Cybersecurity News: Automated Ransomware Attacks, U.S. No Fly List Leaked, and A.I. Detecting A.I.
Welcome to another iteration of Cybersecurity News. The fairly new and unorthodox, semi-monthly news article that highlights a handful of noteworthy cybersecurity-related stories and provides extra references and resources to do further research if you desire. We aim to solidify a more concrete release schedule going forward and will release more information once we have it. For this post we cover six stories covering artificial intelligence, a leak of TSA's No Fly List, cryptocurrency hacks, and ransomware. First, we begin with an ongoing development on malware campaigns leveraging Microsoft's OneNote.
1) .One File to Rule Them All
Ever since Microsoft disabled macros in Office documents in July of 2022, attackers have sought another avenue into networks via endpoints. A few months ago, and continuing today, researchers discovered a plethora of attacks using .lnk and .iso files. Now, the file of choice appears to be .one and .onepkg, used by Microsoft's OneNote office solution. The delivery system of choice, as with most breaches, is primarily phishing via email. Social engineering attacks such as phishing remain the point of weakness for organizations, with an estimated 80-90% of all breaches beginning with a phish. Unit 42 provides an example of this delivery and infection system.
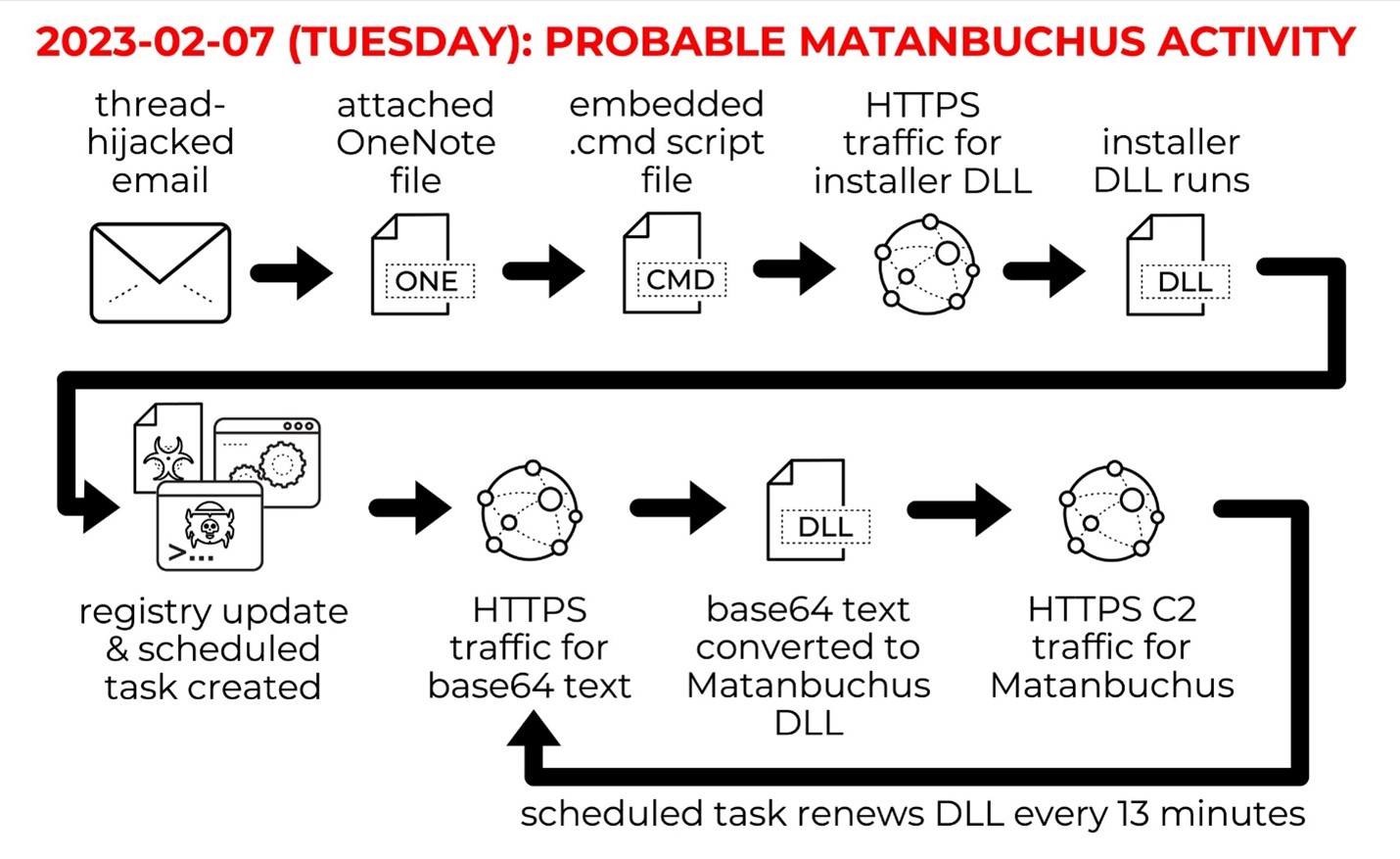
Researchers speculate that the move to .lnk, .iso, and now, .one files, are a result of Microsoft disabling macros by default in Office products. An avenue previously used by attackers to deliver initial payloads. The malware of choice for attackers appears to be popular remote access trojans (RATs) such as AsyncRAT, Quasar RAT, NetWire RAT, and others. Researchers have even seen a QBot campaign utilizing OneNote files, dubbed QakNote. Proofpoint provided a breakdown of some of the campaigns that use OneNote files:
