AtomSilo was a ransomware group with activity only observed for a few months in 2021, beginning operations in September and ending activity towards the end of the year. Only four victims are known to have been infected with the AtomSilo ransomware. However, based on ransom notes and communication methods, there have been at least two more victims that we can't identify with certainty. The ransomware itself is very identical to LockFile, a ransomware group active a few months prior to the inception of AtomSilo. The reason for the parallels in methodology, without overlap in operations, is that AtomSilo, along with LockFile, are attributed to state-sponsored actors in China known as BRONZE STARLIGHT. The group is also known as Cinnamon Tempest, DEV-0401, Emperor Dragonfly, and SLIME34. Researchers speculate the use of ransomware attacks from this group are smokescreens for intellectual property theft. After AtomSilo seized operations, BRONZE STARLIGHT began operating the Rook ransomware, followed by Night Sky, Pandora, and others. A sign that any given ransomware is derived from BRONZE STARLIGHT is the use of HUI Loader, the group’s loader of choice.
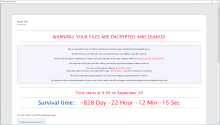
The ransomware uses a well-established hybrid encryption approach that leverages AES-256 for file encryption and RSA-4096 for encrypting the AES-256 key. This ensures that the victim has little to no chance of recovering files without the decryption key (hopefully) provided by the attackers. The ransom note name is a long string that couples a hardcoded string "README-FILE-" with the victim's computer name and a timestamp. You can view the format of that string below. Thankfully, Avast and an independent researcher named Aypex have created a decryptor for AtomSilo, which likely led to the threat actors switching to new ransomware shortly after their releases. This possibly saved victims from a six-to-seven-figure ransom based on the ransom notes from AtomSilo samples that sought these sums.
Samples (SHA-256)(6)
| Industry Sector | Country | Extortion Date | Amount (USD) |
|---|---|---|---|
| Healthcare & Medicine | Brazil | $500,000 | |
| Manufacturing | Lithuania | ||
| Healthcare & Medicine | Japan | ||
| Real Estate & Housing | Brazil |