Deobfuscating a Dropper for a ZLoader Trojan Variant

On March 18th, 2021, the DNSWatch Tailored Analysis Team received an email from an internal WatchGuard employee who deemed the email as suspicious. The initial email included an attachment with the title Attachment_57904. A DNSWatch Analyst performed an initial assessment of the file in search of any malicious indicators or behaviors only to discover that the file was a heavily obfuscated Visual Basic Script (.vbs). Upon this discovery, the file was securely passed on to the Panda Attestation Team for further analysis. This report documents the analysis process of this file and how, ultimately, the file was unveiled to be a dropper for a ZLoader variant.
Preliminary Information
File Metadata
Dropper
| File Name: | Attachment_57904.vbs |
| File Size: | 1,403,043 (bytes) |
| MD5: | DE5FD5E5D41D654355B21942E938FFC3 |
| SHA1: | B3898BADB33A62F84EBDB5459BDCB8187DDA1867 |
| SHA256: | A46AA343E090D3EEC942D0E186AACFC3AE5A4E37FF4DD0A27FA9751961E1524C |
| File Type: | Visual Basic Script (.vbs) |
Malware
| File Name: | Rabin.dmg |
| File Size: | 463,360 (bytes) |
| MD5: | B1FC7DC75445A016588402757FDD6FF6 |
| SHA1: | 12AA8A932E6711BECA796F67E717523D6794DE9E |
| SHA256: | 94EB81BC58ADB976F21344D3EB273C9EB833AFBCADD121EB2AD38F1EF07A1F85 |
| File Type: | 32-bit Dynamic Link Library (.dll) |
Tools Used
- PowerShell
- Python
- CFF Explorer
- Notepad++
External Resources
- https://github.com/ryanestes/MalwareAnalysis
- https://www.virustotal.com/gui/file/94eb81bc58adb976f21344d3eb273c9eb833afbcadd121eb2ad38f1ef07a1f85/detection
- https://analyze.intezer.com/files/94eb81bc58adb976f21344d3eb273c9eb833afbcadd121eb2ad38f1ef07a1f85
Analysis
The attachment provided in the email (i.e. the malware sample).  The file consists of gibberish dictionary words declared as variables, inputted as comments, and large arrays consisted of integers and other words masked as integers. The images below show what is seen upon opening the file.
The file consists of gibberish dictionary words declared as variables, inputted as comments, and large arrays consisted of integers and other words masked as integers. The images below show what is seen upon opening the file.

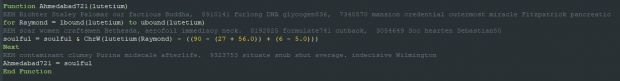
Apart from the over 500 arrays defined in this script, there are exactly 16 arrays proceeded by an execute function. Each execute function is passed an argument, Ahmedabad721(), which is a declared function within the script. The Ahmedabad721() function uses the array above as its argument. You can observe this in the image below.
In the middle of all the arrays and comments that also contain gibberish dictionary words, the Ahmedabad721 function can be found. The small function operates as such:
- Uses a for loop to iterate through the array that is passed as an argument
- subtracts 8 from the integer in the array index
- converts the resulting integer into a character using chrW()
- concatenates that character to a variable
- returns the entire concatenated string
The image below shows how this process unfolds:  After extracting the 16 arrays from the script that are proceeded by an execute function, a Python script was hacked together to replicate the Ahmedabad721 function. Listed below, in order, are the functions that are executed with an emphasis on "WuDT" (More on that next). The small script in the image below prints out all of the functions in the script. The script can be found in the Malware Analysis GitHub repo linked above in the External Resources.
After extracting the 16 arrays from the script that are proceeded by an execute function, a Python script was hacked together to replicate the Ahmedabad721 function. Listed below, in order, are the functions that are executed with an emphasis on "WuDT" (More on that next). The small script in the image below prints out all of the functions in the script. The script can be found in the Malware Analysis GitHub repo linked above in the External Resources.
The next 4 pictures show how the WuDT array evolves into visual basic code as it is deobfuscated. It was discovered that this function builds another file by using another giant array of dictionary words. Each dictionary word within this array aligns with every other array in the original VBS that was not executed (the other 500 or so). The next few steps outline how the WuDT array evolves into an entire ZIP folder containing the ZLoader trojan variant:
- A snippet of the original WuDT array as it is observed in the original script. Notice how there are dictionary words within the list of integers. The only one seen here is “hogging” which is equal to 18 as defined by a variable embedded within the script.
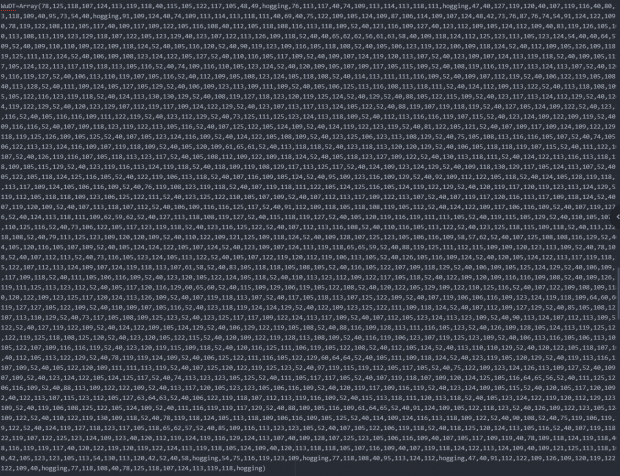
- The array with the string variables substituted with their respective integers in a Python script.

