Zeoticus is believed to be the first in the line of several ransomware encryptors that has led to Zeoticus 2.0, Venus, 2023Lock, and TrinityLock. It was first reported by @siri_urz on Twitter/X at the very beginning of January 2020 (referenced below). However, samples indicate that the operators of this ransomware began Zeoticus at the earliest in December 2019, a month prior to @siri_urz reporting. Most of the other reporting was done by @Amigo_A_'s Ransomware Digest, also referenced below. The UK's National Health Service (NHS) released a public bulletin on this ransomware as well. So, there's plenty of documentation of where this string of ransomware began.
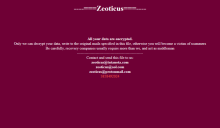
The operators used the tactic of encrypting files followed with a ransom note and changing the desktop wallpaper to advise victims on what to do. The encryption methods are slightly different than most observed, using XChaCha20 to encrypt the files, and the seldom seen curve25519xsalsa20poly1305 combinatory encryption algorithm. The ransom note tells victims to contact them via email, and there have been no reports of any ransom amounts being paid. As such, we have no information on extortion amounts, but we do have at least one sample that we analyzed and grabbed ransom note pictures from. See below.