Cybersecurity News: A Trio of Vulnerabilities, BreachForums Admin Arrested, Hundreds of Ransomware Victims, and The Rise of AI
This post arrives later than usual, but as they say, "Better late than never." Researchers and the media have highlighted various unique, interesting, or destructive vulnerabilities in the last few weeks. We decided to pick three of these vulnerabilities and talk about them. One was patched with Microsoft's Patch Tuesday in March; another affects the privacy of almost everyone, and the CL0P ransomware group leveraged the third vulnerability to infect well over 100 victims. We wanted to highlight another vulnerability – BingBang – that allowed Cloud Security Researcher, Hillai Ben-Sasson, to manipulate Bing search results and take over accounts. However, he posted a blog post that provides a perfect explanation. So, you won't see it here. The other three posts discuss cyberlaw, artificial intelligence, and cyber defense. Covering cyberlaw: the BreachForums admin, pompompurin, was arrested in New York last month, and the future of the forum's evolution is in the hands of second-in-command – Baphomet. In a section called "emerging technologies," we touch on OpenAI's new iteration of ChatGPT – ChatGPT-4, other artificial intelligence tools released in parallel, and what it could mean for cybersecurity. Finally, more ransomware news, but this time it's good news – CISA launched a ransomware vulnerability program to alert organizations on vulnerabilities proactively. Note: We've updated the references footer at every sub-article. Instead of just a list of references mixed in with external publications, we've split the footer Into "references" and "Other Publications" so it's easier to determine which references came from the post and which ones are there for further information-gathering purposes only.
Table of contents
Vulnerabilities
- APTs Exploit Outlook Vulnerability – CVE-2023-23397; Patch Released by Microsoft
- aCropalypse Vulnerability Affects Google Pixel Phones and Windows Snipping Tool
- CL0P Ransomware Group Claims Over 100 Victims Using GoAnywhere Vulnerability CVE-2023-0996
Cyberlaw
Emerging Technologies
Cyber Defense
Vulnerabilities 1) APTs Exploit Outlook Vulnerability – CVE-2023-23397; Patch Released by Microsoft The first vulnerability we will discuss is CVE-2023-23397. This vulnerability has a CVSSv3 Score of 9.8 (critical), and the Computer Emergency Response Team of Ukraine (CERT-UA) was the first to discover and report the vulnerability to Microsoft, per Microsoft's acknowledgments. It's likely because researchers attributed the threat actors to their neighbors – Russia – via the group APT28 (AKA: FANCY BEAR, STRONTIUM, Sofacy). The group didn't leverage their exploit on just Ukraine. There's evidence of attacks on Turkey, Jordan, Poland, and Romania as far back as April 2022. So how does it work? The elevation of privilege (EoP) vulnerability allows an attacker to craft a unique email containing a meeting or calendar invite and extract New Technology LAN Manager (NTLM) credentials without interaction from the victim. To be more procedurally granular: an attacker crafts a special Microsoft Outlook meeting or calendar invite. This invite uses a custom PidLidReminderFileParamter property containing a unique Universal Naming Convention (UNC) pointing to a Server Message Block (SMB) server. Do you know the sound you hear when you get an email from Outlook? The unique approach from an attacker allows them to send a custom notification sound