AzzaSec (AzzaSecurity) is both the name of the ransomware and of an Italian hacktivist group. That is based on research from Threatmon, which wrote an extensive report on this ransomware and its members. The other two members are Turkish (WalterBishop_AzzaSec) and Brazilian (DmitryRansom). However, the leader—madoneputain/Friendied—is Italian. The group was first observed in late February 2024 and disbanded in August of the same year. During this time, they created ransomware with the same name as their group, but one of the samples we analyzed also went by AnonCry. Hence, the Alias of AnonCry. This name is interesting because it is seemingly meaningless, but after we analyzed other ransomware with similar characteristics, we discovered that the group likely had earlier testing ransomware iterations called BlackSkull, GhosHacker, and Anonymous, all of which are based on the NoCry ransomware builder. The primary piece of evidence of this is from the Anonymous variant that contained a debug string directly linked to NoCry. The Anonymous variant also contained AzzaSec strings. Seeing as these are all identical and there are string references, and because these were all created within the timeframe of the group's existence, we have moderately high confidence these all are related to AzzaSec. Also, the name AnonCry (Anonymous+NoCry) is another piece of evidence. Based on this evidence, we believe the public research indicating AzzaSec is based on HiddenTear to be incorrect.
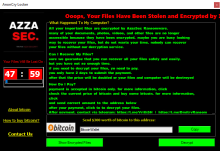
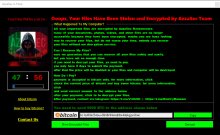
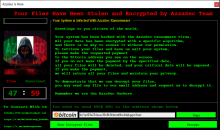
The AzzaSec group worked on a RaaS model that allowed users to purchase the encryptor as a flat fee or subscription service. This comes from a post on CrackingX by a member of AzzaSec. However, they didn't indicate if there was some revenue split or if they simply sold the ransomware encryptor. It's likely the latter. As for the ransomware encryptor, it appended both .AzzaSec and .AzzaSec_Encryptor based on the sample (all but one used .AzzaSec) and encrypted files with AES combined with SHA-512. Similar to the other ransomware mentioned in this description, the extortion amounts were all less than $100, and the maximum amount in the samples we found was $600, a far cry from other major ransomware groups. However, this isn't a surprise, considering the group's motives were hacktivism. They also were aligned with pro-Russian groups such as APT44 and Noname057(16), which commonly use DDoS attacks.