Cybersecurity News: Free Cybersecurity Training, TrickBot Group Exposed, Major GoDaddy Breach, and Russia to Legalize cybercrime?!
A new week, a new month, and a new Cybersecurity News post! This iteration contains a whopping eight (8) stories covering the last two to four weeks. Since cybersecurity is a diverse field of assorted specializations, we attempt to match that with various stories touching on all aspects of cybersecurity. This time we cover a few breaches, Elon Musk's decision to alter Twitter's multi-factor authentication policy, the TrickBot group being exposed and sanctioned, Russia wanting to legalize cybercrime formally, and more!
Since this post is relatively longer than previous iterations, we've included a table of contents so you can navigate directly to the story of your choice without scrolling. We will keep this change going forward and plan on continuously making improvements as necessary. On to the topics!
 It isn't just those seven members who we know are behind some of their ransomware development and money laundering. For example, a Latvian woman named Alla Witte helped program some of the group's software, notably the Diavol ransomware. The group also uses money mules, such as Christina Svechinskayawho, a Russian student arrested by the FBI in 2010, who act as intermediates to launder the stolen money from extortions and other misdeeds. Christina was one of 37 money mules employed by TrickBot, and you can be sure there are many more.
TrickBot's leaked chats and the unveiling of the group by the US and UK governments provide an exceptional case study on the underground ecosystem of cybercrime groups. Much of this information comes from those internal leaked chats. Cyjax gleaned this data and provided a comprehensive overview of TrickBot's operations, which is the best place to go if you want more information on this topic. A short paragraph wouldn't do it justice. You can find that reference, as well as many others, below.
References:
It isn't just those seven members who we know are behind some of their ransomware development and money laundering. For example, a Latvian woman named Alla Witte helped program some of the group's software, notably the Diavol ransomware. The group also uses money mules, such as Christina Svechinskayawho, a Russian student arrested by the FBI in 2010, who act as intermediates to launder the stolen money from extortions and other misdeeds. Christina was one of 37 money mules employed by TrickBot, and you can be sure there are many more.
TrickBot's leaked chats and the unveiling of the group by the US and UK governments provide an exceptional case study on the underground ecosystem of cybercrime groups. Much of this information comes from those internal leaked chats. Cyjax gleaned this data and provided a comprehensive overview of TrickBot's operations, which is the best place to go if you want more information on this topic. A short paragraph wouldn't do it justice. You can find that reference, as well as many others, below.
References:
 So, what happens if someone attempts to leverage quantum computing for malicious purposes? Regarding cybersecurity, the primary concern is cryptography – specifically, encryption mechanisms. Most encryption mechanisms function on the premise that breaking or brute-forcing the algorithms is too labor-intensive, either deterring or preventing decryption. With quantum computing, these encryption algorithms are subject to instantly being broken by brute force. Although it wouldn't require much "force."
Due to this, NIST has been seeking an encryption mechanism that is "quantum proof." Researchers recommended and approved an algorithm called CRYSTALS-Kyber that uses public-key encryption; the only candidate of the final four that used public-key encryption, the others used digital signatures. Quantum-proof algorithms sound great, right? Well, enter another emerging technology – artificial intelligence (AI). Both technologies are in their infancy, and it'll be interesting to see the impacts of each, either synergistically or as a check and balance on each other. In mid-February, we got a teaser.
Researchers from the KTH Royal Institute of Technology in Stockholm, Sweden, published a paper on how they broke the NIST-recommended CRYSTALS-Kyber encryption using side-channel attacks and AI. A term the researchers called "Deep learning-based side-channel attacks." A side-channel attack is an exploit based on information leakage from a system. This information usually isn't enough to break the system, but with AI, researchers can train a model to deterministically find a vulnerability in the mechanism based on the data leaked. As the researchers suggest, their work could be a model in the future to perform an AI-based audit on encryption algorithms before attackers find them first.
References:
So, what happens if someone attempts to leverage quantum computing for malicious purposes? Regarding cybersecurity, the primary concern is cryptography – specifically, encryption mechanisms. Most encryption mechanisms function on the premise that breaking or brute-forcing the algorithms is too labor-intensive, either deterring or preventing decryption. With quantum computing, these encryption algorithms are subject to instantly being broken by brute force. Although it wouldn't require much "force."
Due to this, NIST has been seeking an encryption mechanism that is "quantum proof." Researchers recommended and approved an algorithm called CRYSTALS-Kyber that uses public-key encryption; the only candidate of the final four that used public-key encryption, the others used digital signatures. Quantum-proof algorithms sound great, right? Well, enter another emerging technology – artificial intelligence (AI). Both technologies are in their infancy, and it'll be interesting to see the impacts of each, either synergistically or as a check and balance on each other. In mid-February, we got a teaser.
Researchers from the KTH Royal Institute of Technology in Stockholm, Sweden, published a paper on how they broke the NIST-recommended CRYSTALS-Kyber encryption using side-channel attacks and AI. A term the researchers called "Deep learning-based side-channel attacks." A side-channel attack is an exploit based on information leakage from a system. This information usually isn't enough to break the system, but with AI, researchers can train a model to deterministically find a vulnerability in the mechanism based on the data leaked. As the researchers suggest, their work could be a model in the future to perform an AI-based audit on encryption algorithms before attackers find them first.
References:
 It's a safe assumption to assume that these attacks will continue. So, employees at organizations who use Okta should be vigilant about the texts received. Most SMiShes can be snuffed out by taking a second and looking at the URL of the text and checking for any grammatical errors. Users of other IAM services should heed this warning as well. No one is assumed safe from SMiShing, and anyone is susceptible to being a victim of these attacks. Trust your gut. If it looks fishy, it probably is.