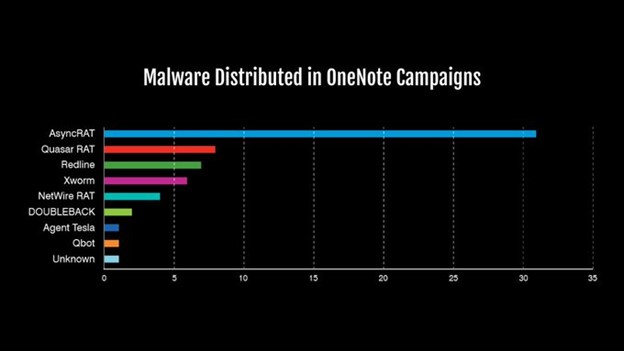
To read more about these attacks, and tools on how to detect malicious OneNote files, check the references below.
References:
- https://bleepingcomputer.com/news/security/hackers-now-use-microsoft-onenote-attachments-to-spread-malware/
- https://bleepingcomputer.com/news/security/new-qaknote-attacks-push-qbot-malware-via-microsoft-onenote-files/
- https://blog.didierstevens.com/2023/01/22/new-tool-onedump-py/
- https://github.com/DissectMalware/pyOneNote
- https://learn.microsoft.com/en-us/DeployOffice/security/internet-macros-blocked
- https://micahbabinski.medium.com/detecting-onenote-one-malware-delivery-407e9321ecf0
- https://phishingbox.com/resources/phishing-facts
- https://techcrunch.com/2022/07/22/microsoft-office-macros-blocked-default
- https://thehackernews.com/2023/02/post-macro-world-sees-rise-in-microsoft.html?es_id=5da7a164e2
- https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/trojanized-onenote-document-leads-to-formbook-malware/
- https://twitter.com/proofpoint/status/1626598662527938561
- https://twitter.com/Unit42_Intel/status/1623349272061136900
2) United States' No Fly List Leaked On Public Forum
Swiss developer and hacker "maia arson crimew" discovered an exposed Jenkins server belonging to CommuteAir. She located a 2019 version of TSA's No Fly List on this server and wrote a blog post on how she performed this breach. It was surprisingly simple. She was bored and decided to search for misconfigured or exposed servers on ZoomEye, the Chinese version of Shodan, and stumbled across the CommuteAir server. That's it!
