PayPal Phishing

The other day, a PayPal phish made it into the inbox of my personal email. It is not normal for phishing emails to make their way past my cloud email provider’s spam filter, so I decided to spin up a sandbox just in case any malware was involved and dive in.
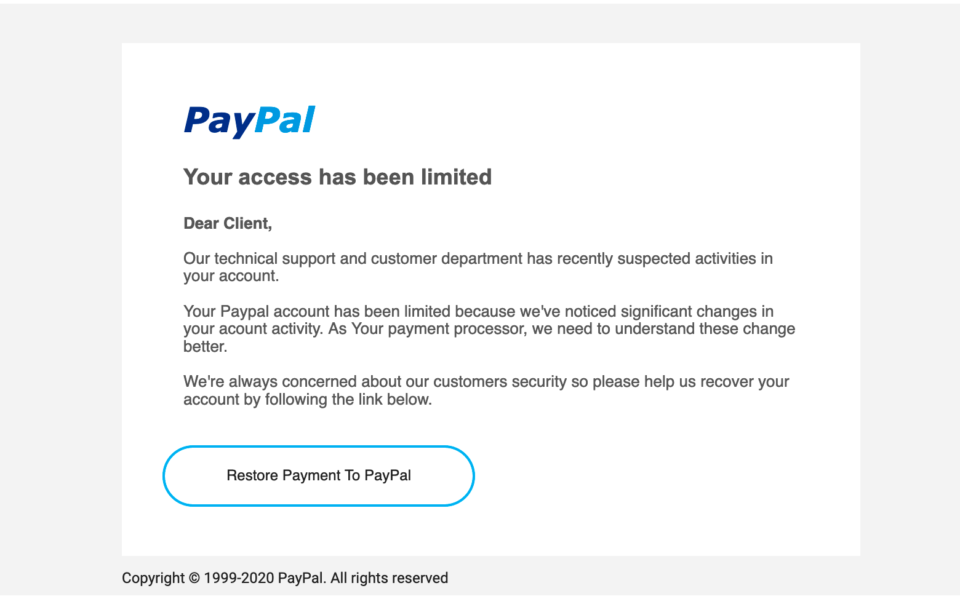
The phishing hook in the message body wasn’t anything special. The phish masqueraded as an email from PayPal notifying me that my account access has been limited for suspicious activity. A few things about the wording of this message were obvious giveaways that the source of this message was not legitimate. First, PayPal has always included my full name in their messages sent to me. The generic “Dear client” was a change from the norm and signaled a red flag. Next up, the first sentence flat out didn’t make sense. “Our technical support and customer department has recently suspected activities in your account.” A more accurate opening line might be “…has recently identified suspicious activity on your account” or something along those lines.
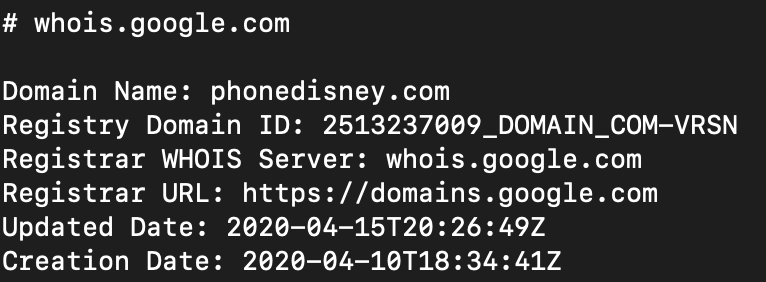
Beyond the message body, there were some overt red flags in the message headers. For example, the “From” header was spoofed to appear to be from a paypal email domain though the actual sender address was phonedisney[.]com, a domain name registered just days before the email.

Even more interesting, the message was blasted out to 180 different email addresses in the “To” header all alphabetically close to my own email address. How the attacker hasn’t discovered the use of BCC is beyond me.
