Law Enforcement Infiltrate and Seize Hive Ransomware Operation
In a sudden, stunning announcement today, the United States Department of Justice, the FBI, and federal agencies from 13 countries from Europol, announced the seizure of the transnational Hive ransomware operation. The seizure was part of a months-long operation that began in late July 2022 when the FBI infiltrated the Hive network. Deputy Attorney General Lisa Monaco said it best: "…we hacked the hackers." Ultimately, this led to the seizure of all TOR websites, communications, and documentation held by the ransomware group. The pictures below show the current state of the Hive ransomware extortion website on TOR, as of this writing. 

As part of this operation, the FBI intercepted decryption keys used to decrypt encrypted files on the victim's systems. Thus, ensuring that victims can return their systems to normal without paying a ransom. The official court order from the Central District of California states that the FBI was able to provide decryption keys to 336 victims, sometimes within hours of encryption, saving around $130 million in ransom payments. The court order also states that the Hive ransomware group targeted more than 1,500 victims worldwide. Many are from the education, health care, legal, and financial sectors. Hive Ransomware was first discovered in June of 2021, shortly after the infamous Russian-based ransomware group, Conti, shut down its operations. It's widely believed that Hive is affiliated with the Conti ransomware group and could even contain some of its former members. Hive would join a list of other ransomware groups associated with former Conti operators, including Royal, Black Basta, and Quantum. Leaked chats from internal chat logs by a Twitter user named @ContiLeaks reveal that Conti was also associated with other ransomware groups, Ryuk, Diavol, and Karakurt. In other words, they're all connected! Small world, right?
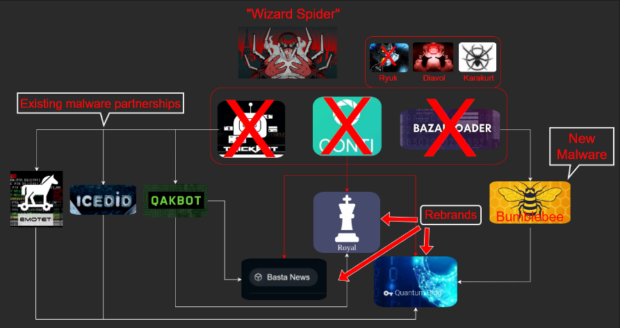
Picture attributed to @BushidoToken (https://blog.bushidotoken.net/2022/11/the-continuity-of-conti.html)
The Hive Ransomware Group runs a double extortion scheme. Meaning they exfiltrate data before deploying ransomware and then threaten to publish the victim's data on an extortion page if they don't pay the ransom. The WatchGuard Threat Lab has tracked 220 victims on Hive's extortion page. Based on the FBI's numbers of around 1,500 victims worldwide, about 15% of victims didn't pay (220/1500 = ~15%). Of course, there are probably more victims that went unreported. So, take that percentage with a grain of salt. The Hive Ransomware Group also used a Ransom-as-a-Service (RaaS) model. This model allows affiliates or other nefarious threat actors to deploy ransomware and gain most of the proceeds without having to go through the hassle of creating the malware and managing the infrastructure themselves. In this case, the Hive ransomware group used an 80/20 model – 80% of proceeds went to the affiliate, and 20% to the Hive operators. Affiliates even had their own administrative dashboard separate from the extortion page, admin panel, and victim panel to track their progress. This is observed in the pictures below, derived from the court order discussed prior.

Hive Backend Infrastructure (https://www.justice.gov/opa/press-release/file/1564286/download)
Hive Admin Panel (https://www.justice.gov/opa/press-release/file/1564286/download)

Hive Affiliate Panel (https://www.justice.gov/opa/press-release/file/1564286/download)
Another surprising anecdote the Department of Justice provided is the location of the servers used by the group. They used two servers in Los Angeles, California, and two backup servers in The Netherlands for redundancy. The court order concealed the IP addresses and owners, but they are probably cloud servers. Further information can be found in the references below. So, what now? The press conference and legal documents didn't mention much of the threat actors. Hive is associated with other groups with a history of rebranding and retooling. Unless law enforcement announces further actions against the operators of Hive, then the expectation is that these threat actors will lay low while rebranding and retooling. Only time will tell. References: https://www.justice.gov/opa/pr/us-department-justice-disrupts-hive-ransomware-variant https://www.justice.gov/opa/press-release/file/1564286/download https://www.europol.europa.eu/media-press/newsroom/news/cybercriminals-stung-hive-infrastructure-shut-down https://www.documentcloud.org/documents/21049431-fbi-flash-hive-ransomware-iocs https://www.bleepingcomputer.com/news/security/fbi-hive-ransomware-extorted-100m-from-over-1-300-victims/ https://www.bleepingcomputer.com/news/security/ransomware-profits-drop-40-percent-in-2022-as-victims-refuse-to-pay/ https://www.bleepingcomputer.com/news/security/hive-ransomware-ports-its-linux-vmware-esxi-encryptor-to-rust/ https://www.trendmicro.com/vinfo/us/security/news/ransomware-spotlight/ransomware-spotlight-hive https://blog.talosintelligence.com/conti-leak-translation/ https://krebsonsecurity.com/2022/05/costa-rica-may-be-pawn-in-conti-ransomware-groups-bid-to-rebrand-evade-sanctions/ https://www.darkreading.com/attacks-breaches/breakup-conti-ransomware-members-dangerous https://northwave-security.com/en/conti-ryuk-and-hive-affiliates-the-hidden-link/ https://securityaffairs.co/128232/security/recover-files-hive-ransomware.html https://blog.bushidotoken.net/2022/11/the-continuity-of-conti.html