- The WuDT array after it is executed using the Ahmedabad721 function. Notice how there is further obfuscation by using comments of gibberish dictionary words. Also notice how the array is a large list of different dictionary words, each corresponding to an entirely different array found within the original script.

- After cleaning up the final obfuscation in the resulting function.
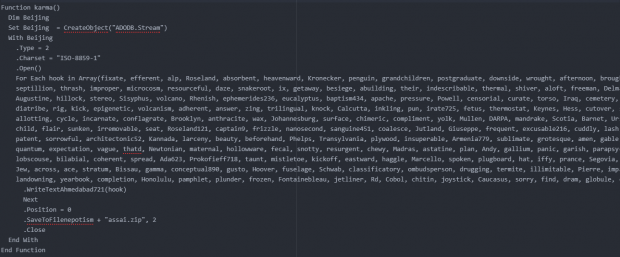
Knowing that the WuDT function is the only one that produces another file, one can assume this is the ultimate malicious file being dropped. Since this function only creates a file, the other execute functions (not WuDT) can be commented out and the original VBS can be executed to produce the resulting file WuDT produces. Ultimately, an entire zip folder named “assai.zip” was generated.

Unzipping the assai.zip folder results in a myriad of different files. All of them are 1 KB except the file named “Rabin.dmg”. Observing the 1 KB shows that each one contains exactly one line of an arbitrary string that is meaningless. In other words, further obfuscation.
Speaking of further obfuscation, the Rabin.dmg, an alleged macOS installer, is actually a 32-bit DLL originally named “us.dll”. 
- The Rabin.dmg file is, in fact, a variant of ZLoader (Ursnif/Gozi). The VBS roughly uses this procedure:

How Can I Prevent This?
The first countermeasure to prevent this malware from infecting your network is to add the signatures for the dropper and malware variant into endpoint detection systems such as antivirus software, if applicable. Considering this file arrived via email as a phishing attempt, the appropriate countermeasures fall in line with other known phishing countermeasures such as:
- Enable or implement e-mail filtering for malicious message bodies and attachments, with an emphasis on attachments.
- Ensure there is continuous anti-phishing training for all employees
- For those without the resources for anti-phishing training, scrutinize all attachments, hyperlinks, and clickable images in all e-mails. Never click anything you deem suspicious.
- Divert any suspicious e-mails to the security personnel within your organization, if possible.
- Additionally, alert security personnel if you accidentally clicked or downloaded something that seemed suspicious. Even if you did so by accident, or if you just clicked "for a second"
- Patch all of your systems and endpoints to ensure the highest security posture possible!