The breach isn't as serious as it might seem. The No Fly List isn't a classified document, and the leaked list was a 2019 version. You can even search the No Fly List yourself. However, having access to the entire list in one concise CSV allowed some researchers to unveil biases against Muslim individuals. A prejudice that likely existed since the inception of the No Fly list created after the September 11th attacks. You can read more about the TSA program and the breach below.
References:
- https://dailydot.com/debug/no-fly-list-us-tsa-unprotected-server-commuteair/
- https://maia.crimew.gay/posts/how-to-hack-an-airline/
- https://no-fly-list.com/
- https://papersplease.org/wp/2023/01/20/the-nofly-list-is-a-muslimban-list/
- https://tsa.gov/travel/passenger-support/travel-redress-program
- https://www.tsa.gov/travel/security-screening
- https://en.wikipedia.org/wiki/Maia_arson_crimew
- https://www.zoomeye.org/
3) OpenAI Releases Tool to Detect AI-Generated Text
When OpenAI released ChatGPT on November 30, 2022, it took the tech world by storm, surpassing a million users by December 4, 2022, less than a week after release. ChatGPT allows users to ask open-ended questions to an extensively trained artificial intelligence (A.I.) engine and quickly receive an answer. The image below displays how ChatGPT looks and responds to those unfamiliar with the tool.
ChatGPT doesn't get all the answers right, but it does seem to do well enough for students to use and abuse the product. Previously, academia focused on preventing and discouraging plagiarism, using tools such as Turnitin to detect plagiarism in papers. Turnitin is a service that accepts online paper submissions and cross-references every other paper to detect plagiarism. Simple, yet effective.
Now, with the introduction of ChatGPT, students can fine-tune their prompts and receive a non-plagiarised paper that fulfills the objectives of the assignment. However, OpenAI quickly responded with another tool to combat the misuse of AI-generated text called AI Text Classifier. This tool uses A.I. to detect A.I.-generated text. Turnitin states that it can also detect A.I.-generated text in students' assignments, but it's unclear if they are using AI Text Classifier or have found another way to detect generative text.
This is just one way A.I. is altering how we solve problems and shows how unforeseen issues arise from the use of A.I.
References:
- https://businessinsider.com/turnitin-will-detect-chatgpt-answers-openai-product-teachers-ai-speech-2023-1
- https://chat.openai.com/chat
- https://en.wikipedia.org/wiki/ChatGPT
- https://fortune.com/2023/01/31/chatgpt-open-ai-new-tool-catch-students-cheating/
- https://openai.com/blog/new-ai-classifier-for-indicating-ai-written-text/
- https://platform.openai.com/ai-text-classifier
- https://theguardian.com/technology/2023/feb/01/chatgpt-maker-openai-releases-ai-generated-content-detection-tool
4) $3.8 Billion Stolen From Cryptocurrency Hacks in 2022
According to blockchain data analytics company, Chainalysis, 2022 was the biggest year yet for crypto hacking, almost surpassing $4 billion in stolen funds. The $3.8 billion in stolen funds is an increase from the $3.3 billion stolen the year prior. It is interesting to note that the number of known blockchain-based attacks decreased from 2021 to 2022. The first notable decrease in year-over-year attacks since Chainalysis began recording this data. The overall year-over-year data, taken from their blog post on the topic, is provided below.
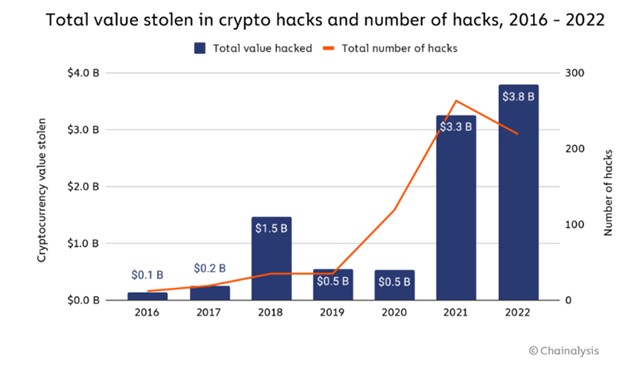
Common questions surrounding this topic include: what are "crypto hacks," and where are these illicit funds being siphoned? According to the same blog post by Chainalysis, vulnerabilities in Decentralized Finance (DeFi) protocols are responsible for most hacks, especially within the last two years. Moreover, the United States government and Chainalysis agree that North-Korean state-sponsored actors are performing these attacks, mainly Lazarus Group. Lazarus group is responsible for large cryptocurrency heists, including the Axie Inifnity's Ronin Bridge exploit, providing the group with $620 million, and the Harmony Bridge hack, resulting in around $100 million stolen.
