Green Mountain Grill Security Analysis
Automated smokers like the Green Mountain Grill (GMG) Davy Crockett are great for smoking different meats and other foods without having to tend the grill during the entire process. GMG has pushed this idea further with a WIFI controller that monitors and controls the grill. Now, one doesn’t even need to leave the couch to maintain the grill. Unfortunately though, this convenience comes with a price.
The setup of the grill consists of downloading an app to your phone and connecting to the grill on its own broadcasted Wi-Fi network. Using the app, you can add the grill to your home Wi-Fi network. After setup, the app controls power and temperatures of the food and grill. The app is also used to update the firmware on the grill wireless controller. The firmware update connects on a serial connection over port TCP 8080.
Grill Wireless Controller Analysis
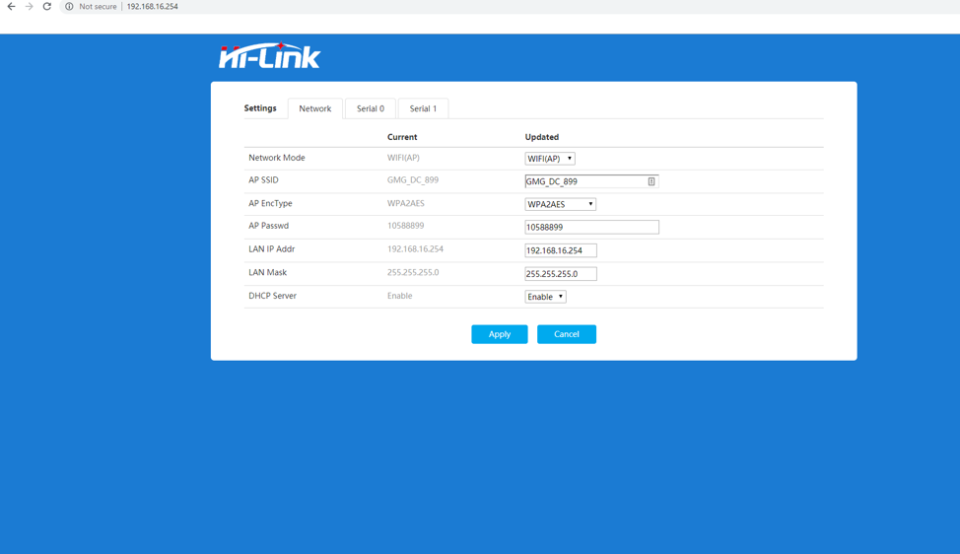
As with most IoT devices, we started our analysis with a port scan using NMAP. NMAP showed that TCP ports 80, 8080, and 8181 are open and responded to http requests. When visiting 8080, and 8181 we get a 404 response, which means they were running an HTTP server but there is no page to load. Port 80 though, had a login window. The username and password were not difficult to guess. We quickly found the user was “admin” and the password was “admin.” These credentials allowed us direct access to the HLK-RM08K Wi-Fi chip. We didn’t do any further testing on this chip since we found easier ways to compromise the grill.
Communication to the grill’s wireless controller did not require, or even support authentication, allowing anyone on the local wireless network to take control of the device within the firmware limits. As a proof of concept, we connected to the grill on port 8080 and were able to change the temperature of the grill without using the app or authenticating. We were also able to send a shutdown command, to which the grill responded with “OK” and then shutdown.
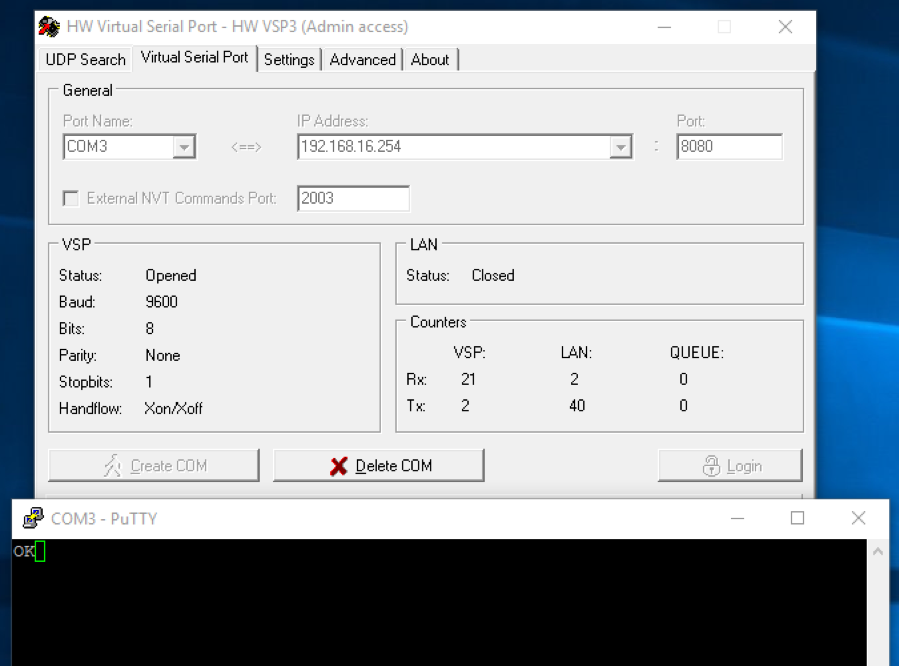
Further analysis and teardown of the controller revealed a STM8207CB microcontroller, the brain behind the grill. Additionally, we found a SWIM connector which enabled direct access to the microcontroller We also found the HLK-RM08K Wi-Fi chip mentioned earlier, which is often used in small WIFI to serial connection projects.