The link within the email used a URL shortening service hosted on the domain meansfat[.]com. The site itself appears to be built on cPanel and using a URL shortener plugin or service that I’m not familiar with. Visiting a few modified versions of the original link path brings up an error indicating the shortener is communicating with an API of some sort. Searching a few of these strings on Google shows several other sites apparently using the same service.
The original link from the phish redirects to service-account[.]genuinelysmash[.]com with the URL path containing a randomly-generated and apparently unique key tied to the visitor and saved in a session cookie. The web server hosting the phish checks to see if the user tied to that key has already gone through every form in the phish and if they have, redirects them to the actual paypal.com website. This functionality can prevent a suspicious victim (or an analyst) from going back through the input forms a second time without clearing local session storage.
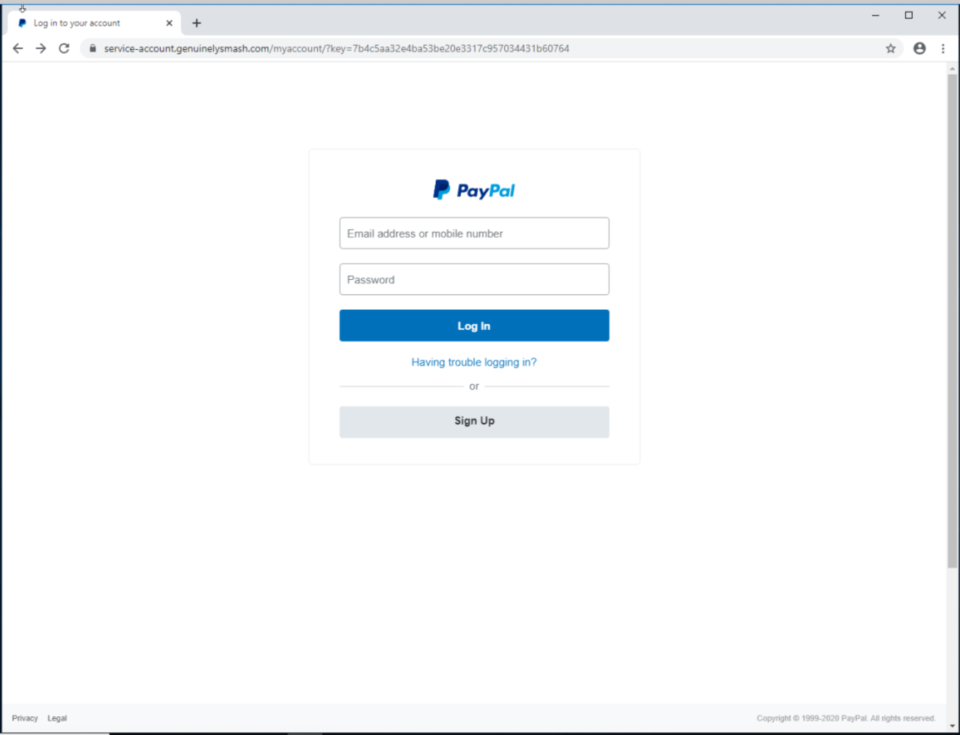
The first page for the phish is simple, designed to look like a PayPal login form. Both the “having trouble logging in” and “sign up” links go directly to legitimate PayPal addresses while the “login” link submits the entered credentials to the attacker-controlled server.
After submitting credentials, whether valid or invalid, the next page displays a notice that the victim’s account has been limited and provides a link to “Secure My Account.”