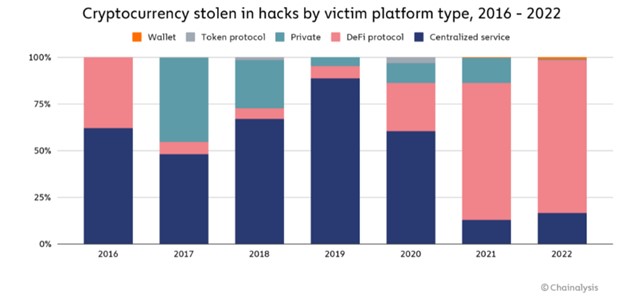
The public ledger, or blockchain, allows users to track any transaction on any blockchain. So, why is cryptocurrency stereotyped as currency for criminals? Chainalaysis states that only around 0.24% of all cryptocurrency transactions in 2022 involved criminal activity. The criminals who do use blockchain technology, such as ransomware groups, often use cryptocurrency mixers/tumblers to obfuscate the sender's address, making it more difficult to track. This is the primary goal of companies like Chainalysis – to create tools and technologies to counteract cryptocurrency-based crime. Thankfully, the U.S. Department of the Treasury's Office of Foreign Assets Control (OFAC) has sanctioned some significant mixers, including Tornado Cash and Blender. However, it appears that Lazarus Group continues to use mixers such as a newer one called Sinbad, the supposed successor of Blender.
I'll finish with an interesting anecdote provided by the Washington Post. In 2020, North Korean exports amounted to $142 million. If we take only two of the attacks attributed to the Lazarus Group, the Ronin Bridge and Harmony Bridge hacks, they've theoretically collected around $720 million. However, some of this has been sanctioned or seized. Knowing this, one could theorize that cryptocurrency hacks primarily drive North Korea's economy.
Check the references below to learn more about Lazarus Group and cryptocurrency hacks.
References:
- https://attack.mitre.org/groups/G0032/
- https://bleepingcomputer.com/news/cryptocurrency/620-million-in-crypto-stolen-from-axie-infinitys-ronin-bridge/
- https://bleepingcomputer.com/news/security/lazarus-hackers-use-new-mixer-to-hide-100-million-in-stolen-crypto/
- https://blog.chainalysis.com/reports/2022-biggest-year-ever-for-crypto-hacking/
- https://cbsnews.com/news/reddit-wallstreetbets-founder-jaimie-rogozinski-suing-over-ban-copyright/
- https://go.chainalysis.com/2023-crypto-crime-report.html
- https://home.treasury.gov/news/press-releases/jy0768
- https://home.treasury.gov/news/press-releases/jy0916
- https://justice.gov/opa/pr/justice-department-seizes-and-forfeits-approximately-500000-north-korean-ransomware-actors
- https://oec.world/en/profile/country/prk
- https://washingtonpost.com/politics/2023/02/14/sanctioned-cryptocurrency-tool-appears-reemerge-under-new-name/
5) CISA Warns About Ransomware Attacks on U.S. and Republic of Korea Healthcare Sector
On February 9th, the United States Cybersecurity & Infrastructure Security Agency (CISA), in coordination with other federal agencies from the United States and the Republic of Korea (ROK), issued a Cybersecurity Advisory (CSA) highlighting ransomware activities against the healthcare industry and other critical infrastructure entities. The advisory focuses on the tactics, techniques, and procedures (TTPs) of threat actors from the Democratic People's Republic of Korea (DPRK) with a focus on two specific ransomware families – Maui and H0lyGh0st. What's interesting is that CISA released a similar advisory on Maui ransomware in July of 2022. So, this has been ongoing for a while now. The group linked with the Maui ransomware operation is the DPRK-based group known as Andariel.
