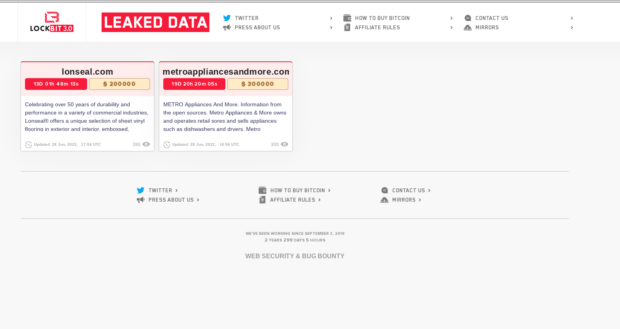
LockBit Ransomware Group Introduces Bug Bounties and More
The LockBit ransomware group has unveiled a new website – LockBit 3.0 – to host their ransom extortions and data leaks. The website includes several new features, including an unprecedented bug bounty program to assist the group in securing their site; acceptance of the privacy cryptocurrency, Zcash; and the addition of receiving payments from users to: “extend the timer for 24 hours”, “destroy all information”, and “download data at any moment”. The website wasn’t the only change from the LockBit group. Based on the new ransom note the malware drops, researchers speculate that the inner workings of the ransomware have changed as well, though that is yet to be confirmed. This post covers LockBit’s third-generation website and how their new business model could reshape other Ransomware-as-a-Service (RaaS) groups going forward.
Bug Bounties
The LockBit 3.0 home page is very similar to LockBit 2.0, their previous website which is still up and running as of this writing. One notable addition is a link at the very bottom for “WEB SECURITY & BUG BOUNTY” which redirects to the group's new Bug Bounty Program. This program is geared toward “all security researchers, ethical and unethical hackers on the planet” for amounts “from $1000 to $1 million”. Yet, isn’t an ethical hacker that helps an unethical, cybercriminal group itself unethical? This raises ethical questions, not to mention the possible legal troubles.
Ethical hackers are individuals that evaluate the security of a computing device or network with the intent of fixing or reporting the discovered vulnerabilities. Usually, ethical hackers are bound by a contract via a penetration test, or at least follow the industry’s general responsible disclosure guidelines. On the other hand, an unethical hacker penetrates a computer or network with nefarious intent. It is commonly said that ethical hackers “hack for good” and unethical hackers “hack for bad”. Hardening the defenses of a cybercriminal group and helping protect their identities is unethical and providing ideas to this group could be seen as assisting with a crime.
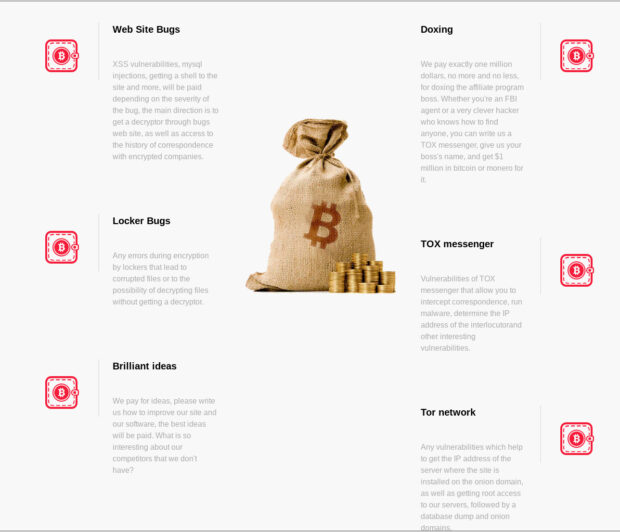
The LockBit group defines six different types of bounties on their site. Since the writing from the picture below is difficult to read, I have copy and pasted it, and paraphrased in some places for readability:
- Web Site Bugs: The group claims they will pay researchers for Cross-site Scripting (XSS) vulnerabilities, SQL injections (SQLi), installing a web shell, and more, depending on the severity of the bug. “The main direction is to get a decryptor through bugs web site, as well as access to the history of correspondence with encrypted companies”.
- Doxing: The Lockbit group claims they will “pay exactly one million dollars, no more and no less, for doxing the affiliate program boss”. Whether you're an FBI agent or a very clever hacker who knows how to find anyone, you can write to the LockBit group via TOX messenger, give your boss's name, and get $1 million in bitcoin or monero for it.
- Note: “affiliate program boss” is assumed to mean the admin(s) using the LockBit RaaS.
- Locker Bugs: Any errors during encryption by lockers that lead to corrupted files or to the possibility of decrypting files without getting a decryptor.
- TOX Messenger: Vulnerabilities of TOX messenger that allow you to intercept correspondence, run malware, determine the IP address of the interlocutor, and other interesting vulnerabilities.
- Note: Tox Messenger is a peer-to-peer instant messaging and video calling service that offers end-to-end encryption.
