Cyberattack framework: What is the cyber kill chain?

In the early 2000s, Lockheed Martin defined the cyberattack chain framework to identify what adversaries must complete in order to achieve their objective. Today, we look at how the growing sophistication of adversaries and sheer number of threats is intensifying pressure on CISOs and IT teams and is increasing their workloads, which all has negative impacts on businesses and organizations. This is why the frameworks and tools that are most effective at helping IT professionals classify tactics, techniques and procedures and quickly identify threats that may be attempting a cyberattack have become so popular among the cybersecurity community, such as the cyber kill chain, which identifies distinct phases in adversaries' actions. These phases can be summarized as follows:
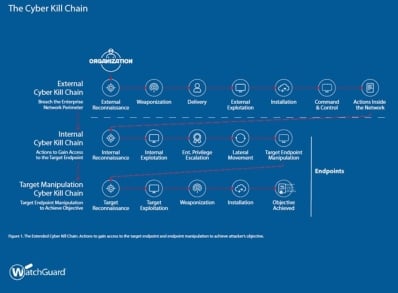
- External reconnaissance: this is the targeting stage, when adversaries focus on identifying details of the organization and the activities of its members on social media or harvest email addresses.
- Weaponization and packaging: the cyberattack can take many forms, such as exploiting web pages, customized malware, or documents that exploit vulnerabilities.
- Delivery: the operation is launched delivering the payload, which is either initiated by the target (e.g. when the user visits a website or opens a malicious file) or by the hacker (e.g. through SQL code injection).
- Exploitation: once the payload has been delivered, the malware compromises the system, generally by exploiting a vulnerability.
- Installation: in this phase, the malware acquires or searches the system for the necessary format to be able to communicate with external actors. It is usually silent during this process and attempts to gain a hold at the endpoint.
- Command and Control: adversaries take control of the installed assets through methods (usually remote) leveraging the DNS system, websites and social media.
- Actions on Objectives: this is the final phase in which adversaries damage the organization's IT assets or extract the data they were after.
There is also an extended version of the framework, which focuses on actions inside the organization. These are the two internal stages:
- Internal reconnaissance: in this stage, adversaries have access to a single device in the organization where they will look for local files, shared network resources or browser history. The objective is to find out how they can map the entire system to enable them to move inside it to seize the most valuable assets.
- Internal exploitation: adversaries take advantage of uninstalled patches, application vulnerabilities, phishing or even default credentials. This allows them to reach servers and thus escalate privileges and achieve lateral movement.
As we discussed in the eBook "Understanding Cyber Attacks,” this framework shows that malicious cyber actors set themselves objectives and use a series of resources (human, financial, etc.) to achieve them. However, the cost of these resources increases exponentially if organizations deploy advanced cybersecurity solutions capable of detecting unknown threats, and attack or behavior indicators. Hackers will succeed much less frequently or even decide not to carry out an attack at all. Conversely, when organizations are not well protected, the cost of compromising their IT assets is lower, involves fewer risks and takes less time, so these objectives will generate more profit for hackers and will be attacked more frequently.
In this sense, they should implement a multi-layered cybersecurity solution that covers network, user and endpoint security. The latter must also have a tool that deploys multiple efficient technologies, both for known attacks and for unknown and sophisticated threats. This helps ensure that the cyber kill chain is always broken. To do this, solutions must have prevention, detection and response capabilities to mitigate even the most sophisticated threats, such as unknown malware that evades traditional cybersecurity mechanisms but show anomalous behavior or exploits that take advantage of vulnerabilities present in code.