References:
It's a safe assumption to assume that these attacks will continue. So, employees at organizations who use Okta should be vigilant about the texts received. Most SMiShes can be snuffed out by taking a second and looking at the URL of the text and checking for any grammatical errors. Users of other IAM services should heed this warning as well. No one is assumed safe from SMiShing, and anyone is susceptible to being a victim of these attacks. Trust your gut. If it looks fishy, it probably is.
References:
 Offering SMS 2FA as an organization is indeed a significant expenditure. Musk says Twitter spends $60 million annually on fake SMS 2FA messages. That doesn't include the non-fake ones. So, Twitter may be paying up to 9-figure fees for these texts. Seeing as Musk's main priority is lowering the costs of Twitter operations, the impetus for this change is likely financially related.
However, the other reason for this change is that SMS 2FA is not as secure as other 2FA options, and as was said, this is true. Even the National Institute of Standards and Technology (NIST) advises using any other 2FA option (NIST SP 800-63B - Section 4.2.1). What's bizarre is that Musk will continue to offer this service to Twitter Blue subscribers, effectively providing a less secure option for a cost. If security were the primary concern, users wouldn't be paying extra for less security. However, the other two options – authentication apps or hardware keys – will be mandatory after the 19th of March, 2023.
Surprisingly, from July 2021 to December 2021, only 2.6% of Twitter users used 2FA. It's safe to assume this number will be lower once the policy change occurs. Meaning more users are less secure. Yes, SMS 2FA is less secure, but any 2FA is better than no 2FA. So, it completely disregards the defense-in-depth model employed by cybersecurity professionals. If you're using SMS 2FA, we recommend, as well as NIST, to change to an authentication app at a minimum and a hardware key if you desire to do so.
References:
Offering SMS 2FA as an organization is indeed a significant expenditure. Musk says Twitter spends $60 million annually on fake SMS 2FA messages. That doesn't include the non-fake ones. So, Twitter may be paying up to 9-figure fees for these texts. Seeing as Musk's main priority is lowering the costs of Twitter operations, the impetus for this change is likely financially related.
However, the other reason for this change is that SMS 2FA is not as secure as other 2FA options, and as was said, this is true. Even the National Institute of Standards and Technology (NIST) advises using any other 2FA option (NIST SP 800-63B - Section 4.2.1). What's bizarre is that Musk will continue to offer this service to Twitter Blue subscribers, effectively providing a less secure option for a cost. If security were the primary concern, users wouldn't be paying extra for less security. However, the other two options – authentication apps or hardware keys – will be mandatory after the 19th of March, 2023.
Surprisingly, from July 2021 to December 2021, only 2.6% of Twitter users used 2FA. It's safe to assume this number will be lower once the policy change occurs. Meaning more users are less secure. Yes, SMS 2FA is less secure, but any 2FA is better than no 2FA. So, it completely disregards the defense-in-depth model employed by cybersecurity professionals. If you're using SMS 2FA, we recommend, as well as NIST, to change to an authentication app at a minimum and a hardware key if you desire to do so.
References:
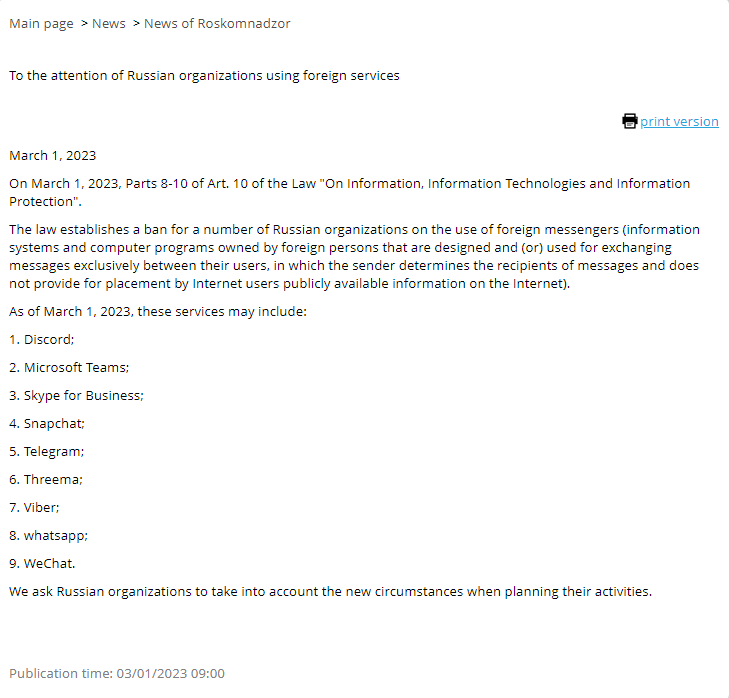 The list doesn't include some big names, including Meta (Facebook and Instagram) and Zoom. That's because last year, Russia found Meta guilty of "engaging in extremist activity" because it tolerated "Russophobia" on its platform. These decrees aren't just for show, as influencers on these social media platforms were restricted from these platforms and could face jail time.
Several references are below regarding CIS countries, Russia's link to cybercrime, Russian cyber laws, and the abovementioned decrees.
References:
The list doesn't include some big names, including Meta (Facebook and Instagram) and Zoom. That's because last year, Russia found Meta guilty of "engaging in extremist activity" because it tolerated "Russophobia" on its platform. These decrees aren't just for show, as influencers on these social media platforms were restricted from these platforms and could face jail time.
Several references are below regarding CIS countries, Russia's link to cybercrime, Russian cyber laws, and the abovementioned decrees.