- Brilliant Ideas: The group will pay for ideas on how to improve the website and software, with the best ideas being paid for. “What is so interesting about our competitors that we don't have?”
- Tor Network: Any vulnerabilities which help to get the IP address of the server where the site is installed on the onion domain, despite TOR’s protections, as well as getting root access to servers, followed by a database dump and onion domains.

Bug bounties are beneficial to security researchers and organizations alike. Security researchers are often paid for their bounties based on the severity of the vulnerability and the parameters set forth by the bug bounty program, and organizations can then fix their vulnerabilities. It’s a win-win. However, if the organization is a cybercriminal group, nobody wins but the criminals. Therefore, it is strongly advised to not partake in this bug bounty due to the unethical nature and legality of the situation.
Zcash Acceptance
Zcash is a digital currency, or cryptocurrency, that is used to protect the privacy of its users by using cryptography and other technologies to shield the transaction source. In other words, it’s more difficult to trace than traditional Bitcoin and other assets. These cryptocurrency assets are known as “privacy coins”. In addition to Zcash, LockBit still accepts the de facto standard of privacy coins – Monero – and Bitcoin. It is uncertain why the LockBit group began accepting Zcash in addition to Monero, but the assumption is that it is easier to acquire. You can purchase Zcash at major United States-based cryptocurrency exchanges such as Coinbase and Binance.us, while you cannot with Monero. If victims use Zcash enough for ransoms, however, then it is likely only a matter of time before authorities or cryptocurrency exchanges remove Zcash as well. This is all speculative, however.
User Payments
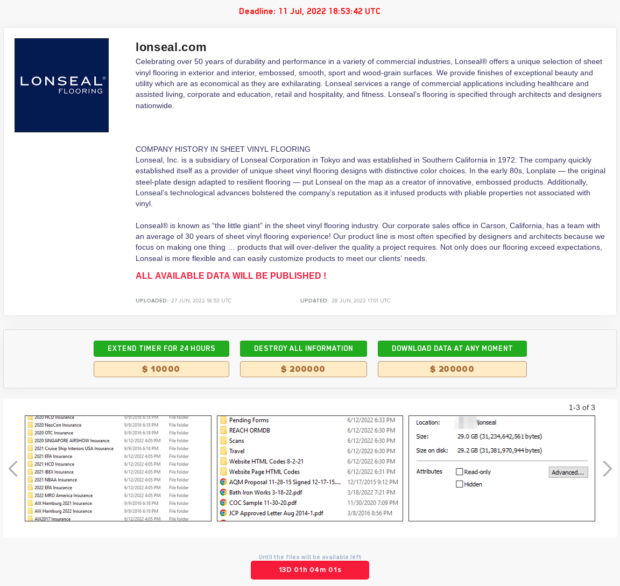
User payments refer to the aspect that ordinary users and visitors of the website can now pay money to extend extortion timers, destroy extortion data, and download extortion data on-the-fly. This can be seen on the landing page of one of the current extortion victims via the green buttons in the image below. Based on the only two victims, the prices of these features vary, but it is unknown what criteria is used to determine the dollar amount of each feature. This novel idea of including users to increase financial gain will likely motivate other ransomware groups to do the same. After all, the motivation of most of these ransomware groups is financial gain, and “brilliant ideas” such as these will only exacerbate the issue.
User payments can be seen as triple extortion, a step up from the double extortion techniques made famous by the Maze ransomware in 2019. Traditionally, ransomware would infect a computer system, encrypt files, and then demand a ransom for access to the encrypted data. This is extortion. Double extortion is when a ransomware group threatens to release the encrypted data publicly if the ransom is not paid. Triple extortion could be defined in these circumstances since users can impact how the extortion plays out. For example, a user can “extend the timer for 24 hours” with a small payment, and then the data can still be released because the original ransom is not met. Another example is if an unknown user downloads the data and then the LockBit group still publishes the data because the original ransom was not met. However, it is unknown if the group would remove the extortion if the data were downloaded or destroyed by a user as opposed to the organization that was extorted.
In summary, the LockBit group and their new LockBit 3.0 website have revolutionized how ransomware groups operate. It is often said that cybercriminal groups operate as a business, and this not only reinforces that idea, but ups the ante. The group introduced a bug bounty program to help protect the security of the group and at the same time assist with exploitation efforts. LockBit also has introduced a new payment method, Zcash, in addition to Bitcoin and Monero. Finally, users can now interact and alter the extortions of victims by extending their time, destroying information, and even downloading the data before anyone else can. These are all “features” that a typical organization would introduce. However, the difference is malice.
For security researchers who want to explore the LockBit 3.0 website, the Onion domain is listed below.
hxxp://lockbitapt2yfbt7lchxejug47kmqvqqxvvjpqkmevv4l3azl3gy6pyd[.]onion
NOTE: This website is run by cybercriminals, and you should navigate to the link at your own risk. Inexperienced users should refrain from navigating to the website.