Analyzing a Fileless Malware Loader

Thanks to WatchGuard’s Panda Adaptive Defense 360 zero-trust service, WatchGuard Threat Lab was able to identify and stop a sophisticated fileless malware loader before execution on the victim’s computer. Upon further detailed analysis by our attestation team, we identified several recent browser vulnerabilities that the malware targeted as part of its exploit chain.
Malware Behavior
The attack that WatchGuard Threat Lab analyzed lived fully in memory, making use of JavaScript [T1059.007] and PowerShell [T1059.001] to execute malicious actions. Advanced attacks like this one, that doesn’t leave artifacts on the victim’s storage drive, can evade many anti-virus engines easily by living in the computer memory out of their reach.
The attack started with a drive-by compromise [T1189] that used JavaScript embedded in a malicious website. Because web browsers run JavaScript automatically, the attack didn’t require any user interaction aside from them just visiting the site. The website itself was hosted on a domain that the threat actors appeared to set up just to host the attack.
When the victim lands on the site, the JavaScript executes an encoded PowerShell script that uses the ReflectivePEInjection module from the popular Powersploit [S0194] attack framework. The ReflectivePEInjection module loads executables and libraries into a running process on the victim’s computer [T1055.002], hiding the malware from defensive tools that don’t keep an eye on existing applications. In this case of this attack, the PowerShell script contained three encoded Portable Executable binaries. Each of the binaries exploited a different privilege escalation vulnerability to expand the malware’s capabilities.
- CVE-2020-1054 is a memory corruption vulnerability in the Windows kernel-mode driver that handles bitmap image files that enables privilege escalation [TA0004] to SYSTEM level. The attack triggers the vulnerability by creating a bitmap image and changing pixels outside of its memory bounds, enabling the attacker to write into the memory of the driver module and execute shellcode at SYSTEM level privileges.
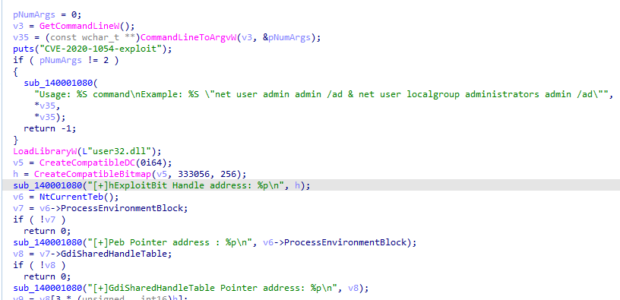
- CVE-2019-1458 Is a similar privilege escalation vulnerability in the same Win32k Windows driver. This exploit uses calls to the undocumented NtUserMessageCall API and simulated keypresses to cause memory corruption in the window switching functionality. Based on the code we analyzed, the malware copied a publicly available proof of concept to use in their script.
- CVE-2019-0808 is yet another privilege escalation vulnerability in the Win32K Windows driver. This exploit attempts to install a file with elevated privileges. While researching this exploit we also found CVE-2019-5786 used in tandem with the elevation of privilege exploit. CVE-2019-5786 is a sandbox-escape vulnerability in Google Chrome which enables the attacker to interact with the rest of the victim’s running processes. Based on this, we believe older versions of Chrome could be vulnerable when attacked with this malware if the site changes the initial exploit based on the browser used to visit the site.
Prevention
If any of these exploits succeed, the threat actor now has privileged access to the victim’s computer. With that access, they can download other malware like botnets or remote access trojan and potentially move laterally behind the network perimeter. In order to detect and prevent similar attacks, organizations should implement the following recommendations.
Implement Strong EDR
Endpoint Detection and Response software actively monitors process behavior in real time to identify suspicious and malicious behaviors and indicators of compromise. Use EDR paired with strong Endpoint Protection (EPP) that analyzes all files, watches existing process memory, and provides 100% attestation for malware or goodware.
Layer Defensive Tools That Can Identify and Block Malware Command and Control
No single layer of defense can block all malware and intrusions. In addition to EDR, layer your security with other services like DNS firewalling and IPS that can detect and block botnet command and control (C&C) connections. Tools that block C&C are a strong last line of defense in the event of an infection, limiting the ability for the malware to function or spread.
Indicators of Compromise
Domains:
- Judgementinvincible[.]com
- Speedjudgementacceleration[.]com
Files MD5s:
- B338E9E5EFA8AEDBDA533EEFF01871FF
- 694398D10C925A92DC51932D412F9514
- 7B40AA57E1C61ECD6DB2A1C18E08B0AF