References:
Table of contents
- TrickBot Group Exposed and Sanctioned
- Multi-Year GoDaddy Breach Results in Source Code Leak and Malware
- Cybrary Releases more than 500 Hours of Free Cybersecurity Training Videos to Address the Skills Shortage
- Post-Quantum Encryption Algorithm Cracked With the Help of AI
- Group Behind 0ktapus Campaign Attempted Sophisticated Attack on Coinbase
- Twitter Removes SMS Two-Factor Authentication For Non-Twitter Blue Subscribers
- Three Terabytes of U.S. Military USSOCOM Data Exposed on Azure Server
- Russia Seeks to Formally Legalize Cybercrime
1) TrickBot Group Exposed and Sanctioned
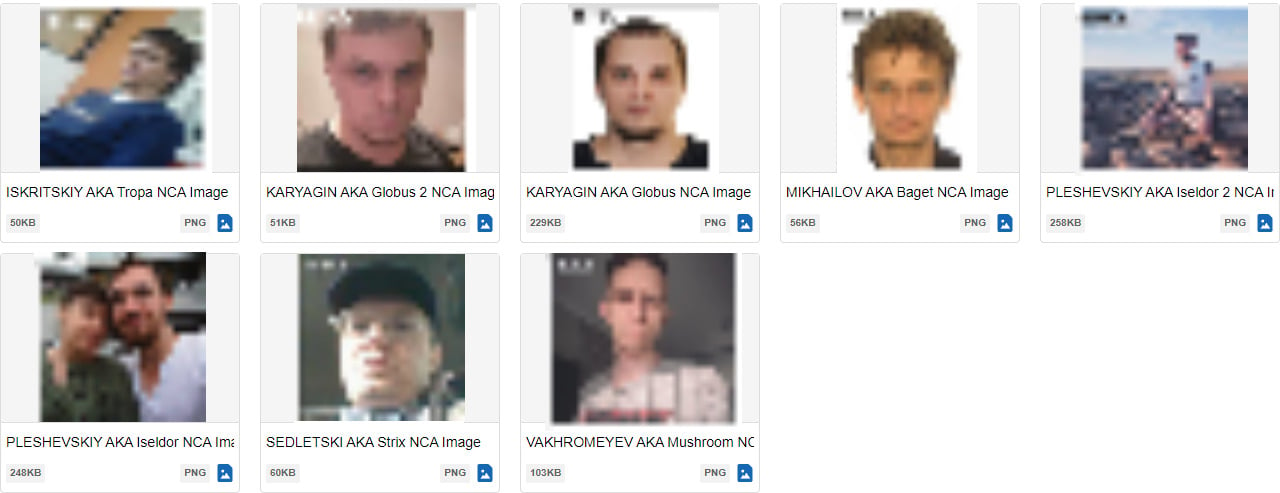
United States (US) and United Kingdom (UK) authorities have exposed and announced sanctions against seven members of the TrickBot cybercrime gang. You may also know the group under different aliases – Wizard Spider, FIN12, DEV-0193, DEV-0569, and UNC1878. Although, these aliases could be affiliates cooperating with prominent TrickBot members. The group also goes by the ransomware they have created or helped propagate – BlackByte, Black Basta, Conti, Diavol, Maze, Quantum, Royal, and Ryuk. Their bread and butter is the botnet they use to spam email campaigns – TrickBot – to deploy further malware, usually ransomware. The sanctioned members are as follows:- Vitaly Kovalev ("Bentley," "Ben")
- Maksim Mikhailov (“Baget”)
- Valentin Karyagin (“Globus”)
- Mikhail Iskritskiy ("Tropa")
- Dmitry Pleshevskiy ("Iseldor")
- Ivan Vakhromeyev ("Mushroom")
- Valery Sedletski (“Strix”)
 It isn't just those seven members who we know are behind some of their ransomware development and money laundering. For example, a Latvian woman named Alla Witte helped program some of the group's software, notably the Diavol ransomware. The group also uses money mules, such as Christina Svechinskayawho, a Russian student arrested by the FBI in 2010, who act as intermediates to launder the stolen money from extortions and other misdeeds. Christina was one of 37 money mules employed by TrickBot, and you can be sure there are many more.
TrickBot's leaked chats and the unveiling of the group by the US and UK governments provide an exceptional case study on the underground ecosystem of cybercrime groups. Much of this information comes from those internal leaked chats. Cyjax gleaned this data and provided a comprehensive overview of TrickBot's operations, which is the best place to go if you want more information on this topic. A short paragraph wouldn't do it justice. You can find that reference, as well as many others, below.
References:
It isn't just those seven members who we know are behind some of their ransomware development and money laundering. For example, a Latvian woman named Alla Witte helped program some of the group's software, notably the Diavol ransomware. The group also uses money mules, such as Christina Svechinskayawho, a Russian student arrested by the FBI in 2010, who act as intermediates to launder the stolen money from extortions and other misdeeds. Christina was one of 37 money mules employed by TrickBot, and you can be sure there are many more.
TrickBot's leaked chats and the unveiling of the group by the US and UK governments provide an exceptional case study on the underground ecosystem of cybercrime groups. Much of this information comes from those internal leaked chats. Cyjax gleaned this data and provided a comprehensive overview of TrickBot's operations, which is the best place to go if you want more information on this topic. A short paragraph wouldn't do it justice. You can find that reference, as well as many others, below.
