Phishing Passwords With Maersk, Microsoft and Adobe
We recently discovered a sharp increase in a particular phishing scam while reviewing threat intelligence from the Firebox feed, our threat data from Firebox appliances around the world. Its primary targets were in Germany and Italy, but we also found some instances of the campaign in the Asian Pacific regions. Addressed with popular shipping companies like DHL and Maersk in both the TO field and the FROM field, this spam mimicked a financial invoice or statement to ultimately try and steal credentials.
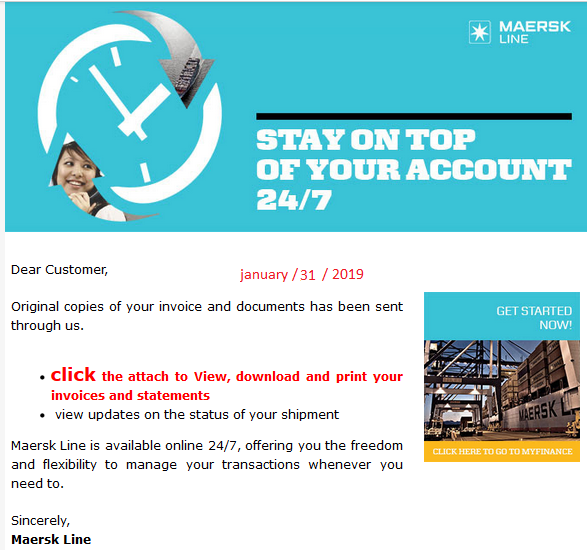
Let’s take a look at one of the samples we collected that masqueraded as an email from the shipping company Maersk. In the Maersk example, the email includes a picture that looks like a legitimate graphic from Maersk saying they have invoices for the recipient. Due to an error in the message’s formatting, the picture wasn’t always displayed in the body of the email when we viewed it, but perhaps other environments would see this picture correctly.
As for how they steal your password, the "PDF" attachment is actually an HTML file that loads a request for your Adobe ID email and password. If you fill out this form you don’t get to see the invoice though. Instead, the credentials are sent to a forum creation site jotfoormeu.com. We don’t suspect jotfoormeu.com are responsible for the attack. Likely, someone used their service to create a database for the phishing form submissions. The HTML attachment may have the same icon as a PDF in an email attachment because users often open PDF files with their favored web browser. If the user believes the request is from a PDF, they are more likely to fill out the form. At the time of this publication, jotfoormeu.com has removed the offending site.
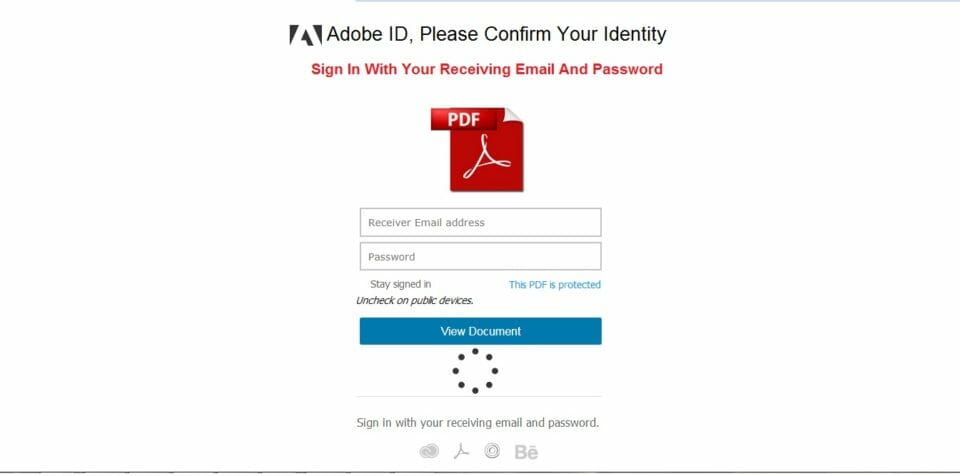
We have no reason to doubt https://jotformeu.com. But just because we trust the domain doesn’t mean we would trust everything on it, especially when unknown users may edit some pages. Attackers often use this trick to make add credibility to their phishing attacks. They especially like to use domains such as Google drive drive.google.com, Microsoft Azure Blob storage blob.core.windows.net or Microsoft OneDrive onedrive.live.com for this purpose.
We found another email campaign with a similar strategy from intelligence that we gathered through our DNSWatch service, another line of defense we have to these types of threats. This email sends the user to a web page crafted specifically for that user. The web request link includes the victim’s email address which then populates it into a form.
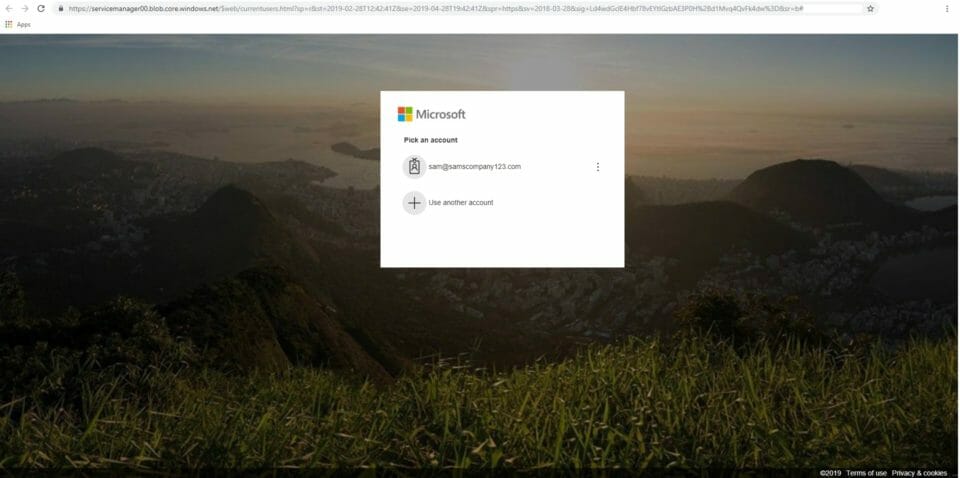
The email links to a windows domain web page, but instead of logging into your Microsoft account this page sends your login to the attacker. The web page creator recreated the Microsoft account login to match what the user would normally see when logging in.
Attackers are getting better at making their phishing attacks more believable. Users can’t rely on trusting the URL domain alone in web links received via email. If you click a link and are greeted by a login prompt, be sure to review how you got to the page. If there is any suspicion, don’t enter private information and get confirmation from the person who sent you there. Try calling the person or company directly to verify the link with the trusted person. We advise against sending an email replay in case the email account is compromised. Working through these steps may take a few more moments to verify the link but will save you in the long run when a malicious link does get sent to you or your company.