New Phishing Attacks Stealing MFA Tokens Too
In the Firebox Feed, our threat intelligence feed powered by WatchGuard Firebox customers around the world, we recently came across a trending phishing campaign that uses a malicious PDF as part of its attack. Targeting mostly German users, the PDF comes attached to an email with a subject line that translates from German to "Invoice for your sales tax." Included in the email were instructions to add a certificate to the user’s trusted certificate store. While we didn't have to add any certificates for the malware to successfully infect our sandbox, as a rule one should never add a certificate to their computer unless they can verify its validity.
We opened the PDF with Chrome and this was our experience:
The email gave us an error message in German that told us we must open the PDF with Acrobat Reader. This should be a red flag for anyone because Acrobat Reader can do more potentially malicious actions with a PDF than Chrome on its own, like execute JavaScript. To see what damage the file could do, we ignored the red flags and opened the file with Acrobat Reader. The PDF opened an input from using Javascript that prompted us for our Amazon username and password, which we filled in with bogus information.

The PDF then displayed a security warning from Adobe. In the warning, after looking carefully, we could see the username and password in the URL, another red flag. As you can see in the warning below, the domain sellercentral[dot]amazon[dot]de[dot]A5793ERYGH40WW09[dot]oms3[dot]biz isn’t actually an Amazon domain but instead is a subdomain of oms3[dot]biz. Using subdomains to masquerade as a legitimate company is a common tactic in phishing attacks.

We clicked through the warning to continue our investigation. By clicking “Allow,” the PDF sent the email and password we entered to the attacker’s web server in a web request. The web request took us to what looked like an Amazon page, but hosted on OMS3[dot]biz. We have seen this type of attack before, but this specific one gets interesting. The page displayed a second form, asking us for our 2FA code from our phone. After we input our 2FA code we were sent to sellercentral.amazon.de the correct Amazon domain. In the meantime, the attacker in control of the phishing site would now have access to our Amazon account (if we used our real login credentials). Not only did we just give our username and password to them, but we suspect the server behind this phishing site has sent the username and password to Amazon to start the login process automatically.
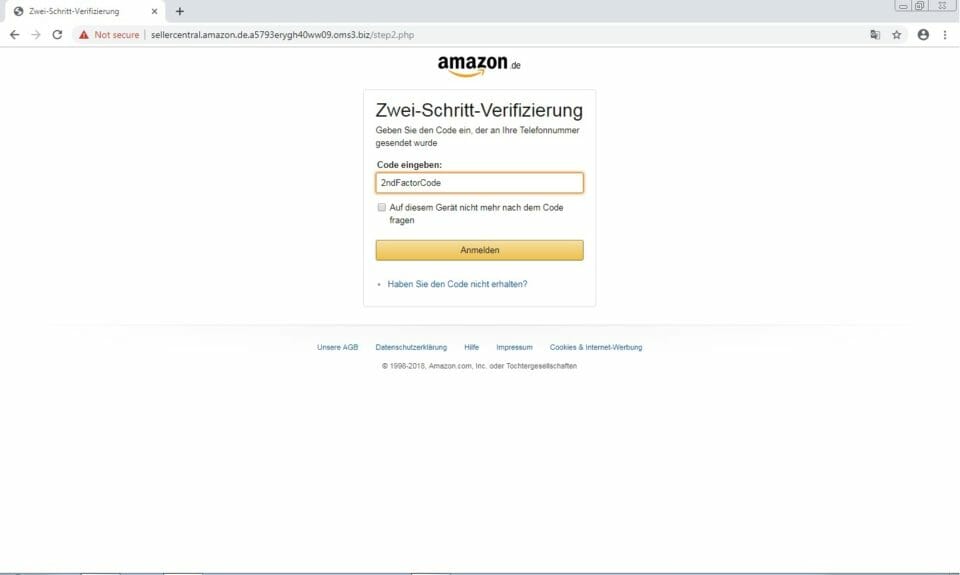
This whole prosses runs in JavaScript while using the phishing sites mentioned. We performed a packet capture during this test and we can clearly see the username, password, and 2FA in clear text being sent to the phishing site.
This code gets sent as a HTML form after submitting the last form.
submitted=true&tel=2ndFactorCode&mfaSubmit=Submit
This malware showed an evolution in typical phishing attacks, using advance techniques to gather 2FA tokens in order to access the victim’s Amazon account. We suspect the attacker automated the backend to siphon money from the victim’s account for themselves. With 2FA becoming more widely adopted for logins, phishing attempts are getting more sophisticated when attempting to access your data. 2FA makes logins much more secure but no amount of security makes users completely safe. But if users know what to look for and don't bypass warnings then we can get closer to being completely secured.