References:
- https://analyst1.com/wp-content/uploads/2022/11/Nationstate_ransomware_with_consecutive_endnotes.pdf
- https://cisa.gov/sites/default/files/publications/TrickBot_Fact_Sheet_508.pdf
- https://cyjax.com/app/uploads/2022/07/Who-is-Trickbot.pdf
- https://fcdo.brandworkz.com/BMS/albums/?album=3376&lightboxAccessID=A6A8C4AC-D67B-4F8B-A7CDCFE41CD719C0
- https://forbes.com/sites/sap/2023/02/09/how-tech-helps-this-young-business-better-care-for-its-customers/?sh=3387bdb9796d
- https://holdsecurity.com/news/2021/06/trickbot-gang-arrest-story-of-alla-witte/
- https://krebsonsecurity.com/2010/09/u-s-charges-37-alleged-money-mules/
- https://krebsonsecurity.com/2023/02/u-s-u-k-sanction-7-men-tied-to-trickbot-hacking-group/
- https://reuters.com/article/us-cybercrime-russia-dyre-exclusive/exclusive-top-cybercrime-ring-disrupted-as-authorities-raid-moscow-offices-sources-idUSKCN0VE2QS
- https://sentinelone.com/labs/trickbot-update-brief-analysis-of-a-recent-trickbot-payload/
- https://thedfirreport.com/2021/12/13/diavol-ransomware/
- https://threatpost.com/conti-ransomware-decryptor-trickbot-source-code-leaked/178727/
2) Multi-Year GoDaddy Breach Results in Source Code Leak and Malware
GoDaddy is an American domain registrar and web hosting company based in Arizona. Apart from those two things, the company has evolved to offer a suite of tools to help anyone get a website up and running with additional offerings to market and attract customers. Unfortunately, according to GoDaddy's most recent U.S. Securities and Exchange Commission (SEC) annual 10-K report, the company was a victim of three separate breaches involving the same threat actor over the last three years. According to the report, the breach impacted over one million GoDaddy customers and began in March 2020 when 28,000 hosting accounts were compromised. The second breach occurred a year later when the hackers acquired an admin password from the company and gained access to GoDaddy's WordPress admin dashboard. This resulted in a further compromise of 1.2 million customers through the Managed WordPress hosting environment. The third and final breach happened a few months ago, in December, when threat actors installed malware on internal systems. This malware ended up on customers' websites, affecting not only GoDaddy but also customers. Thankfully, GoDaddy states that this string of breaches didn't affect normal operations, and the incident is no longer ongoing. Read the official 10-K report to understand the breadth of the breach and the services involved. References:- https://aboutus.godaddy.net/about-us/overview/default.aspx
- https://godaddy.com/catalog
- https://guard.io/blog/godaddy-admits-28-000-customers-were-affected-in-data-breach
- https://madeinbritain.org/news/godaddy-the-latest-cyber-attack-victim-with-malware-installed-and-source-code-stolen
- https://malcare.com/blog/godaddy-data-breach/
- https://sec.gov/Archives/edgar/data/1609711/000160971121000122/gddyblogpostnov222021.htm
- https://sec.gov/files/reada10k.pdf
- https://techcrunch.com/2021/11/22/godaddy-breach-million-accounts/
3) Cybrary Releases more than 500 Hours of Free Cybersecurity Training Videos to Address the Skills Shortage
This post is short and sweet. Cybrary, a well-known cybersecurity platform, announced they are making more than 500 hours of video content free to address the cybersecurity skills shortage. These videos are for all skill levels, beginner, practitioner, and advanced practitioner, in what they aptly call "Cybrary Free Access." For beginners, they offer a new IT Foundations and Cybersecurity Foundations path. Practitioners can utilize certification prep courses. Advanced practitioners can unlock entire courses for free, such as Threat Actor Campaigns (TAC) and Common Vulnerabilities and Exploits (CVE) Series. According to the World Economic Forum (WEF), the cybersecurity sector must fill around 3.4 million jobs to fill the workforce gap. A gap that increased by 26.2% in 2022 compared to 2021. According to a study by Fortinet, the two areas to address are training and diversity. Cybrary is doing its part for training, but diversity is arguably more important. That's because there are many free cybersecurity resources already, but about 80% of all cybersecurity professionals are white, and only 14% are female. In other words, it's easier to train technical skills as opposed to hiring an outstanding diverse team with varying skill sets and backgrounds. With millions of job openings, organizations want to retain talented folks and build a well-rounded team. However, that isn't easy, with other organizations eager to snatch skilled cybersecurity professionals of all genders, races, and backgrounds. References:- https://appknox.com/blog/top-free-cybersecurity-training-resources
- https://cybrary.it/blog/500-hours-free-content-to-address-cybersecurity-skills-shortage/
- https://cybrary.it/catalog/career-path/cybersecurity-foundations/
- https://cybrary.it/catalog/career-path/it-foundations/
- https://cybrary.it/catalog/certifications/
- https://cybrary.it/catalog/common-vulnerabilities-exposure-series
- https://cybrary.it/catalog/threat-actor-campaigns