The other side of the CISA advisory is the group known as H0lyGh0st. Microsoft has tracked this group since June 2021 and dubs them DEV-0530 (Maui has been around since April 2022). H0lyGh0st is known to have developed at least two ransomware variants – SiennaPurple and SiennaBlue. Regardless of the variant, the group uses a dark web domain to perform extortion communications with victims and asks for cryptocurrency in exchange for the decryption of files. Cryptocurrency that will likely be sent to a mixer, as described above.
To read more about those ransomware strains, see the Microsoft post in the references below.
References:
- https://bleepingcomputer.com/news/security/maui-ransomware-operation-linked-to-north-korean-andariel-hackers/
- https://blogs.blackberry.com/en/2022/08/h0lygh0st-ransomware
- https://cisa.gov/uscert/ncas/alerts/aa22-187a
- https://cisa.gov/uscert/ncas/alerts/aa23-040a
- https://microsoft.com/en-us/security/blog/2022/07/14/north-korean-threat-actor-targets-small-and-midsize-businesses-with-h0lygh0st-ransomware/
- https://stairwell.com/wp-content/uploads/2022/07/Stairwell-Threat-Report-Maui-Ransomware.pdf
6) Automated ESXiArgs Ransomware Attack Leads to Thousands of Infections
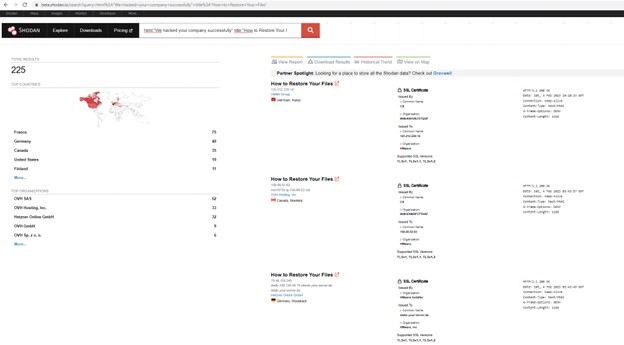
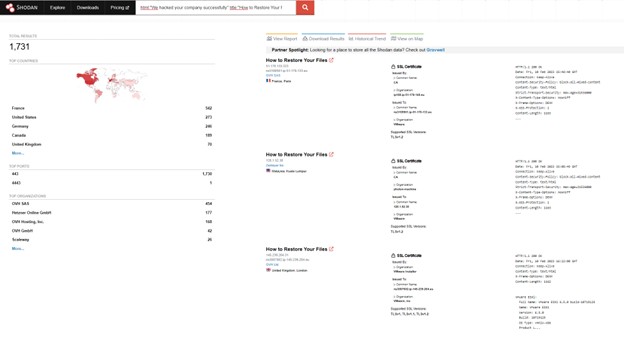
At the beginning of February, researchers, news outlets, and security organizations began sounding the alarm about ransomware attacks against VMWare ESXi servers on a broad scale. CERT-FR designated CVE-2020-3992 and CVE-2021-21974 as the exploited vulnerabilities. The WatchGuard Threat Lab and other researchers began to quickly discover that the attack was automated, based on public Shodan (credit to @1ZRR4H) and Censys searches. To determine automation, we took two images of the Shodan searches a few days apart. If you look at the top left number, you can see the number of hits on the search (the number of infections). The first image shows 225 hits, and the second shows 1,731. Around 1,500 infections over a few days is undoubtedly a sign of automation.
