AnyDesk Remote Access Vendor Compromise
 On February 2nd, remote access software vendor AnyDesk disclosed they had been the victim of a cyberattack where an unknown threat actor obtained access to production systems. AnyDesk appears to have contained the incident before the adversaries were able to leverage their access into a supply chain attack against AnyDesk customers but out of an abundance of caution, they proactively revoked all security-related certificates including their code signing certificates for the AnyDesk application. AnyDesk also forced a password reset for all customers on their my.anydesk.com management portal as an an additional precaution. AnyDesk released a follow-up statement on February 7th, confirming all versions of AnyDesk obtained from official sources are safe to use, but encouraged customers to upgrade to the latest versions (7.0.15 and 8.0.8 at this time) as quickly as possible. If you are a WatchGuard EPDR or Panda AD360 customer, you can locate AnyDesk installations that need upgrading by using the Software dashboard list. After adding the General > Software list to your dashboard, search for the publisher name “philandro Software GmbH” to locate AnyDesk installations that require updating. The new publisher name for AnyDesks’ re-issued code signing certificates is now “AnyDesk Software GmbH”.
On February 2nd, remote access software vendor AnyDesk disclosed they had been the victim of a cyberattack where an unknown threat actor obtained access to production systems. AnyDesk appears to have contained the incident before the adversaries were able to leverage their access into a supply chain attack against AnyDesk customers but out of an abundance of caution, they proactively revoked all security-related certificates including their code signing certificates for the AnyDesk application. AnyDesk also forced a password reset for all customers on their my.anydesk.com management portal as an an additional precaution. AnyDesk released a follow-up statement on February 7th, confirming all versions of AnyDesk obtained from official sources are safe to use, but encouraged customers to upgrade to the latest versions (7.0.15 and 8.0.8 at this time) as quickly as possible. If you are a WatchGuard EPDR or Panda AD360 customer, you can locate AnyDesk installations that need upgrading by using the Software dashboard list. After adding the General > Software list to your dashboard, search for the publisher name “philandro Software GmbH” to locate AnyDesk installations that require updating. The new publisher name for AnyDesks’ re-issued code signing certificates is now “AnyDesk Software GmbH”. 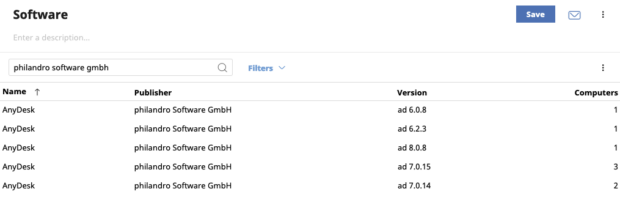 Adversaries are increasingly turning towards software vendors in the hopes of leveraging a single compromise into a wide-reaching supply chain attack. Thankfully in this case, all signs seem to indicate AnyDesk fully contained this incident with minimal impact to their customers and no compromised customer data.
Adversaries are increasingly turning towards software vendors in the hopes of leveraging a single compromise into a wide-reaching supply chain attack. Thankfully in this case, all signs seem to indicate AnyDesk fully contained this incident with minimal impact to their customers and no compromised customer data.