- https://infosecurity-magazine.com/news/cybersecurity-workforce-gap-grows/
- https://isc2.org//-/media/ISC2/Research/2022-WorkForce-Study/ISC2-Cybersecurity-Workforce-Study.ashx
- https://forbes.com/sites/forbestechcouncil/2021/04/23/how-to-address-the-lack-of-diversity-in-cybersecurity/
- https://forbes.com/sites/forbestechcouncil/2022/09/30/minorities-and-the-cybersecurity-skills-gap/
- https://fortinet.com/content/dam/fortinet/assets/reports/report-2022-skills-gap-survey.pdf
- https://fortune.com/education/articles/the-cybersecurity-industry-is-short-3-4-million-workers-thats-good-news-for-cyber-wages/
- https://nist.gov/system/files/documents/2022/07/06/NICE%20FactSheet_Workforce%20Demand_Final_20211202.pdf
4) Post-Quantum Encryption Algorithm Cracked With the Help of AI
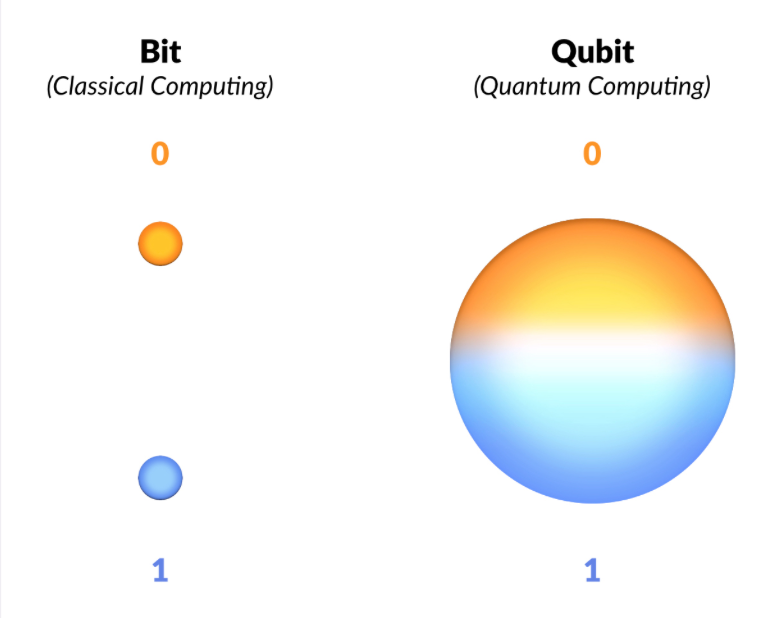
The idea and implementation of quantum computing will fundamentally change the world, plain and simple. This is because quantum computers contain quantum bits (qubits) that hold exponentially more data than traditional computer bits, vastly increasing throughput. A conventional bit can be in one of two states – 0 (off) or 1 (on). Conversely, a qubit can be in more than one state – 0, 1, "or any proportion of 0 and 1 in superposition of both states, with a certain probability of being a 0 and a certain probability of being a 1." Since throughput equals data over time, qubits can send an exponential increase in data directly proportional to the qubit's state. Thus, quantum computing can solve many, if not all, of the world's most computing-intensive tasks, superseding supercomputers. So, what happens if someone attempts to leverage quantum computing for malicious purposes? Regarding cybersecurity, the primary concern is cryptography – specifically, encryption mechanisms. Most encryption mechanisms function on the premise that breaking or brute-forcing the algorithms is too labor-intensive, either deterring or preventing decryption. With quantum computing, these encryption algorithms are subject to instantly being broken by brute force. Although it wouldn't require much "force."
Due to this, NIST has been seeking an encryption mechanism that is "quantum proof." Researchers recommended and approved an algorithm called CRYSTALS-Kyber that uses public-key encryption; the only candidate of the final four that used public-key encryption, the others used digital signatures. Quantum-proof algorithms sound great, right? Well, enter another emerging technology – artificial intelligence (AI). Both technologies are in their infancy, and it'll be interesting to see the impacts of each, either synergistically or as a check and balance on each other. In mid-February, we got a teaser.
Researchers from the KTH Royal Institute of Technology in Stockholm, Sweden, published a paper on how they broke the NIST-recommended CRYSTALS-Kyber encryption using side-channel attacks and AI. A term the researchers called "Deep learning-based side-channel attacks." A side-channel attack is an exploit based on information leakage from a system. This information usually isn't enough to break the system, but with AI, researchers can train a model to deterministically find a vulnerability in the mechanism based on the data leaked. As the researchers suggest, their work could be a model in the future to perform an AI-based audit on encryption algorithms before attackers find them first.
References:
So, what happens if someone attempts to leverage quantum computing for malicious purposes? Regarding cybersecurity, the primary concern is cryptography – specifically, encryption mechanisms. Most encryption mechanisms function on the premise that breaking or brute-forcing the algorithms is too labor-intensive, either deterring or preventing decryption. With quantum computing, these encryption algorithms are subject to instantly being broken by brute force. Although it wouldn't require much "force."
Due to this, NIST has been seeking an encryption mechanism that is "quantum proof." Researchers recommended and approved an algorithm called CRYSTALS-Kyber that uses public-key encryption; the only candidate of the final four that used public-key encryption, the others used digital signatures. Quantum-proof algorithms sound great, right? Well, enter another emerging technology – artificial intelligence (AI). Both technologies are in their infancy, and it'll be interesting to see the impacts of each, either synergistically or as a check and balance on each other. In mid-February, we got a teaser.
Researchers from the KTH Royal Institute of Technology in Stockholm, Sweden, published a paper on how they broke the NIST-recommended CRYSTALS-Kyber encryption using side-channel attacks and AI. A term the researchers called "Deep learning-based side-channel attacks." A side-channel attack is an exploit based on information leakage from a system. This information usually isn't enough to break the system, but with AI, researchers can train a model to deterministically find a vulnerability in the mechanism based on the data leaked. As the researchers suggest, their work could be a model in the future to perform an AI-based audit on encryption algorithms before attackers find them first.