in place of the original WAV file that supplies the meeting or invite notification. Instead of providing an arbitrary sound, the attacker uses this attack vector to acquire NTLM hashes. There have been numerous technical write-ups that explain it using more visual cues. I've listed them below, along with some proof-of-concept code snippets. Microsoft fixed the vulnerability in the March 2023 edition of Patch Tuesday – Microsoft's monthly operating system patches on the second Tuesday of every month. The fix happened a month ago now, so if you haven't applied that patch yet, stop what you're doing and do that first! References:
- https://deepinstinct.com/blog/cve-2023-23397-exploitations-in-the-wild-what-you-need-to-know
- https://learn.microsoft.com/en-us/office/client-developer/outlook/mapi/pidlidreminderfileparameter-canonical-property
- https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-23397
- https://twitter.com/KevTheHermit/status/1635981427400400897
Other Publications:
- https://attackerkb.com/topics/Vwh3i1yau9/cve-2023-23397
- https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-23397
- https://microsoft.com/en-us/security/blog/2023/03/24/guidance-for-investigating-attacks-using-cve-2023-23397/
- https://msrc.microsoft.com/blog/2023/03/microsoft-mitigates-outlook-elevation-of-privilege-vulnerability/
- https://nvd.nist.gov/vuln/detail/cve-2023-23397
- https://twitter.com/domchell/status/1636742613121236992
- https://virustotal.com/gui/file/582442ee950d546744f2fa078adb005853a453e9c7f48c6c770e6322a888c2cf
Technical Write-Ups:
- https://huntress.com/blog/everything-we-know-about-cve-2023-23397
- https://mdsec.co.uk/2023/03/exploiting-cve-2023-23397-microsoft-outlook-elevation-of-privilege-vulnerability/
- https://trustedsec.com/blog/critical-outlook-vulnerability-in-depth-technical-analysis-and-recommendations-cve-2023-23397/
Proof-of-Concepts:
- https://github.com/api0cradle/CVE-2023-23397-POC-Powershell
- https://github.com/tiepologian/CVE-2023-23397
- https://microsoft.github.io/CSS-Exchange/Security/CVE-2023-23397/
2) aCropalypse Vulnerability Affects Google Pixel Phones and Windows Snipping Tool Seemingly out of the blue, a security researcher disclosed a privacy vulnerability in Google Pixel's screenshot editing tool - Markup. More specifically, the vulnerability – aCropalypse – allows anyone to acquire removed cropped data from an image that used Google Pixel's Markup tool. The researcher, Simon Aarons, published an infographic to explain it better. As you can see below, the user cropped the original image using Google Pixel's Markup tool. Anyone with that image can acquire the previously cropped data, reversing the cropping action. 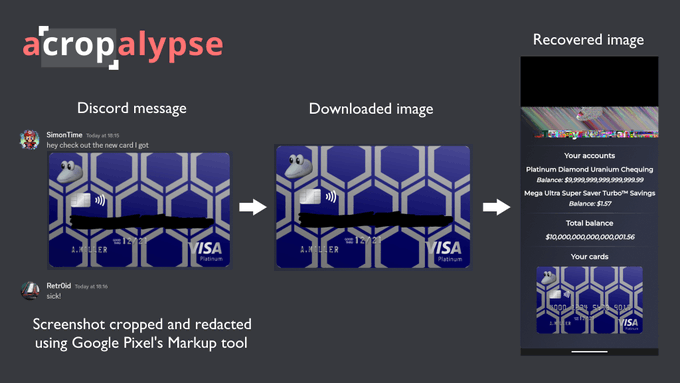
aCropalypse Infographic
To make matters worse, shortly after Simon disclosed aCropalypse, another researcher discovered that the same vulnerability lies within Windows 11 Snipping Tool (and Windows 10 Snip and Sketch). Google Pixel phones have only shipped around 30 million phones in total. While Windows currently has over 1 billion active devices. Therefore, this isn't some remote vulnerability affected by a few pictures. The vulnerability affects the following: Google Pixel:
- All Google Pixel phones beginning with the Pixel 3 (Android Pie) AND
- those that haven't updated to the 2023-03-01 patch level.
Windows:
- Windows 10 users with Snip and Sketch versions before 10.2008.3001.0 are vulnerable.
- Windows 11 users with Snipping Tool versions before 11.2302.20.0 are vulnerable.