Search query: html:"We hacked your company successfully" title:"How to Restore Your Files"
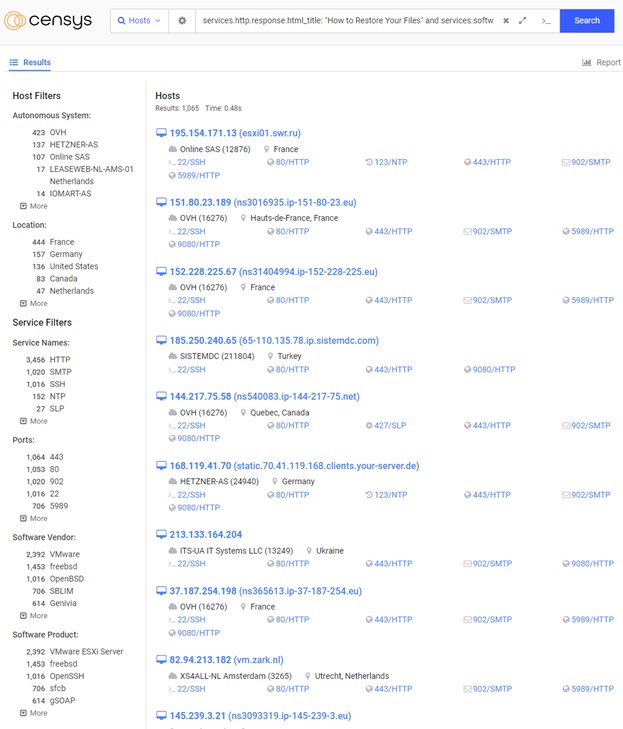
Search query: services.http.response.html_title: "How to Restore Your Files" and services.software.product=`VMware ESXi Server`
Shortly after a wave of infections, CISA created and released a recovery tool for those infected called ESXiArgs-Recover. Unfortunately, researchers discovered a new version of ESXiArgs in the wild that was immune to CISA's recovery tool; thus, beginning the cat-and-mouse game that continues as of this writing. It's unlikely CISA will release a new recovery tool for the latest ESXiArgs version because the encryption loophole appears to be fixed. So, preventing intrusion and encryption is paramount, especially because VMWare-targeted ransomware were on the rise before this occurrence.
To protect yourself from these attacks, the first and most important thing you can do is get rid of remote access to your ESXi server. This should immediately rectify any concerns you would have about this automated attack. However, if you, for whatever reason, need remote access to the server, it is recommended to keep it up to date and enforce a consistent patch policy. The automated attack only affects unpatched servers exposing the CVEs described prior. CERT-FR provides more information on the vulnerable servers.
The references below provide the search queries, public reporting, researcher's findings, and technical analyses of the ESXiArgs ransomware.
References:
- https://bazaar.abuse.ch/browse/tag/esxiargs/
- https://beta.shodan.io/search?query=html%3A%22We+hacked+your+company+successfully%22+title%3A%22How+to+Restore+Your+Files%22
- https://bleepingcomputer.com/news/security/massive-esxiargs-ransomware-attack-targets-vmware-esxi-servers-worldwide/
- https://bleepingcomputer.com/news/security/new-esxiargs-ransomware-version-prevents-vmware-esxi-recovery/
- https://blog.qualys.com/vulnerabilities-threat-research/2023/02/07/ransomware-targets-outdated-vmware-esxi-hypervisors-protect-your-systems-now
- https://cert.ssi.gouv.fr/alerte/CERTFR-2023-ALE-015/
- https://cybersecuritydive.com/news/vmware-ransomware-increase/642576/
- https://github.com/cisagov/ESXiArgs-Recover
- https://reuters.com/world/europe/italy-sounds-alarm-large-scale-computer-hacking-attack-2023-02-05/
- https://search.censys.io/search?resource=hosts&sort=RELEVANCE&per_page=25&virtual_hosts=EXCLUDE&q=services.http.response.html_title%3A+%22How+to+Restore+Your+Files%22+and+services.software.product%3D%60VMware+ESXi+Server%60
- https://www.trustedsec.com/blog/esxiargs-the-code-behind-the-ransomware/
- https://twitter.com/1ZRR4H/status/1621591855157616642
- https://twitter.com/CERT_FR/status/1621570988243652611
- https://twitter.com/gbillois/status/1622484233078833153
- https://twitter.com/herrcore/status/1624515160500060163