and neither of the ransom notes indicates that a ransom can be paid to decrypt files. To solidify the point, no communication method is provided, and the files aren't encrypted; they're overwritten in 666-byte intermittent chunks that can't be reversed. Azov is a wiper and doesn't pretend to be ransomware other than the file name - RESTORE_FILES.txt. The contents of the ransom note attempt to pin security researcher Hasherezade as the operator. Also, the note tells victims to contact other security researchers on Twitter, but they had no part in this.
Whatever the ransom note says, the wiper was intended to destroy any system it managed to infect. Upon infection, it would attempt to spread and inject itself into legitimate 64-bit executables, mainly msiexec.exe. Researchers from Check Point Research have discovered over 17,000 executables uploaded to VirusTotal, and as we all know, that's not the entirety of all infections.