To remedy these vulnerabilities, install the March updates from each software issuer (Google and Microsoft). However, any images with vulnerable versions are still susceptible to image recapture. The only way to eliminate the vulnerability within pictures taken with these tools is to recapture or sanitize them by truncating the excess data that is appended on the end, which allows a user to recapture the cropped data. Make sure the successive screenshots aren't using the vulnerable versions, though! References:
- https://acropalypse.app/
- https://news.microsoft.com/bythenumbers/en/windowsdevices/
- https://source.android.com/docs/security/bulletin/pixel/2023-03-01
- https://trustedreviews.com/news/googles-total-pixel-sales-barely-compare-to-what-samsung-sells-in-a-year-4272550
- https://twitter.com/ItsSimonTime/status/1636857478263750656
- https://twitter.com/ProgramMax/status/1638217206180741121
- https://twitter.com/vladsavov/status/1577242036880539648
Other Publications:
- https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-28303
- https://cve.org/CVERecord?id=CVE-2023-21036
- https://en.wikipedia.org/wiki/ACropalypse
- https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-28303
- https://windowslatest.com/2023/04/09/windows-11-kb5025310-changes-how-the-print-screen-key-works/
3) CL0P Ransomware Group Claims Over 100 Victims Using GoAnywhere Vulnerability CVE-2023-0996 The final vulnerability discussed herein is a zero-day responsible for the breach of well over 100 organizations. Well, the vulnerability isn't responsible. The CL0P ransomware group was exploiting the vulnerability – CVE-2023-0996. It all began in February when there were confirmed reports of CL0P exploiting the vulnerability and being responsible for many breaches, 130 to be exact. However, well into March, and even today, the CL0P group continues to add alleged victims at a high rate. Based on CL0P's claims and extortion page, the number of ransomed organizations is well over 200, which are from the publically reported claimed extortions only. Some posted extortions in the past month include Bissell, City of Toronto, Hitachi, Procter & Gamble, Rubrik, and Virgin.  CVE-2023-0996 is a vulnerability in GoAnywhere's Managed File Transfer (MFT) solution. GoAnywhere MFT is a product in Fortra's cybersecurity portfolio. If you don't know who Fortra is, they also have another well-known product called Cobalt Strike – a commonly used threat emulation tool used by both penetration testers and malicious hackers alike. This is notable because CL0P is known to use Cobalt Strike for its hacking efforts. So, CL0P used a Fortra product to exploit another Fortra product. The vulnerability allows attackers to gain remote code execution (RCE) from exposed administrative consoles. NIST describes the zero-day exploit: "Fortra (formerly, HelpSystems) GoAnywhere MFT suffers from a pre-authentication command injection vulnerability in the License Response Servlet due to deserializing an arbitrary attacker-controlled object. This issue was patched in version 7.1.2." Also, based on the rate of attacks, some believe the CL0P group automated the attacks. A well-written technical overview found here describes it sufficiently. References:
CVE-2023-0996 is a vulnerability in GoAnywhere's Managed File Transfer (MFT) solution. GoAnywhere MFT is a product in Fortra's cybersecurity portfolio. If you don't know who Fortra is, they also have another well-known product called Cobalt Strike – a commonly used threat emulation tool used by both penetration testers and malicious hackers alike. This is notable because CL0P is known to use Cobalt Strike for its hacking efforts. So, CL0P used a Fortra product to exploit another Fortra product. The vulnerability allows attackers to gain remote code execution (RCE) from exposed administrative consoles. NIST describes the zero-day exploit: "Fortra (formerly, HelpSystems) GoAnywhere MFT suffers from a pre-authentication command injection vulnerability in the License Response Servlet due to deserializing an arbitrary attacker-controlled object. This issue was patched in version 7.1.2." Also, based on the rate of attacks, some believe the CL0P group automated the attacks. A well-written technical overview found here describes it sufficiently. References:
- https://bleepingcomputer.com/news/security/clop-ransomware-claims-it-breached-130-orgs-using-goanywhere-zero-day/
- https://frycos.github.io/vulns4free/2023/02/06/goanywhere-forgotten.html
- https://nvd.nist.gov/vuln/detail/CVE-2023-0996
- https://ransomwareattacks.halcyon.ai/news/massive-cl0p-ransomware-campaign-likely-driven-by-automation
- https://trendmicro.com/vinfo/hk-en/security/news/ransomware-spotlight/ransomware-spotlight-clop
Other Publications:
- https://gist.github.com/Frycos/d7ec4de07123f78cc37d29890dce0313
- https://techcrunch.com/2023/03/22/fortra-goanywhere-ransomware-attack/