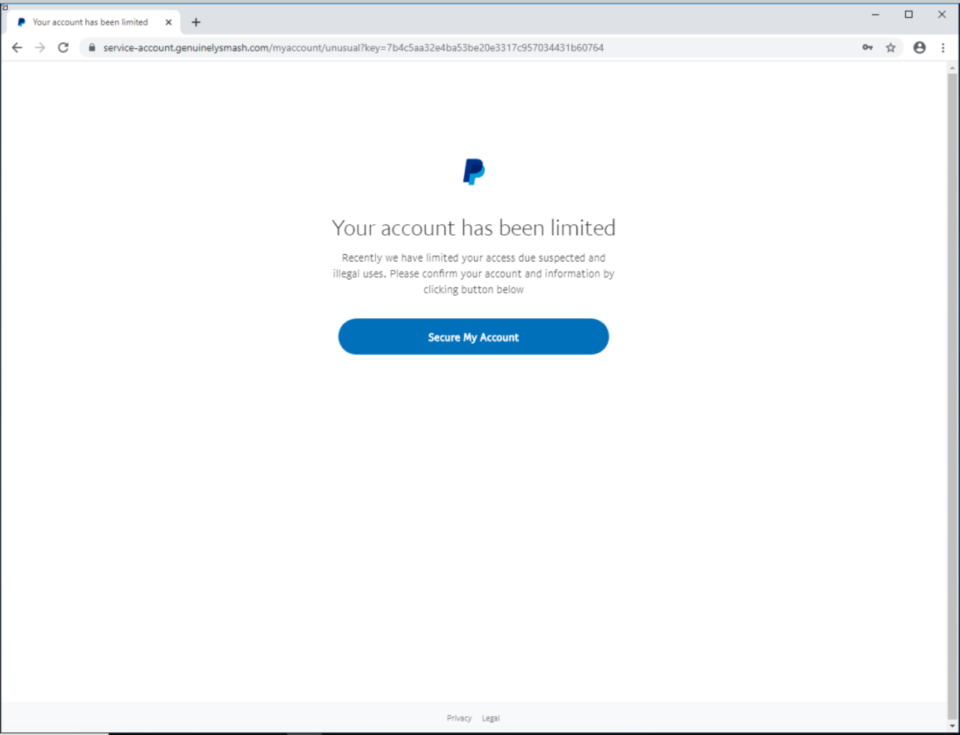
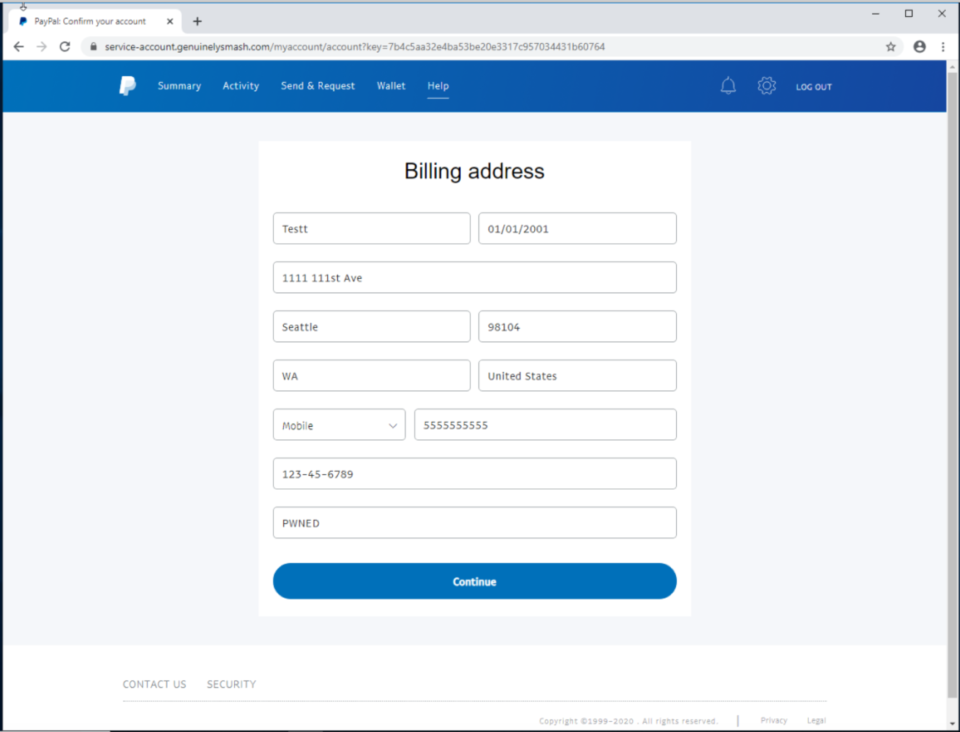
The next page requests information you might expect to unlock a PayPal account, or more accurately to take over someone’s identity, including name, address, phone number, social security number, and mother’s maiden name.”