References:
- https://azure.microsoft.com/en-us/resources/cloud-computing-dictionary/what-is-a-qubit/#introduction
- https://csrc.nist.gov/csrc/media/Projects/post-quantum-cryptography/documents/selected-algos-2022/official-comments/crystals-kyber-selected-algo-official-comment.pdf
- https://csrc.nist.gov/glossary/term/side_channel_attack
- https://energy.gov/science/doe-explainsquantum-computing
- https://eprint.iacr.org/2022/1713.pdf
- https://ibm.com/topics/supercomputing
- https://www.nist.gov/news-events/news/2022/07/pqc-standardization-process-announcing-four-candidates-be-standardized-plus
- https://qc-at-davis.github.io/QCC/How-Quantum-Computing-Works/The-Qubit/The-Qubit.html
- https://securityweek.com/ai-helps-crack-a-nist-recommended-post-quantum-encryption-algorithm/
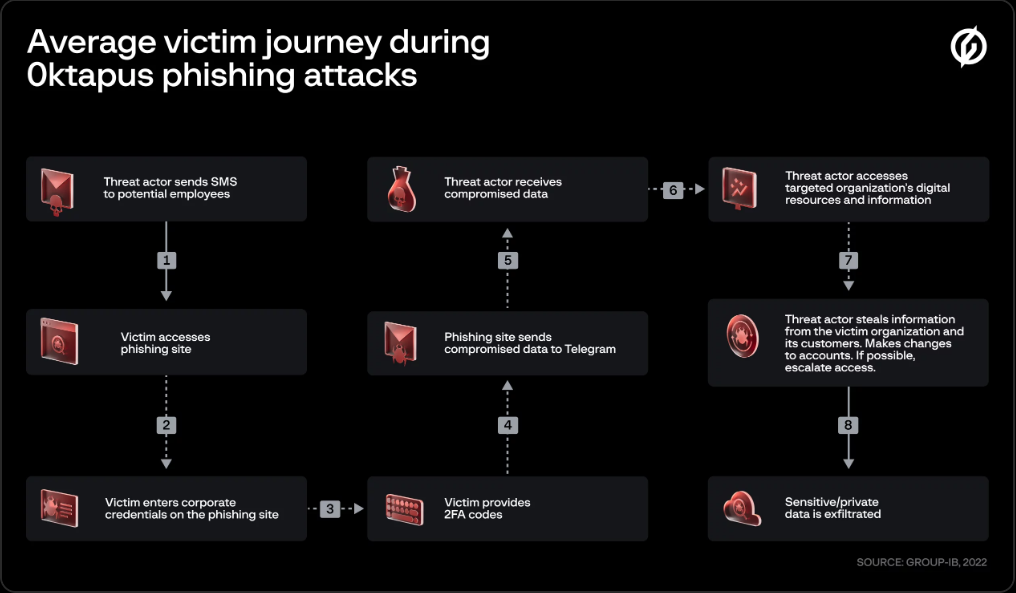
5) Group Behind 0ktapus Campaign Attempted Sophisticated Attack on Coinbase
A group named 0ktapus recently performed several high-profile SMiShing campaigns targeting organizations using Okta. Okta provides Identity Access Management (IAM) services that allow users to authenticate and access secure resources. SMiShing combines the terms' SMS' and 'phishing' and is what you think it is – phishing via text messages. In the latter half of 2022, 0ktapus operators allegedly performed SMiShing attacks on Twilio, DoorDash, CloudFlare, and over a hundred others. In February, 0ktapus attempted to breach Coinbase using the same techniques. Fortunately, they did not fall victim to their social engineering attempts for the most part. Coinbase used this opportunity to be transparent and share the information they learned from this attack to help other organizations using Okta. They released a case study on the event and revealed a lot of good tactics, techniques, and procedures (TTPs) that the attackers used. The TTPs include how they acquired initial access, potential command and control servers (C2s), tools used for remote access, and unexpected installations. A typical SMiShing attack from 0ktapus looks like this: It's a safe assumption to assume that these attacks will continue. So, employees at organizations who use Okta should be vigilant about the texts received. Most SMiShes can be snuffed out by taking a second and looking at the URL of the text and checking for any grammatical errors. Users of other IAM services should heed this warning as well. No one is assumed safe from SMiShing, and anyone is susceptible to being a victim of these attacks. Trust your gut. If it looks fishy, it probably is.
References:
It's a safe assumption to assume that these attacks will continue. So, employees at organizations who use Okta should be vigilant about the texts received. Most SMiShes can be snuffed out by taking a second and looking at the URL of the text and checking for any grammatical errors. Users of other IAM services should heed this warning as well. No one is assumed safe from SMiShing, and anyone is susceptible to being a victim of these attacks. Trust your gut. If it looks fishy, it probably is.
