Remote access trojans (RATs) threaten the airline industry

On 11 May, Microsoft warned on its cybersecurity intelligence Twitter account that a cyber attack campaign specifically targeting airlines and travel companies was underway. According to the Redmond-based company, the cyberattackers had managed to steal credentials, take screenshots and access webcams, obtain browsing and network data and extract all kinds of information. But how did they do it? Microsoft says that the hackers used spear phishing.
Spear Phishing
This technique is becoming more and more common. According to a study cited by the Comparitech portal, it is now used by 65% of all groups responsible for cyberattacks. Moreover, some hits have caused huge losses in the past for a variety of companies, such as the $100 million fraud that affected the giants Facebook and Google. This means it’s a serious threat to organizations of all sizes and sectors.
Spear phishing tends to have a higher success rate. Whereas standard phishing entails sending fraudulent emails indiscriminately in mass attacks while posing as a legitimate organization or person, spear phishing attacks require more effort, as they are specifically targeted at a person or organization and tend to be customized and more detailed, making them more difficult to detect. Thus, they can impersonate another member of the organization (or even the boss, which is known as CEO fraud) or a supplier or customer.
In this case reported by Microsoft, the employees of the organizations who were duped opened files apparently relating to aircraft cargo. They thought they were opening a PDF file, but they were actually opening an image containing a hidden link embedded in it that downloads malicious VBScript code. Once this code was downloaded, the malware was loaded onto their systems.
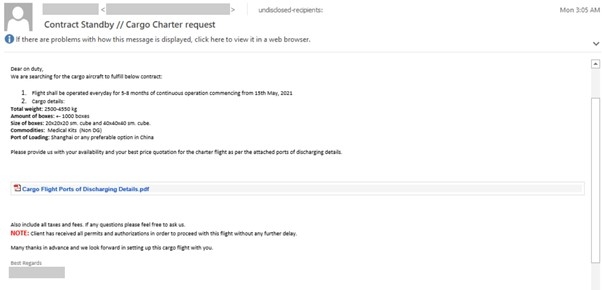
Sample of the phishing email used by the cyberattackers in their campaign. Source: Microsoft Security Intelligence
The hackers used remote access trojans (RATs), which give cyberattackers control of targeted systems remotely. These RATs connected to dynamic servers controlled by the cyberattackers and then used various fileless techniques to download or inject more code, giving them new capabilities, such as network data, using a loader called Snip3 as a tool.
What the Microsoft analysts also noticed is that they principally used SMTP port 587 to obtain the extracted data, which makes sense considering the input vector used, as it is one of the standard protocols for sending and receiving emails. This port appears secure enough, as it supports TLS encryption; however, the fact that the email is difficult to intercept or open by third parties due to this encryption doesn’t make it a threat-free vector. As these cyber attacks have shown, malware can still reach its victims, especially if they open the door to the trojan duped by spear phishing.
MSPs with network-wide security
Good cybersecurity practices in organizations are essential to reduce the chances of successful cyber attacks. If employees know how to distinguish between phishing emails and legitimate ones, they will not open the bogus ones and cyberattackers will have fewer techniques at their disposal in order to infiltrate an organization’s systems.
But it so happens that these best practices can be implemented with ease for mass phishing campaigns, as they are simpler to detect (e.g. unknown senders or misspelled texts). But they are not as easy to implement in order to combat much more personalized spear phishing techniques.
For this reason, cybersecurity cannot rely solely on human factors and increasingly needs to be supported by advanced technologies. Cases like this demonstrate the need for MSPs to provide customers with network security tools that offer comprehensive protection. The WatchGuard Firebox platform delivers that protection, with virtual or appliance firewalls, advanced SD-WAN, content inspection on HTTPS and full network visibility with WatchGuard Cloud Visibility, which provides over 100 dashboards and reports so that you can view all your activity, detect anomalies and take swift action to prevent threats. This makes incidents like the one described by Microsoft much less likely.