- https://therecord.media/what-its-like-to-run-a-hacking-forum-a-conversation-with-raidforums-owner-omnipotent
Cyberlaw 4) BreachForums Admin 'pompompurin' Arrested and Charged in New York If you've read a security article about leaked credentials or database dumps in the past year or so, you've unknowingly probably come across a picture or information derived from BreachForums. However, you may be more familiar with its predecessor, RaidForums, which operated for seven years from 2015 to 2022. In 2022, RaidForums admin, 'Omnipotent,' a Portuguese national named Diogo Santos Coelho, was arrested in the United Kingdom and charged in the Eastern District of Virginia, awaiting extradition. BreachForums is the successor to RaidForums and is essentially a clone that allows mostly black hat hackers a forum to dump and sell breached and leaked data. The transition to BreachForums wasn't immediate. After Omnipotent's arrest, many users were on high alert because of recent law enforcement actions. However, 'pompompurin,' BreachForums admin, eventually gained the community's trust, and BreachForums became the natural successor. However, BreachForum's tenure was short-lived relative to the seven-year stint of RaidForums. Pompompurin, whose real name is Conor Brian Fitzpatrick, was arrested in Peekskill, New York, on March 15, 2023. Simultaneously, federal law enforcement seized the servers of the hacking forum, effectively ending BreachForums after about one year of service. Instinctively, users of the forums are wondering what comes next, and similar to last time, many don't trust any new forums that are advertising themselves, and there's a bunch. The most obvious choice comes from the alleged second-in-command of BreachForums – Baphomet. Baphomet immediately began to trickle messages to users about possible next steps for the forum and to relay that federal law enforcement had access to the backend servers. So, Baphomet started his own Telegram group that could replace BreachForums (not likely) or wait until something else develops. Researchers have surmised possible successors, including newer websites like D4rk Forums, LeakBase, ARES Leaks, PwnedForums, and Data Forums. There are also currently other hacking forums that likely saw an increase in activity from the BreachForum's takedown, including Nulled, Cracked, Exploit, and XSS. Who knows what will come next, but the WatchGuard Threat Lab will certainly stay on top of it and report on any developments in future iterations of these articles. References:
- https://bleepingcomputer.com/news/security/fbi-confirms-access-to-breached-cybercrime-forum-database/
- https://en.wikipedia.org/wiki/BreachForums
- https://en.wikipedia.org/wiki/RaidForums
- https://flashpoint.io/wp-content/uploads/Complaint-USA-v.-Conor-Brian-Fitzpatrick.pdf
- https://justice.gov/d9/press-releases/attachments/2022/04/12/coelho_indictment.pdf
- https://justice.gov/opa/pr/justice-department-announces-arrest-founder-one-world-s-largest-hacker-forums-and-disruption
- https://krebsonsecurity.com/2022/04/raidforums-get-raided-alleged-admin-arrested/
Other Publications:
- https://bleepingcomputer.com/news/security/breached-shutdown-sparks-migration-to-ares-data-leak-forums/
- https://therecord.media/what-its-like-to-run-a-hacking-forum-a-conversation-with-raidforums-owner-omnipotent
- https://twitter.com/darktracer_int/status/1639198995095633922/photo/1
Emerging Technologies 5) ChatGPT-4 and a Myriad of Other AI Tools Released The artificial intelligence (AI) revolution is upon us! The next iteration of OpenAI's ChatGPT tool – ChatGPT-4 – was released in March and brought many improvements over ChatGPT-3. For starters, ChatGPT-4 contains more parameters than its predecessor. ChatGPT-3 had 175 billion parameters. So, ChatGPT-4 likely contains somewhere in the 200 billion range, but this is just an educated guess. There are no standard specifications OpenAI provides on the number of parameters in ChatGPT-4. As an aside, parameters are configuration variables that determine the language model. The more parameters, the more aspects engineers can train the model on. Like any newer technology, some will think of ways to use it to better humanity, and others will seek to leverage it for malicious purposes. For example, ChatGPT-4 scores in the 90th percentile of the Uniform Bar Exam. Some will seek ways to use this technology to help them with their studies, while others will see how they can use it to cheat on tests. It's all about intent. Of course, since this is a Cybersecurity News Post, we will imagine ways ChatGPT-4, and other AI tools, can be leveraged by attackers to make everyone's life more difficult. The most prevalent and ubiquitous AI attacks will likely pertain to social engineering, just as they do now in the current threat landscape. Researchers have warned of the implications of Deepfakes and the uncanny valley. That is no longer future to be scared of; it's the present. For example, a Twitter user created a deepfake in one hour that could trick someone, even though it doesn't look authentic. That's because he created it in an hour. Imagine if an attacker took the time to make a deepfake look as authentic as possible and used voice-spoofing AI to mimic a natural person's voice. Think of all of the social engineering attacks this technology can assist attackers with. Attackers can even spoof simple voice calls with audio-based AI and cause havoc. Social attacks are destructive now, but they will likely only get worse. References:
- https://beta.elevenlabs.io/
- https://cdc.gov/phlp/publications/topic/hipaa.html
- https://d-id.com/
- https://midjourney.com/home/?callbackUrl=%2Fapp%2F
- https://openai.com/blog/chatgpt
- https://openai.com/product/gpt-4
- https://spectrum.ieee.org/what-is-the-uncanny-valley
- https://theguardian.com/technology/2020/jan/13/what-are-deepfakes-and-how-can-you-spot-them
- https://twitter.com/christianortner/status/1639360983192723474
Other Publications:
- https://adobe.com/sensei/generative-ai/firefly.html
- https://bard.google.com/
- https://bleepingcomputer.com/news/microsoft/microsoft-brings-gpt-4-powered-security-copilot-to-incident-response/
- https://mlyearning.org/gpt-4-parameters/
- https://nvidia.com/en-us/ai-data-science/generative-ai/
- https://openai.com/blog/chatgpt-plugins
- https://openai.com/product/dall-e-2
- https://zapier.com/blog/chatgpt-vs-gpt/
Cyber Defense 6) CISA Launches Ransomware Vulnerability Warning Pilot (RVWP) Program The U.S. Cybersecurity and Infrastructure Security Agency (CISA) is a self-described national coordinator for critical infrastructure security and resilience and the operational lead for federal cybersecurity. It's "America's Cyber Defense Agency." As America's lead for cybersecurity efforts, one pillar of national security that constantly needs addressing is the defense against ransomware. The actions of ransomware operators affect businesses of all sizes and statures. Not to mention it's a matter of national security involving critical infrastructure. As such, CISA recently established the Ransomware Vulnerability Warning Pilot (RVWP) program, as required by the Cyber Incident Reporting for Critical Infrastructure Act of 2022 (CIRCIA), signed by President Biden in March 2022. The RVWP program aims to "determine vulnerabilities commonly associated with known ransomware exploitation and warn critical infrastructure entities with those vulnerabilities, enabling mitigation before a ransomware incident occurs." You may be wondering, "All vulnerabilities? What about internal vulnerabilities; how will they determine those?" The answer is simple – they won't. The RVWP program identifies and mitigates Internet-accessible vulnerabilities only. Right after the program's introduction, the CISA notified 93 organizations running Microsoft Exchange instances vulnerable to "ProxyNotShell." So, as the name implies, the program will warn organizations proactively before ransomware operators can breach your network—a step in the right direction. The RVWP program is a cog in the ransomware prevention machine. Another cog is federal and international law enforcement offensive operations. In the past, federal law enforcement apprehended the REvil ransomware group members and, more recently, dismantled the Hive ransomware operation. Not to mention the private industry playing its part [1,2]. In addition to the RVWP program and offensive operations by law enforcement, CISA, the FBI, and federal agencies led by Australia established the Joint Ransomware Task Force (JRTF) in September 2022. So, governments worldwide are tipping the tide in the ransomware battle long from over. References:
- https://cisa.gov/about
- https://cisa.gov/news-events/cybersecurity-advisories/aa23-040a
- https://cisa.gov/news-events/news/cisa-establishes-ransomware-vulnerability-warning-pilot-program
- https://cisa.gov/stopransomware/Ransomware-Vulnerability-Warning-Pilot
- https://congress.gov/bill/117th-congress/house-bill/2471/text
- https://darkreading.com/application-security/ransomware-attackers-bypass-microsoft-mitigation-proxynotshell-exploit
- https://nytimes.com/2022/01/14/world/europe/revil-ransomware-russia-arrests.html
- https://quadrantsec.com/blog/expert-insights-black-basta-backend-operations
- https://quadrantsec.com/resource/technical-analysis/black-basta-malware-overview
Other Publications:
- https://bbc.com/news/technology-59998925
- https://cisa.gov/stopransomware
- https://cisa.gov/topics/cyber-threats-and-advisories/information-sharing/cyber-incident-reporting-critical-infrastructure-act-2022-circia
- https://doublepulsar.com/proxynotshell-the-story-of-the-claimed-zero-day-in-microsoft-exchange-5c63d963a9e9
- https://justice.gov/opa/pr/us-department-justice-disrupts-hive-ransomware-variant