References:
- https://blog.cloudflare.com/2022-07-sms-phishing-attacks/
- https://cloudflare.com/learning/what-is-cloudflare/
- https://coinbase.com/blog/social-engineering-a-coinbase-case-study
- https://doordash.news/get-the-facts/how-were-responding-to-a-third-party-vendor-phishing-incident/
- https://group-ib.com/blog/0ktapus/
- https://group-ib.com/media-center/press-releases/0ktapus-campaign/
- https://support.okta.com/help/s/article/what-is-okta?language=en_US
- https://support.signal.org/hc/en-us/articles/4850133017242
- https://threatpost.com/0ktapus-victimize-130-firms/180487/
- https://twilio.com/blog/august-2022-social-engineering-attack
- https://twilio.com/resource-center/what-is-twilio-an-introduction-to-the-leading-customer-engagement-platform
6) Twitter Removes SMS Two-Factor Authentication For Non-Twitter Blue Subscribers
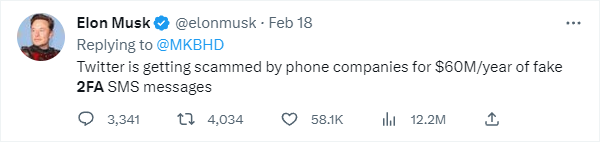
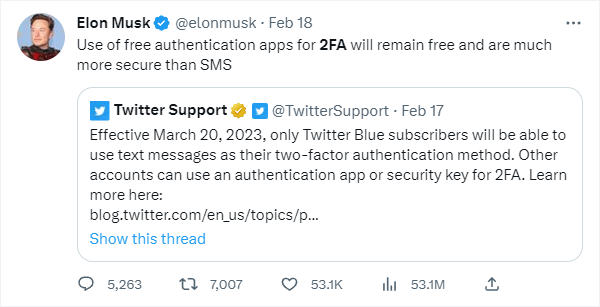
Elon Musk is back at it again, ruffling the feathers of cybersecurity practitioners and anyone not subscribed to Twitter Blue. That's because Twitter announced an update to two-factor authentication (2FA), placing SMS 2FA behind the paywall of Twitter Blue. Currently, in the United States, Twitter costs $8.00 per month for web users and $11.00 per month for iOS and Android users. The higher price for mobile users is to offset the fees going to Apple and Google, respectively, and these costs vary based on your country. Based on his public tweets, Musk states that the change is because of money expenditures by offering SMS 2FA and its insecurity based on the various manners attackers bypass SMS 2FA. Both of which are true. Musk reveals those thoughts in his Tweets below:
 Offering SMS 2FA as an organization is indeed a significant expenditure. Musk says Twitter spends $60 million annually on fake SMS 2FA messages. That doesn't include the non-fake ones. So, Twitter may be paying up to 9-figure fees for these texts. Seeing as Musk's main priority is lowering the costs of Twitter operations, the impetus for this change is likely financially related.
However, the other reason for this change is that SMS 2FA is not as secure as other 2FA options, and as was said, this is true. Even the National Institute of Standards and Technology (NIST) advises using any other 2FA option (NIST SP 800-63B - Section 4.2.1). What's bizarre is that Musk will continue to offer this service to Twitter Blue subscribers, effectively providing a less secure option for a cost. If security were the primary concern, users wouldn't be paying extra for less security. However, the other two options – authentication apps or hardware keys – will be mandatory after the 19th of March, 2023.
Surprisingly, from July 2021 to December 2021, only 2.6% of Twitter users used 2FA. It's safe to assume this number will be lower once the policy change occurs. Meaning more users are less secure. Yes, SMS 2FA is less secure, but any 2FA is better than no 2FA. So, it completely disregards the defense-in-depth model employed by cybersecurity professionals. If you're using SMS 2FA, we recommend, as well as NIST, to change to an authentication app at a minimum and a hardware key if you desire to do so.
References:
Offering SMS 2FA as an organization is indeed a significant expenditure. Musk says Twitter spends $60 million annually on fake SMS 2FA messages. That doesn't include the non-fake ones. So, Twitter may be paying up to 9-figure fees for these texts. Seeing as Musk's main priority is lowering the costs of Twitter operations, the impetus for this change is likely financially related.
However, the other reason for this change is that SMS 2FA is not as secure as other 2FA options, and as was said, this is true. Even the National Institute of Standards and Technology (NIST) advises using any other 2FA option (NIST SP 800-63B - Section 4.2.1). What's bizarre is that Musk will continue to offer this service to Twitter Blue subscribers, effectively providing a less secure option for a cost. If security were the primary concern, users wouldn't be paying extra for less security. However, the other two options – authentication apps or hardware keys – will be mandatory after the 19th of March, 2023.
Surprisingly, from July 2021 to December 2021, only 2.6% of Twitter users used 2FA. It's safe to assume this number will be lower once the policy change occurs. Meaning more users are less secure. Yes, SMS 2FA is less secure, but any 2FA is better than no 2FA. So, it completely disregards the defense-in-depth model employed by cybersecurity professionals. If you're using SMS 2FA, we recommend, as well as NIST, to change to an authentication app at a minimum and a hardware key if you desire to do so.
