Chase Bank Scams Target Our Own

The other day, a WatchGuard employee received a text alert stating that Chase bank had limited access to their account. They right away knew the message was bogus and offered it to us to investigate. We found the link within the message sends the user to a fake Chase login. Fortunately, the employee knew better and didn't follow the link in the text message, but others might not be as observant. We followed through with the phish in our test environment and found the scam could end in a takeover of the victim’s bank account.

When we first visited this site in our sandbox, at first we saw nothing, just a blank page. Upon further inspection though, we noticed the page contained some HTML code. As it turned out, the web page only displayed content when resized to a portrait window size like in a phone. We don’t know if the scam creators meant to do this to avoid analysis, but a quick resizing of the window allowed us to see the website.
The scammers made the fake website look like the real one, but a careful eye will spot a few differences including the Remember Me and Use token checkboxes as well as the copyright year on the bottom of the page.
While we navigated the website, we monitored the data that the browser transmitted to the web servers with a network monitor called Fiddler. We found that entering the username and password sent this information to the scammer where they keep it on their servers for later use. The scammers still need more information to access your account though. Chase and most other banks require multi-factor authentication, so the scam continues.
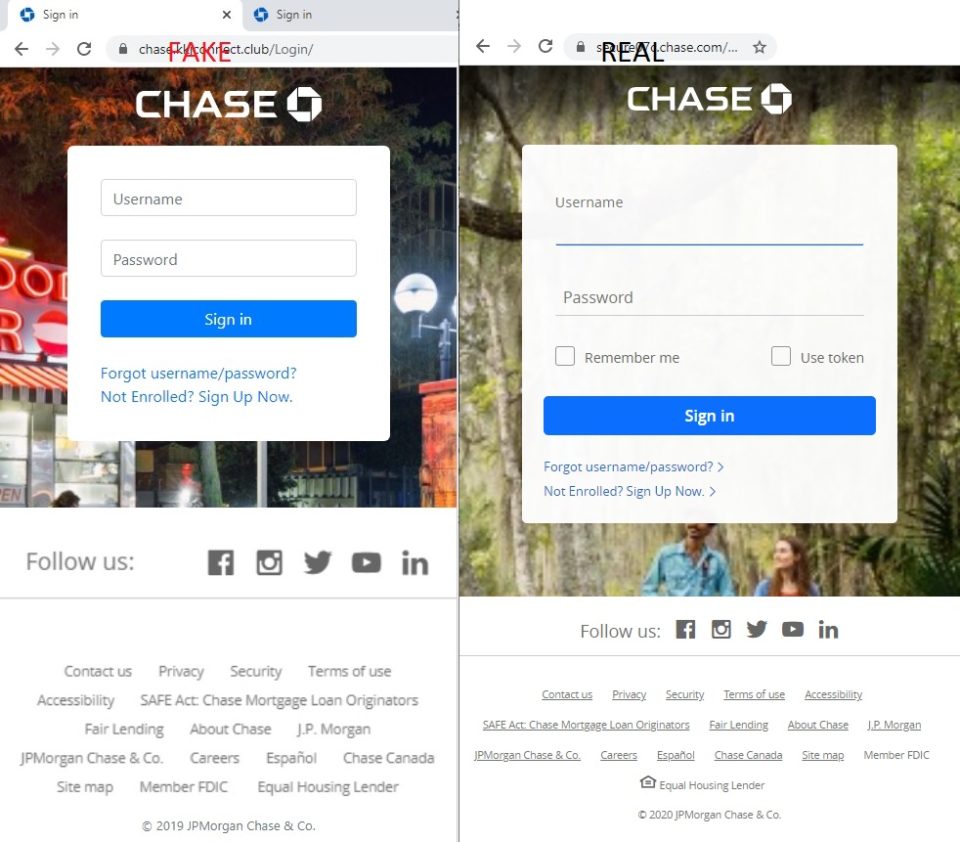
Once “logged in,” the site displayed a notification that the account has been limited and we need to update our phone number to unlock it. The scammer likely uses the phone number field to misdirect the user into thinking a normal account update is taking place. They may also use it to change the phone number on the account or send a fake notification, but we don’t know for sure. We would have to use a real bank account to test this and we understandably didn’t want to do that. We did enter a burner number that we use when investigating scams, and we saw the web page send the number to the scammers, but we never received a message or call.