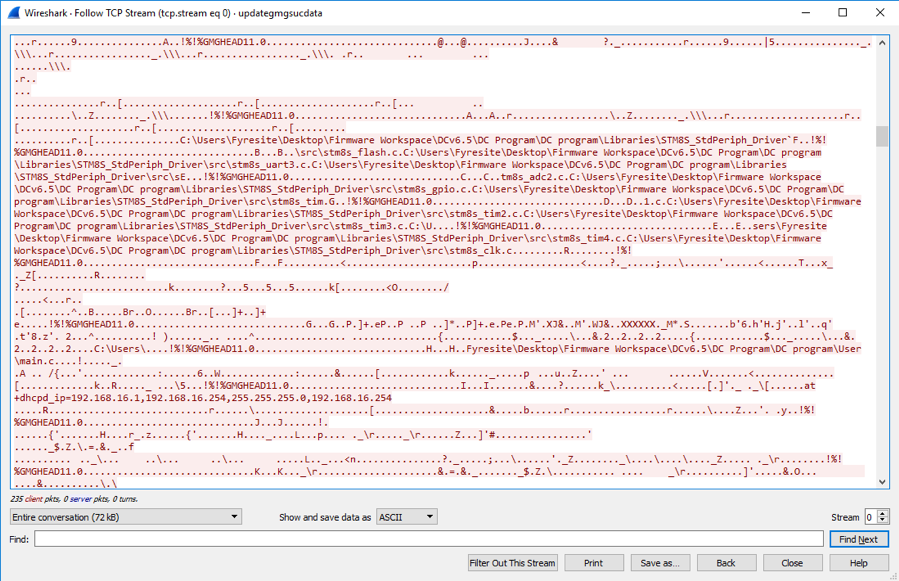
GMG has the ability to release firmware updates to the wireless controller over the wireless network. We ran a packet capture to analyze the traffic over WIFI for this device while updating the firmware. Inspecting this traffic, we found file paths, names, and other indications of an unencrypted connection. As it turns out, the firmware is sent in clear text (unencrypted) and without any authentication. Though outside the scope of this analysis, we suspect someone could spoof the server and push custom firmware to this device.
Because the wireless controller does not authenticate firmware updates, with local access we were able to install a custom firmware build that bypassed temperature limits. We suspected we wouldn’t be able to read the existing firmware off the microcontroller because the chip had a read fuse, which manufacturers often “blow” to lock down that possibility. As it turns out, we found the manufacturer did not set the read fuse.
We contacted GMG support to disclose the vulnerabilities and work towards a resolution. After a few initial responses confirming that they received our vulnerability report and were analyzing the issues, we stopped receiving replies. We believe in a responsible disclosure process, where we work with manufacturers to resolve security flaws before public disclosure. But after much more than our typical 90 day disclosure timeline without any response, we have decided to release these vulnerabilities publicly so that affected consumers can take additional steps to secure their grills.
To highlight the specific vulnerabilities and potential impact.
- The grill wireless controller lacks authentication for settings modifications. An attacker could damage the grill by forcing the grill to remain on for a long period of time at high heat.
- The grill lacks encryption and authentication for firmware updates. An attacker with network access to the grill could load custom firmware to bypass basic safety features like temperature limits, which could cause the grill to overheat and become a fire hazard.
- Additionally, an attacker could use a custom firmware update to add a backdoor to without the user knowing. This could allow the attacker to modify the grill indefinitely.
Mitigation Suggestions
As with most IoT devices, owners of the GMG Davy Crockett and similar grills must take additional security steps. This includes connecting the grill to a segmented wireless network and heavily restricting network access to and from that network. By restricting network access, you can prevent an attacker from maliciously accessing the grill wireless controller or prevent them from pivoting from an already infected device to other systems on the same network.
Disclosure Timeline
10/7/2018 Vulnerabilities discovered
10/9/2018 Reported to manufacturer
10/22/2018 Report confirmed by manufacturer
1/7/2019 Manufacturer contacted for update before public disclosure
5/31/2019 Public Disclosure