References:
- https://blog.twitter.com/en_us/topics/product/2023/an-update-on-two-factor-authentication-using-sms-on-twitter
- https://help.twitter.com/en/managing-your-account/two-factor-authentication
- https://help.twitter.com/en/using-twitter/twitter-blue
- https://pages.nist.gov/800-63-3/sp800-63b.html
- https://safetydetectives.com/blog/what-is-smishing-sms-phishing-facts/
- https://securityweek.com/sim-swapping-blamed-hacking-twitter-ceos-account/
- https://securityweek.com/twitter-shuts-off-text-based-2fa-for-non-subscribers/
- https://twitter.com/elonmusk/status/1626996774820024321
- https://twitter.com/elonmusk/status/1627059645293670401
7) Three Terabytes of U.S. Military USSOCOM Data Exposed on Azure Server
Another Azure server was misconfigured and exposed to the Internet. This time, the problem is that the exposed server belonged to the U.S. Military and revealed sensitive information about the U.S. Special Operations Command (USSOCOM). According to public reporting, a good-faith security researcher named Anurag Sen discovered the exposed server, and it's not the first time he's warned organizations of its exposed assets. According to data from Shodan, a well-known open-source intelligence (OSINT) tool used to search almost every Internet-connected device on the planet, the server exposed the data to anyone who could find it for two weeks. To understand the severity of exposing USSOCOM data to the public for two weeks, you must understand what USSOCOM does. USSOCOM, as the name implies, is the US military special operation forces command hub coordinating with other special operations forces (SOF) globally. Their operations include counterinsurgency and counterterrorism, hostage rescue and recovery, special reconnaissance, unconventional warfare, and more. The database in question possibly exposed some of this data. The Pentagon and Microsoft are investigating how this occurred. Still, a spokesperson from the Defense Department stated there was no evidence anyone accessed the three terabytes (TB) of exposed data, thankfully. References:- https://bloomberg.com/news/articles/2023-02-22/pentagon-and-microsoft-investigating-leak-of-military-emails
- https://shodan.io/
- https://socom.mil/about
- https://techcrunch.com/2020/06/19/oracle-bluekai-web-tracking/
- https://techcrunch.com/2023/02/21/sensitive-united-states-military-emails-spill-online/
8) Russia Seeks to Formally Legalize Cybercrime
In a move that may surprise most, but not all (myself), the head of the State Duma Committee on Information Policy, Alexander Khinshstein, stated that Russia intends to formalize cybercrime into law as long as it's in the interest of the Russian Federation. The Russian government and cybergroups based out of Russia, or swear allegiance to Russia, perform a lot of cyberattacks against countries not in the Commonwealth of Independent States (CIS). For those unfamiliar, the CIS is a Eurasian intergovernmental organization comprised of 9 independent countries, primarily from the former Union of Soviet Socialist Republics (USSR): Armenia, Azerbaijan, Belarus, Kazakhstan, Kyrgyzstan, Moldova, Russia, Tajikistan, and Uzbekistan. Although upon the dissolution of the USSR in 1991, the CIS consisted of 12 countries – those mentioned prior, Georgia, Turkmenistan, and Ukraine. The latter three countries withdrew from the CIS for different reasons. You can get a high-level overview of the reasons here. For all other countries not in the CIS, mainly NATO countries, Russian threat actors usually act with impunity. Russian officials typically look the other way, with some exceptions, and loopholes exist in the Criminal Code of the Russian Federation to bypass cybercrime laws. For that reason, about three-fourths of ransomware payouts lead back to Russian-based operators. You may wonder how these attackers avoid CIS countries when propagating malware, especially for self-propagating malware like worms. Well, malware authors implement geolocation techniques before the malware delivers its payload. Common methods include getting the victim's IP address, grabbing language information from the system, and even checking the keyboard configuration. This post initially stopped here, but after completing it, Russia made additional changes to cybercrime laws. On March 1st, Putin signed a decree amending Article 10 Dissemination of information or provision of information, to ban foreign messenger services, including Discord, Microsoft Teams, Skype, Snapchat, Telegram, Threema, Viber, WhatsApp, and WeChat. That decree is translated and shown in full below. The list doesn't include some big names, including Meta (Facebook and Instagram) and Zoom. That's because last year, Russia found Meta guilty of "engaging in extremist activity" because it tolerated "Russophobia" on its platform. These decrees aren't just for show, as influencers on these social media platforms were restricted from these platforms and could face jail time.
Several references are below regarding CIS countries, Russia's link to cybercrime, Russian cyber laws, and the abovementioned decrees.
References:
The list doesn't include some big names, including Meta (Facebook and Instagram) and Zoom. That's because last year, Russia found Meta guilty of "engaging in extremist activity" because it tolerated "Russophobia" on its platform. These decrees aren't just for show, as influencers on these social media platforms were restricted from these platforms and could face jail time.
Several references are below regarding CIS countries, Russia's link to cybercrime, Russian cyber laws, and the abovementioned decrees.
References:
- https://bbc.com/news/technology-60378009
- https://bleepingcomputer.com/news/security/russia-bans-foreign-messaging-apps-in-government-organizations/
- https://carnegieendowment.org/2018/02/02/why-russian-government-turns-blind-eye-to-cybercriminals-pub-75499
- https://cisa.gov/russia
- https://consultant.ru/document/cons_doc_LAW_61798/546dcc703c0a1e08647b40a2eeaf9461168c7cb1/
- https://crsreports.congress.gov/product/pdf/IF/IF11718
- https://csoonline.com/article/3632943/russia-is-fully-capable-of-shutting-down-cybercrime.html
- https://cybernews.com/news/russia-cybercrime-for-homeland/
- https://duo.com/decipher/us-says-russia-other-nations-are-uncooperative-on-cybercrime-investigations
- https://en.wikipedia.org/wiki/Member_states_of_the_Commonwealth_of_Independent_States
- https://theguardian.com/technology/2022/mar/14/russian-influencers-instagram-access-blocked-telegram-social-media
- https://imolin.org/doc/amlid/Russian_Federation_Criminal_Code.pdf
- https://nato.int/cps/en/natohq/topics_52044.htm
- https://nti.org/education-center/treaties-and-regimes/commonwealth-independent-states-cis/
- https://nytimes.com/2022/01/14/world/europe/revil-ransomware-russia-arrests.html
- https://rkn.gov.ru/news/rsoc/news74156.htm
- https://rkn.gov.ru/news/rsoc/news74672.htm
- https://roskomsvoboda.org/post/extremism-za-buty-blog/
- https://securelist.com/russian-speaking-cybercrime-evolution-2016-2021/104656/
- https://securityledger.com/2021/08/connecting-the-dots-the-kremlins-links-to-cyber-crime/
- https://standinggroups.ecpr.eu/sgoc/russian-speaking-cyber-crime-reasons-behind-its-success/
- https://tass.ru/obschestvo/17021313
- https://themoscowtimes.com/2022/10/11/startup-pollsters-challenge-accepted-wisdom-on-russians-war-support-a78972