The Evolution of Phishing: A WatchGuard Real-World Example
Phishing is a type of social engineering attack where threat actors attempt to trick users into providing sensitive information via email. Typically, this involves creating a phishing campaign where threat actors will send the same phishing email to a large batch of recipients in an attempt to trick at least a small subset of these potential victims. Not to be confused with spear phishing which is a more targeted phishing attack via email that uses specific knowledge or details about the recipient(s) to further deceive them into providing sensitive information. Phishing is an ongoing problem that businesses are aware of and are in a constant battle to eradicate, and for good reason. Year after year statistics reflects that IT decision-makers highlight social engineering attacks as one of the primary cyber threats they face resulting in business disruption and financial loss.
The general consensus of phishing attacks is that these attacks are ever-increasing in volume, steady in their success rates, increasing costs for businesses, are commonly used to deliver malware such as ransomware, and are evolving. For example, The Anti-Phishing Working Group releases a quarterly report showcasing current trends on phishing and their most recent report shows that phishing attacks doubled in the last year due to the COVID-19 pandemic and phishing rates have remained at a steady but high level. The FBI’s Internet Crime Complaint Center (IC3) logged similar results showing a doubling of phishing complaints in the past year. As phishing attacks increase, so do the number of breaches, and these breaches cost businesses large sums of money. IBM’s annual “Cost of a Data Breach Report”, with research by the Ponemon Institute, revealed that the estimated total cost of a data breach in 2020 is around $3.86 million and has further increased to $4.24 million in 2021, the highest average cost in 17 years. Loss of sensitive information isn’t the only threat of phishing attacks. Verizon’s Data Breach Investigations Report (DBIR) shows that almost all malware (96%) is delivered via email communications, including ransomware.
However, this post was created to highlight the evolution and complexity of phishing attacks using real-world examples experienced by WatchGuard employees. The evolution of phishing has expanded beyond email into other communication mediums such as SMS/text messaging services (SMiShing), voice calls (Vishing), and social media (Angler Phishing). Just recently, Watchguard employees experienced two of these – SMiShing and angler phishing. As you may have guessed, SMiShing is phishing, or social engineering, by us of SMS and text messaging services such as WhatsApp, Signal, and Facebook Messenger. Angler phishing is when threat actors use social media communications to masquerade as a legitimate customer service representative to elicit information. This can come in the form of SMS social media services as well as Instagram, Twitter, or LinkedIn direct messages, amongst others.
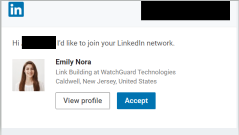
The first incident experienced by a WatchGuard employee involves LinkedIn. A user named Emily Nora was masquerading as a WatchGuard employee in a “Link Building” role, which doesn’t exist. This fake employee attempted to connect and contact several WatchGuard employees, likely just going down the list of employees associated with the official WatchGuard LinkedIn, phishing for sensitive information. Thankfully, WatchGuard employees snuffed this angler phishing attempt out immediately. A screenshot of this fake employee attempting to connect to an official WatchGuard employee can be seen below.
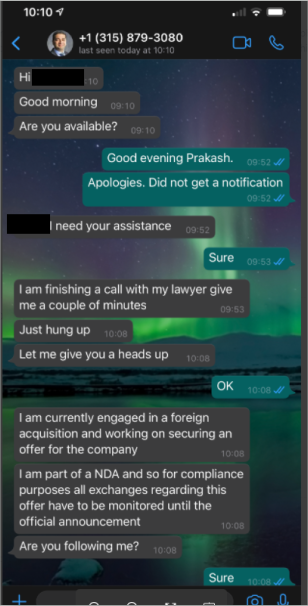
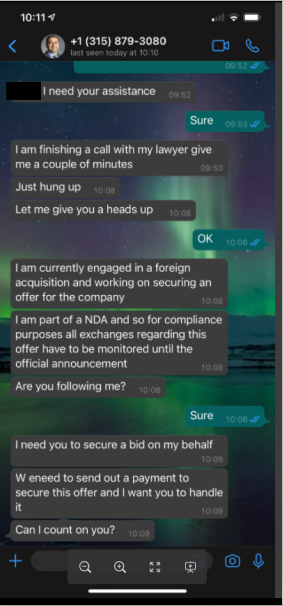
Another interesting phishing attempt came via WhatsApp. A user impersonating the CEO of WatchGuard, Prakash Panjwani, attempted to perform a foreign transaction (an acquisition) by leveraging an employee within WatchGuard to handle the payment. They used Prakash’s official image and used social engineering tactics to attempt to trick the employee into performing the action (send payment). Again, this SMiShing/angler phishing attempt was detected and reported to the appropriate channels within the organization.
Protecting from phishing attacks of all types should always begin with proper training on the issues. Studies show that simulation and gamification of phishing attacks assist users in detecting and preventing phishing attacks. However, this short post highlights the importance of training not only for phishing via email, but phishing via all possible communication mediums your organization uses; primarily phishing, vishing, SMiShing, and angler phishing training. Beyond training, common sense and your “gut” go a long way in the detection and prevention of phishing. For example, if your organization has an employee directory you can search for an employee such as Emily Nora or know that a current role doesn’t actually exist. Another example is knowing that the CEO of your organization wouldn’t likely contact you via WhatsApp to perform a significant business decision such as an acquisition. Although, these scenarios are case-by-case for each organization. The safest possible route is to just report any suspicious communications to a security professional within your organization, if possible.
References:
APWG Phishing Activity Trends Report 2Q 2021 (https://apwg.org/trendsreports/)
FBI IC3 2020 Report (https://www.ic3.gov/Media/PDF/AnnualReport/2020_IC3Report.pdf)
IBM Cost of a Data Breach 2021 (https://www.ibm.com/security/data-breach)
Verizon DBIR (https://www.verizon.com/business/resources/reports/dbir/)