The next page asks for credit card information. Interestingly, the page actually validates the credit card number using the Luhn algorithm and prevents entering in obviously fake numbers.
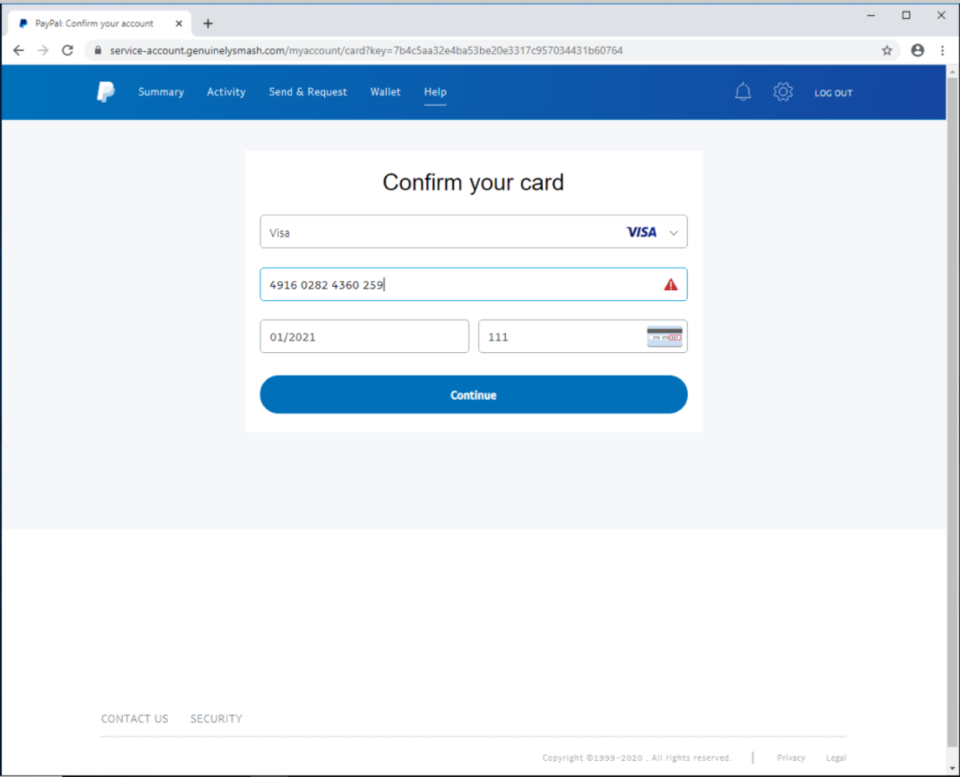
After entering in a “valid” credit card number (that is, one that passes the validity check), the page finally redirects the user to paypal.com/signin. Because of the cookies and session data, the victim cannot go back through the form without resetting their stored data for the site.
Overall, the phish used convincing looking assets to mimic a legitimate PayPal form. If the victim failed to notice the URL or any of the red flags in the email message itself, they could have fallen for this attack. Hopefully this shows the importance of treating every unsolicited email with suspicion. If you receive a call-to-action email from a sensitive service like PayPal, it’s always worth the extra effort to manually browse to the site itself instead of clicking on email links and, if in doubt, simply pick up the phone and call them.
The good news is, if you’re a WatchGuard customer, the DNSWatch service blocks all of the domains associated with this phish. With DNSWatch enabled, would-be victims of this phish are instead redirected to a short phishing-awareness training video or game to teach them how to spot the red flags.