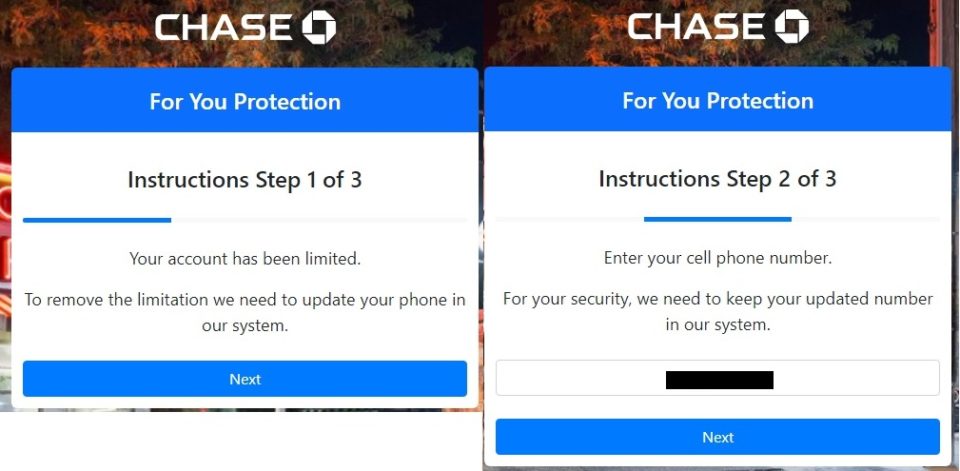
In the last step we wait for the code; we receive and enter our password again. We know this type of scam well. In the background the scammers likely have a server keeping this information and using it to log into Chase bank. The code we receive comes from the real Chase bank and if you enter this into the scammers website they will pass the code onto the website’s login page to access your account.
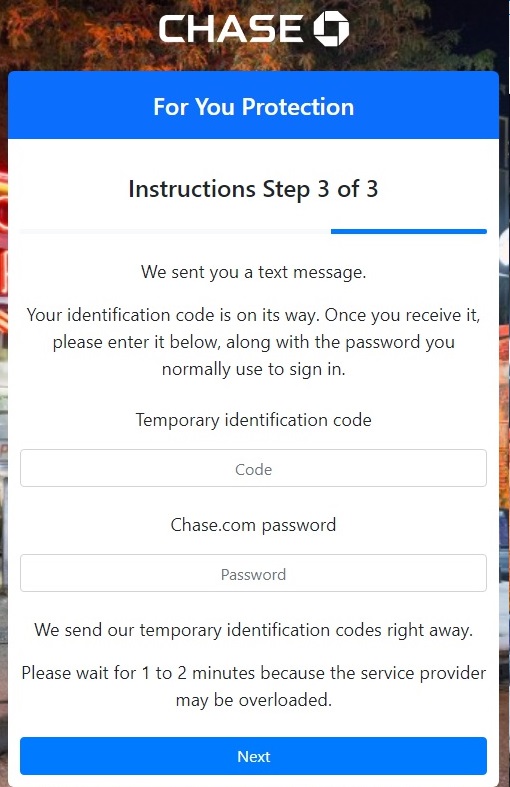
Since we didn’t use a real Chase account, we never received the code but entering a fake code allowed us through. The password this time may only misdirect the victim into thinking a normal verification is taking place just like the previous phone number field. The message “Please wait for 1 to 2 minutes because the service provider may be overloaded” gives insight into their operation. The scammer’s server likely doesn’t send the login details to the server until after you enter your phone number. It may also take time for their system to make the proper request to the Chase login page. For whatever reason, they need a little extra time to make the request on their side.
After entering a random code and password we once again saw this information sent to the scammers followed by a confirmation message on the scammer’s website. If we entered real bank login details, it wouldn’t take long for the scammers to take money out.
Always watch for text messages or phone calls that ask you for private information. Chase bank warns its users of scams just like this one on their website "Don't reply to an email, phone call or text message that tell you your account has been compromised, then asks you to give or confirm your personal or account information" Also don’t follow any links directly from an message or email. If the service has as issues with your account, you can resolve it by going directly to the website or calling them directly.